4.2 Virtual Private Networks
Imagine you are out of the office and need to access a printer or file server on the office network. Unless you dial in to the company's server, it is not possible for you to access the resources in the office. Moreover, using a dial-up line is not a cheap alternative (despite the slow speed), especially if you are overseas.
A Virtual Private Network (VPN) allows you to establish a secure, encrypted connection to the office's network, all through a public network such as the Internet. Using a VPN, you can work as though you are connected to your company's network.
There are two main types of VPN:
- User-to-Network
-
This type allows a client to use a VPN to connect to a secure network, such as a corporate intranet.
- Network-to-Network
-
This type connects two networks via a VPN connection. This effectively combines two disparate networks into one, eliminating the need for a Wide Area Network (WAN).
4.2.1 Tunneling
Tunneling is the process of encapsulating packets within other packets to protect their integrity and privacy during transit. A tunnel performs such tasks as encryption, authentication, packet forwarding, and masking of IP private addresses. Figure 4-1 shows a tunnel established between two computers through the Internet. Think of a tunnel as a private link between the two computers: whatever one sends to another is only visible to the other, even though it is sent through a public network like the Internet.
Figure 4-1. A tunnel established between two computers in a VPN

The following section discusses some tunneling protocols available for VPNs.
4.2.1.1 PPTP, L2TP, and IPSec
If you're curious about what goes on under the hood of a VPN, there are three protocols that you need to know: PPTP, L2TP, and IPSec:
- Point-to-Point Tunneling Protocol (PPTP)
-
This was designed by Microsoft (and other companies) to create a secure tunnel between two computers. PPTP provides authentication and encryption services, and encapsulates PPP packets within IP packets. It supports multiple Microsoft networking protocols such as LAN to LAN and dial-up connections. However, it is proprietary and the encryption is weak.
- Layer 2 Tunneling Protocol (L2TP)
-
This works like PPTP, except that it does not include encryption. L2TP was proposed by Cisco Systems, and like PPTP, supports multiple networking protocols.
- IPSec
-
This addresses the shortcomings of L2TP by providing encryption and authentication of IP packets. As such, L2TP is often used together with IPSec to provide a secure connection.
|
4.2.2 Setting Up a VPN Connection Between Two Computers
In the following sections, I illustrate how to set up a VPN host as well as a client using two Windows XP Professional systems.
4.2.2.1 On the host computer
Let's start with setting up the VPN host:
On the desktop, right-click on Network Connections.
Select "Create a new connection".
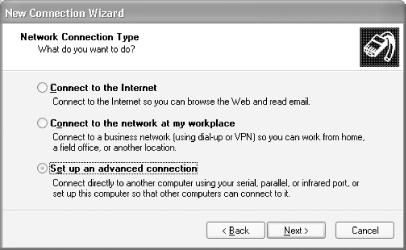
In the New Connection Wizard window, select "Set up an advanced connection" (see Figure 4-2). Click Next.
Figure 4-2. Choosing the network connection type
Select "Accept incoming connections". Click Next.
In the next window, you can select the other devices to accept the incoming connection. Click Next.
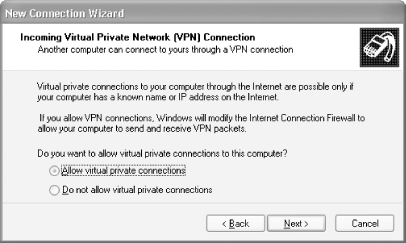
Select "Allow virtual private connections" and click Next (see Figure 4-3).
Figure 4-3. Allowing a VPN connection
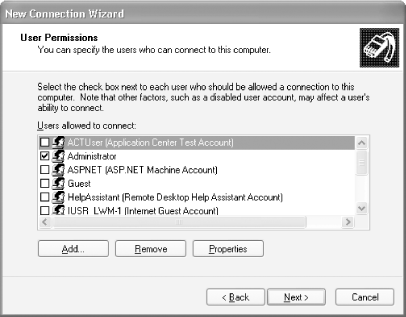
Select the users that you want to allow to connect to your computer using the VPN connection (see Figure 4-4). Click Next.
Figure 4-4. Granting access rights to users
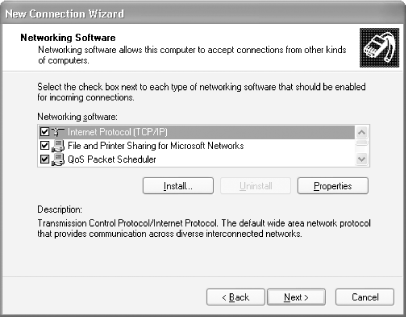
The next window allows you to install additional networking software for this connection (see Figure 4-5). Click on Next to go to the next screen.
