3.2 Finding Wireless Networks
Finding commercial wireless operators is easy ? very often you can identify the signage hanging outside a coffee house or on the walls of a hotel lobby. If not, when you power up your Windows XP computer equipped with a wireless card, it will display a list of wireless networks available. Examining the SSIDs (see Chapter 2 for more information on SSIDs) will often allow you to identify the network operator instantly.
This section focuses on how you can locate wireless networks when on the road. It is useful as a guide to help you look out for wireless networks in places such as hotels, coffee houses, or libraries.
3.2.1 Site Surveys
A simple way to discover wireless networks is to perform a site survey with your wireless network card. Doing a site survey is simple using either Windows XP's built-in capabilities or an advanced tool such as NetStumbler.
|
3.2.1.1 Windows XP
Windows XP's Wireless Zero Configuration feature automatically discovers the available wireless networks in the vicinity (this feature was illustrated in Chapter 2). However, Windows XP does not allow you to see detailed information about the wireless networks, such as the number of access points available or where they are located. If you need the additional information, you should use the more sophisticated (and free) NetStumbler program.
3.2.1.2 NetStumbler
NetStumbler is a free wireless network discovery tool (written by Marius Miner, a San Francisco Bay area software developer) that runs on Windows-based computers. You can use NetStumbler for site surveys, and it is also a useful tool for detecting unauthorized (rogue) access points.
|
You can download NetStumbler from http://www.netstumbler.com/. Running NetStumbler will display a list of wireless access points detected.
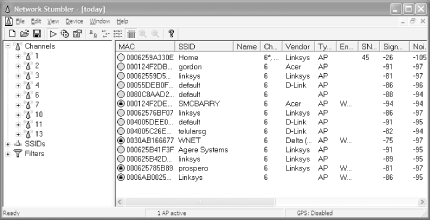
As shown in Figure 3-6, NetStumbler groups the access points detected based on channels and SSIDs. In this case, several access points were found running on channel 6. The MAC addresses of the access point are also displayed, together with other information such as vendor of the access point, whether WEP was used, signal-to-noise ratio, etc.
Figure 3-6. Using NetStumbler to detect wireless networks
|
NetStumbler also includes GPS support so you can connect a GPS receiver to your notebook and collect the location information for all the access points you find. Feeding the latitude and longitude information to mapping software (such as Microsoft MapPoint) lets you plot a map showing the locations of the access points. See Chapter 9 for more details on how to use NetStumbler with GPS.
Wardriving, Warwalking, and WarflyingA new term has been coined to describe the act of doing site surveys: Wardriving. Wardriving involves people using their notebook computers or Pocket PCs (equipped with wireless cards and GPS receivers) and driving around the city (or neighborhood) looking for the presence of wireless networks ? just for the fun or it, or to assess the security risks of wireless networks. With a GPS receiver, wardrivers can catalog the exact location of an access point. Besides Wardriving, people who performed site surveys via walking are Warwalking. Well, Warflying then seems obvious ? you fly on an airplane doing site surveys (for a great Warflying story, see Philip Windley's weblog at http://www.windley.com/2002/09/02.html). To see the Wardriving efforts around the world, go to google.com and type in "Wardriving". |
3.2.1.3 Determining wireless coverage with NetStumbler
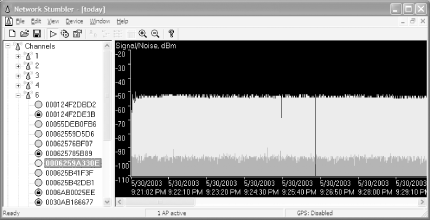
You can use NetStumbler to display a graph depicting the signal-to-noise ratio of a given access point (see Figure 3-7). This is useful for helping network administrators select the best place to position an access point for maximum coverage.
Figure 3-7. NetStumbler can display the signal-to-noise ratio for an access point.
Is Wardriving Legal?Before you do your own Wardriving, be sure to check with the local authorities to see if it is legal. As far as I know, Wardriving is not illegal in the U.S. However, in some countries, Wardriving may be an offense (in Singapore, it is classified under the Computer Misuse Act). One way to protect yourself when doing a Wardrive is to disable DHCP on your computer. Set a static IP address for your computer so that when you are associated with an access point, the network does not assign an IP address to you. Technically speaking, so long as you have not been assigned an IP address by the wireless network (even though you have been associated with the access point), you have not joined the network, and so you cannot be held liable for trespassing into the network. However, if you use DHCP for IP address, and an IP address is assigned to you, your MAC address will be logged by the network. Depending on local law, this may make you liable for your action. |
NetStumbler displays the graph in two colors: green and red. If the graph displays in mostly green, then it means that the signal quality is good. In general, always aim for lots of green in your graph.
