Moving from Wireline to Wireless and Mobile
Moving from Wireline to Wireless and Mobile
We are now ready to apply the principles of VPN technology to the mobile wireless environment. In the previous section, we addressed main properties and design methodologies of VPN provided in various dial-up environments—including general circuit-switched wireless data systems. The rest of this chapter (and the book) focuses on VPN support over cellular wireless packet data networks such as those incorporated into 2.5G and 3G systems. We start the discussion with a terminology clarification, followed by the introduction of basic VPN mechanisms into main wireless packet-data-based systems. This should provide you with enough background and a good transition to the detailed discussions in Chapters 6 and 7.
Wireless versus Mobile
Let's first clear up confusion between the terms wireless and mobile, which are often inaccurately used to refer to specific network types. Many publications use the terms interchangeably. This is valid in certain areas and circumstances. However, it is our intention to use these two terms in a way as precise as possible. When applied to data networking, wireless and mobile mean two different things. Wireless networks can be mobile or nonmobile; for instance, microwave, Local Multipoint Distribution Services (LMDS), line-of-sight laser communication, or Bluetooth links are typically not supporting mobility and are simply used to provide fixed network access in the absence of wire or fiber. Mobile networks can be established over wireless as well as wired infrastructures as long as user mobility or network access service roaming are supported.
The term wireless means exactly what it says: something that can exist without wires. So, for example, wireless network should refer to a network built over the air (or in space in case of satellite communications). The term mobile refers to something that changes its location over time, so mobile host, for example, refers to a host whose position in the network changes over time relative to other hosts. Data mobility in turn can be defined as the ability of a host to change its point of attachment as well as its method of communication to the network while maintaining uninterrupted connectivity (recall the definition in Chapter 1). Systems capable of mobility support are therefore called mobile systems, and the end-user devices supporting mobility are called mobiles, mobile stations, and mobile nodes.
| Note |
Now as the definitions are established we should mention that in real life, mobile networks are almost always implemented in the wireless environments, while wireless networks can be both mobile and fixed. |
As is often the case, these definitions can be widely interpreted and may produce more questions than answers, including:
-
Would a change of IP address constitute a service interruption?
-
Can mobile data technology that spans only one wireless system be considered truly mobile?
-
Can mobility be supported and what would it be used for over fixed networks such as corporate LANs?
-
Is it important to be able to contact a user asynchronously anytime independently of his or her current location?
-
Is mobility to be supported on physical, link, or network layers?
The rest of this book could be devoted to the discussion of this fascinating topic, but we need to continue on with the topic at hand. We will try to resolve as many questions arising from these definitions as we possibly can, time and space permitting.
Significance of VPN in the Wireless Packet Data Environment
Recall from Chapter 4 that cellular packet data technology is based on a dynamic tunneling concept in which sequential tunnels are created and torn down between the foreign networks visited by the mobile station and its home network. The complexity of the task of providing VPN service in such environment lies in somehow combining this technique with fixed or "quasi-fixed" tunneling topology required on the wireline side to provide mobile users with secure private network access. This task becomes especially complex when compulsory VPN service is required. In this case wireless operator must possess the equipment capable of supporting not only dynamic tunneling but also dynamic tunnel switching between dynamic and fixed portions of their infrastructure. Figure 5.8 provides a sample architecture illustrating this requirement. In the case of voluntary VPN, this task is simplified a bit, since end-to-end tunneling is generally unaware of the underlying infrastructures as long as the endpoints' IP address stays fixed. This requirement should be addressed by data mobility schemes such as those used in GPRS or CDMA2000.
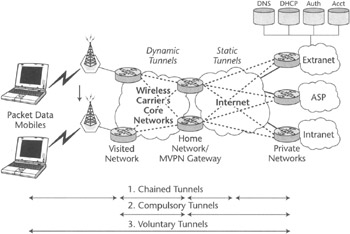 Figure 5.8: VPN in wireless packet data environments.
Figure 5.8: VPN in wireless packet data environments.
Let's now analyze why MVPN in packet data systems is necessary. Supporting MVPN requires complex tunnel-switching-capable network nodes and mobile devices. In wireless packet data, the mobile stations are enabled by the network layer mechanisms to change their location and point of attachment to the network while maintaining the connection to their home network. Often the mobile station roams onto foreign networks supported by operators other than its original carrier. While roaming, the MS keeps its connectivity to its home network through the use of tunneling schemes supporting mobility such as GPRS in GSM and UMTS systems or Mobile IP in CDMA2000 system. In such an environment, it is impractical to establish any kind of permanent dial-up-style circuit connection between the MS and private network. That would actually defeat the purpose of migration from circuit- to packet-switched environment.
The best—and arguably the only—technology for private network access in such an environment is MVPN, either compulsory or voluntary, based on mobility-enabled tunneling protocols at least over some leg of the end-to-end data path. Thus, MVPN in packet data systems would not just be an access option—as it is in wireline networking, along with other types of access such as direct dial-up, leased lines, ATM, and Frame Relay—but a necessity. Having summarized the importance of MVPNs, we can now take a more detailed view at main MVPN types.
