Wireless LAN
Wireless LAN
If this book had been written at the end of 2000, wireless LAN (WLAN) would most likely not appear here. After all, WLAN has only superficial similarity to cellular systems, does not truly support data mobility unless tunneling schemes like Mobile IP are applied to it, and was originally designed for in-building or campus rather than wide-area deployment. But since this time, WLAN has arguably become the fastest growing wireless access technology. We believe WLAN—combined with 2.5G and 3G systems—can potentially bring wireless data communication to a new level unachievable by 3G alone. For instance, a number of hotels and cafe chains in many parts of the world, such as Western Europe and North America (for example, Starbucks in the United States), already offer their guests the ability to use WLAN services. These businesses often partner with a cellular operator or wireline ISP, which manages the service for them, or asks the operator for permission to install their system at the premises based on a lease agreement or a revenue-sharing approach.
WLAN Technology
WLAN is a version of the existing wireline LAN standards (802.3 or Ethernet are two popular examples) defined by IEEE named 802.11b, after the number of engineers assigned to design it. WLAN relies on the RF technology and transmits data over the air, rather than via the wired connection required by other LAN technologies. In this section we briefly review the properties of the air interface used by WLAN. Networking and security are discussed in detail in Chapter 9.
Successful WLAN connection requires a client device, a wireless Network Interface Card (NIC), installed in the user's mobile device (such as laptop or PDA), and an access point (AP), the device that terminates the RF air interface and performs routing functions. A typical WLAN topology is shown in Figure 3.7.
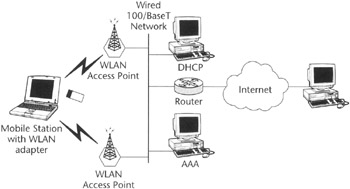 Figure 3.7: Typical WLAN topology.
Figure 3.7: Typical WLAN topology.
WLAN ranges can reach as high as 500 meters outdoors with no obstacles present. It is based on use of unlicensed Industrial, Scientific, and Medical (ISM) band, 2.4 to 2.5 MHz, which brings clear cost advantages to commercial WLAN deployments. On the downside a 2.4-MHz frequency is now also used by cordless telephones and Bluetooth devices and can potentially interfere with microwave ranges emission and vice versa.
The networks defined by 802.11 standards are capable of operating by using two types of transmission: Frequency Hopping Spread Spectrum (FHSS) and Direct Sequence Spread Spectrum, already mentioned in the CDMA2000 section. FHSS and DSSS radio interface technologies are mutually exclusive. FHSS is simpler to implement but is limited to 2 Mbps by FCC regulations (in the United States, where it was developed). For unlicensed band, DSSS is more complex but offers higher tolerance to interference and the bit rates as high as 11 Mbps, which is the highest-possible bit rate for the 802.11b standard. As such the DSSS version is largely the most popular and successful, and it is fast becoming the de facto standard.
One of the major limitations to wider deployment of WLANs for public and corporate use has been the lack of security or a standard way to secure the access and data confidentiality. The Wireline Equivalent Protocol (WEP) standard developed by IEEE tried to address this, but examples of failure made it unsuitable for the deployment in networks with strict security requirements. The interoperability between different WLAN standards is now being addressed by Wireless Ethernet Compatibility Alliance (WECA) initiative, which is now promoting not only interoperability among vendors (via the definition of the Wi-Fi trademark and logo) but is also closely monitoring security extension to WEP that IEEE is currently defining in the 802.11i committee. Typically, public WLAN deployments are based on the users authenticating at a portal, possibly after TCP redirection occurring as the user attempts to access any Web page. (An example is the captive portal approach, common to many broadband and now also wireless access systems; see Chapter 5 for more details.) After authentication, the point of attachment of the user to the Internet will allow the user access until further authentication is requested or an account needs to be topped up.