Figure 4-5. Installing the networking software for the VPN connection
Click on Next and then Finish to complete the process.
4.2.2.2 On the client
To configure Windows XP to connect to a VPN:
On the desktop, right-click on Network Connections.
Select "Create a new connection".
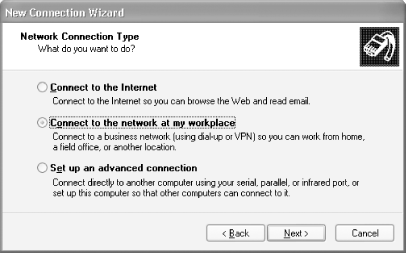
Select "Connect to the network at my workplace" (see Figure 4-6).
Figure 4-6. Selecting the network connection type
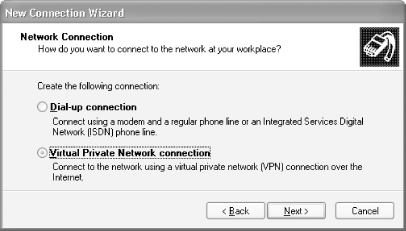
Select "Virtual Private Network connection" (see Figure 4-7). Click Next.
Figure 4-7. Selecting the network connection
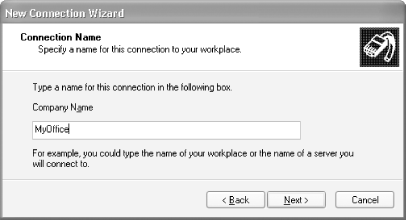
Enter a name for the VPN connection (see Figure 4-8). Click Next.
Figure 4-8. Giving your VPN connection a name
Select "Do not dial the initial connection". Click Next.
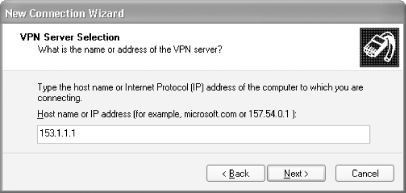
Enter the IP address of the VPN server (see Figure 4-9). Click Next.
Figure 4-9. Specifying the IP address of the VPN host
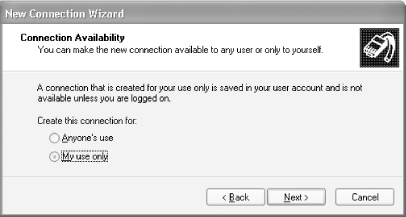
Select "My use only" (see Figure 4-10). Click Next.
Figure 4-10. Setting the connection availability
Turn on the "Add a shortcut to this connection to my desktop" checkbox. Click Finish.
That's it! When the process is completed, an icon is shown on the desktop (see Figure 4-11).
Figure 4-11. The icon for the VPN connection
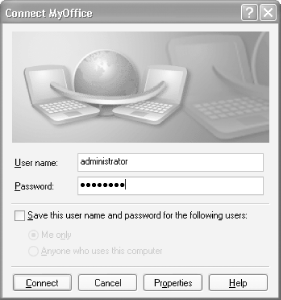
To connect to the VPN server, double-click on the icon and log in with your username information (see Figure 4-12). You can now work as though you are working on a computer in your office: most (if not all) of your network resources, such as file and print servers, will be accessible.
|
Figure 4-12. Logging in to a VPN connection
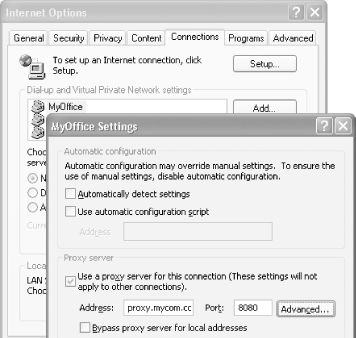
|
Figure 4-13. Setting a proxy server for a VPN connection
IPSec and PPTP Pass ThroughMost wireless routers support a feature known as "IPSec and PPTP pass through." What does it do? IPSec and PPTP are security protocols that provide authentication and encryption over the Internet. The "pass through" feature of the wireless router allows secure packets to flow through the router, but the router itself does not perform any authentication and encryption operation. IPSec works in two modes: transport and tunnel. Transport mode secures IP packets from source to destination, whereas tunnel mode puts an IP packet into another packet that is sent to the tunnel's endpoint. Only tunnel mode (ESP) IPSec can be passed through. |


 Internet Options
Internet Options 