Voluntary MVPN
MVPN based on voluntary tunneling is implemented almost exactly the same as wireline VPN. As with wireline VPN, it's important to consider whether the service provider uses public or private IP addressing schemes and what IP address translation mechanisms (if necessary) are used when private addressing schemes are in place. Another consideration, which is unique to the wireless environment, is the stability of the IP address assigned to a mobile device. Generally, tunneling protocols supporting mobility in modern packet data systems help to keep IP addresses assigned to mobile stations constant. Some even allow for permanent fixed IP addresses to be preprovisioned in the end user devices—a perfect condition for stable end-to-end tunnels forming a foundation for reliable voluntary VPN.
However, in some wireless systems certain access modes provide only limited IP mobility. Remote users and IT managers must take this into consideration when ordering wireless service with the intention to use it for voluntary VPN. For example, in CDMA2000, Simple IP access mode provides user mobility only within boundaries of the same PDSN/FA (more on this in Chapter 7). Here end-to-end tunnels cannot be kept alive when changing the serving PDSN, since the packet data bearer needs to be reestablished toward the new PDSN and the MS must acquire a new IP address. This also requires the VPN client on the MS to restart the session with the new IP address. That might not appear to be a significant problem given that a typical PDSN usually may span areas of several hundred square kilometers, but for mobile users traveling along the boundaries between two different PDSNs, this might present a real challenge. Using a compulsory VPN technology with a Simple IP access mode would not ameliorate the situation either, since the end-to-end connectivity is lost and a new remote network access procedure needs to be restarted each time a new PDSN is visited. This can be changed if a Mobile IP-based access mode is used. Mobile IP access mode can be used two different ways. One provides direct access to the network the end user needs to access, while providing mobility. The other way is plain but uninterrupted access to the Internet offered by the mobile operator, in which the user can choose to voluntarily set up an end-to-end tunnel using a common VPN client.
Another interesting aspect of voluntary MVPN access to networks over wireless links is its moneymaking properties from an operator perspective. It is somewhat likely that consumer access to the Internet will be differentiated from the Internet access service that allows a customer to use a VPN client, since the potential revenues per subscriber from consumer access are likely not to be the same as those from business customers accessing their corporate network using a VPN client. For this reason, wireless carriers need to offer distinct access points to the Internet for these two classes of users. The network access attributes will likely be different at these access points, such as public/private IP address, NAT with or without the NAT traversal feature, firewalling, and virus filtering. From an operational point of view, this may be enforced at contract signup time via the appropriate definition of the subscribed services.
Compulsory MVPN
As mentioned at the beginning of this section, compulsory MVPN is based on the same principles as its wireline counterpart. However, while wireline compulsory VPN is based on a single fixed tunnel (or more rarely on a set of fixed concatenated tunnels), the MVPN implemented in a wireless environment is different and is based on a combination of dynamic tunnels supporting mobility and fixed tunnels on the wireline side. To achieve this functionality, referred to as dynamic tunneling switching, wireless operators must deploy intelligent infrastructure elements capable of supporting a variety of tunneling techniques.
Tunnel switching is a fairly recent concept, initially introduced by wire-line data communication vendors competing in the IP services market. Devices supporting tunnel switching capability must be able to route user data through sets of tunnels by terminating the tunnels carrying the incoming data and originating the tunnels encapsulating the outgoing data. This is usually based on a set of policies provisioned in the network or individual devices by the wireless carrier on the business customer's behalf. Alternatively, instead of using tunnels, a private network of leased physical lines or ATM or Frame Relay VCs between the wireless operator's access gateway and the enterprise could be deployed. However, the leased line approach would eliminate VPN cost advantage and ease of management and provisioning, which is especially important in the mobile environment.
Compulsory Mobile VPN may be implemented differently depending on the allowed mobility pattern. For instance, it is possible to build a compulsory service in CDMA2000 Simple IP access mode given that user mobility would be limited. This is often the case for business users accessing corporate networks from hot spots like airport lounges or hotel rooms. This service requires dynamic establishment of an L2TP tunnel between the serving PDSN and the customer network (see Chapter 7 for details on how this is done). In fact, it is not possible to allocate a particular PDSN where a static compulsory tunnel between the corporation and the wireless carrier can be defined, since the subscriber may be using any PDSN serving the radio access network where he or she is located.
Architecturally the compulsory service may be implemented in CDMA2000 or GPRS systems by enabling the device that is a termination point of the protocols supporting mobility, such as PDSN or HA and GGSN, respectively, to be also the originating point of traffic exchange with customer networks via a set of fixed tunnels.
The compulsory model does not fit well with the currently commercially deployed WLAN access mode, since current access control methods require the user to first acquire an IP address and then authenticate at a portal to gain network access. This requires the use of a DHCP-assigned IP address that belongs not to the corporation, but to the network that the subscriber is visiting. Therefore, it will not be possible to admit the user to the corporate network. This would create many security problems, since source-address-based firewalling and packet-filtering rules would be no longer possible, making this unacceptable for corporate IT departments. One way out of this situation is to use Mobile IP-based mobility, since Mobile IP comes with its own access control and the MS can be assigned an address belonging to the corporate access network. While it is hard to judge which of the myriad MVPN options will become the standard, the final outcome will be—as always—shaped by the market and the needs of real-life customers.