To aim for maximum coverage, once an access point is mounted, install NetStumbler on a notebook computer and call up the graph. (To view this graph, drill down into the list of channels or SSIDs on the left and locate the access point you're interested in.) Watch the graph for a few seconds, and you'll see that it is charting the signal-to-noise ratio over time. So, if you walk around the site you wish to survey, you'll see the values change as the quality of coverage increases or decreases.
3.2.2 Warchalking
Warchalking is the practice of drawing symbols on walls to indicate a nearby wireless network. With the symbols, wireless users can identify the areas in which they can connect wirelessly to the Internet. Figure 3-8 shows the symbols used for Warchalking. The web site for Warchalking can be found at http://www.warchalking.org/.
Figure 3-8. Symbols used for Warchalking (from left to right: an open network, a closed network, and a network protected by WEP)
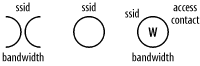
3.2.2.1 How Warchalking came about
In the 1930s during the Great Depression, many people left their homes to look elsewhere for jobs. Due to the poverty and scarcity of work, everywhere these people (often known as hobos) were often unwelcome in the new cities. As the story goes, a group flocked to Texas because it was rumored that there was a town there called El Paso where people were generous to beggars. To avoid trouble with the locals, the hobos devised a set of symbols to communicate with each other, so that they knew what to expect in the unfamiliar town. Figure 3-9 shows some original symbols devised by the hobos. Can you figure out what they mean?
Figure 3-9. Some symbols used by the hobos

Here are the answers:
You will be beaten
Man with gun
Safe camp
You can visit the following web sites for more symbols used by the hobos:
http://www.slackaction.com/signroll.htm
http://sedaliakatydepot.com/hobo.htm
Matt Jones, an Internet product designer, operates a web site (http://blackbeltjones.com) that serves primarily as the Londoner's online resume and portfolio. In June 2002, Jones combined the practice of using a sniffer tool to detect a wireless network (known as Wardriving or Warwalking) with that of the hobos' symbol to come up with the symbols for wireless networks (see Figure 3-8). Using these symbols, wireless users can then know if there is an available wireless network for their use. He was inspired by architecture students "chalking up the pavement" on his way to lunch. During a lunch, Jones and a friend, who had recently been discussing hobo signs with another friend, came up with the notion of Warchalking.
So the next time you see such a symbol on a wall or a sidewalk, you know that there is probably wireless access in the vicinity. Once you know about it, what can you do with it? To answer this question, you need to consider the legal and moral aspects of Warchalking.
3.2.3 Warchalking, Wardriving, and Legality
Warchalking or Wardriving for wireless networks are activities that are still legally debatable at the moment. First, drawing chalk marks on the wall may not constitute an offense (this depends on where you live: it is definitely considered an offense in Singapore if you do it without explicit permission!). But the real concern is when you discover a wireless network in a nearby home or business. Unlike wired networks, a wireless network has no clear boundary; hence, how does one define trespassing?
What happens if a wireless home network is not protected by any form of security (see Chapter 4) or MAC address filtering (see Chapter 5)? In this case, the wireless network is deemed to be "open" and may suggest that strangers are welcome to use the network. So, should you connect to the network? There is no clear answer.
At the time of this writing, a bill (House Bill 495) is moving through the New Hampshire state legislature that defines explicit boundaries for this. Under this bill, users would effectively be permitted to connect to open wireless networks. House Bill 495 recognizes that an open network is often a welcome mat. After all, if you were sitting in a public place such as a hotel lobby, airport, coffee shop, library, or conference venue and found an open access point, what would your first instinct be? Would you connect to the wireless network or find someone in order to ask permission? Most users would assume that the network was put there for their use. If passed, House Bill 495 would still protect wireless network operators by requiring them to take some steps to secure their network in order to be able to prosecute unauthorized users who connect to their network. If this sort of legislation becomes more common, then the legality of Warchalking and Wardriving will be easier to evaluate on a case-by-case basis.







