Hub-Based Networks
Nowadays hubs are inexpensive devices that you can use in your network to provide port or connection sharing for your users. For example, you might use a hub in your home to share an Internet connection among multiple computers or in your office to share a switch port with multiple users grouped together in a room.
Hubs in a Home Network
Suppose that you have a computer at home, with a printer, and are using a cable modem or digital subscriber line (DSL) for access to the Internet, as illustrated in Figure 12-1.
Figure 12-1. Home Computer, Modem, and Internet
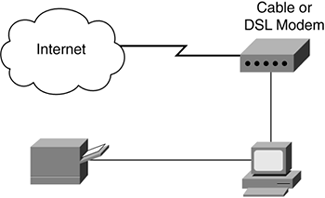
The network shown in Figure 12-1 is a basic network configuration typical for home use. It uses the minimum number of devices to provide you a connection to the Internet: the computer, the cable/DSL modem, and the Internet access line itself.
Now suppose that your office issues you a laptop, and you want to be able to telecommute (work from home) at times. Because you already have an Internet connection to your home, you might want to share that connection, rather than install a second connection for your laptop; a small hub enables you share this connection, as illustrated in Figure 12-2.
Figure 12-2. Hub-Based Network
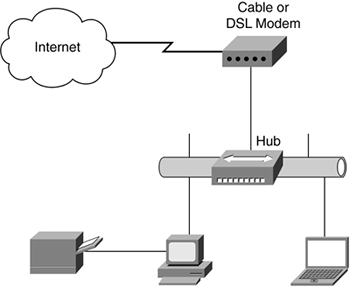
With the addition of a small hub from your local computer or office-supply store, you can share your dedicated Internet connection with multiple computers, and you are limited only by the number of ports on the hub, such as a four- or eight-port hub.
When you look at the network illustrated in Figure 12-2, it is obvious that there is little provided in the way of network security. Okay, let's be blunt: There is no network security in this architecture! Recognizing this lack of security, it is advisable to install a software-based firewall on each device (computer) connected to the hub, because as you might recall, the hub is a multiport repeater and takes whatever signal is received on one port and repeats it out all ports?not the most secure model.
It is worth mentioning that within 24 months of the time of writing this book, it is expected that all hub-component vendors will stop making hubs and make only low-end switches. With this said, it would be perfectly reasonable for you to go to your local computer store and buy a small low-end switch rather than a hub for this same scenario. The purpose here is to show where a hub might be used today.
Hubs in an Office Network
Suppose you share an office with a few people, each in his or her own workspace, with the exception of a control desk with multiple computers, as illustrated in Figure 12-3.
Figure 12-3. Control Desk and Cubicles
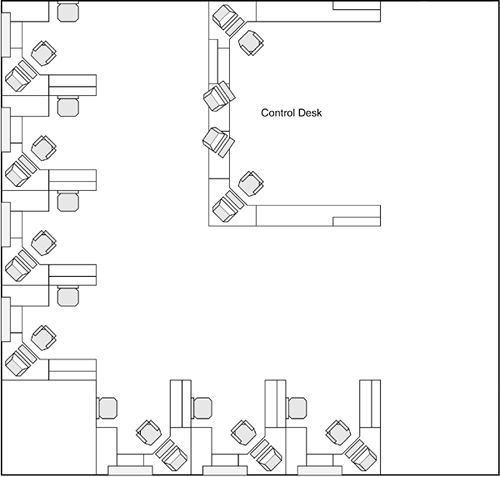
Figure 12-3 shows a control desk with four computers and seven cubicles, each with its own computer. In this setup, 11 computers are sharing a single network connection, such as to the Internet. However, you might have recognized a pattern in that the number of ports on a hub, bridge, or switch is a multiple of two. (This chapter doesn't go into the specifics because such specifics are beyond the scope of this book.) Suffice it to say that the number of ports available on a hub, bridge, or switch are numbered in this way: 4-ports, 8-ports, 16-ports, 24-ports, and so on. However, the office pictured in Figure 12-3 needs 11 ports. So although it might be easy to say, "Drop in a 16-port hub and call it a day," life is not that easy.
note
Using hubs is not the only possible solution for this scenario. This chapter presents another possible solution, using switches, in subsequent sections. |
You could use both an eight- and four-port hub, creating a daisy chain, as illustrated in Figure 12-4. This architecture enables you to share a port on the eight-port hub with the four-port hub, which has the three control-desk computers connected to it. Keep in mind that one of the ports of your four-port hub is being used to provide the uplink to the eight-port hub, so you have only three usable ports for workstations available on the four-port hub.
Figure 12-4. Small Hub-Based Daisy Chain
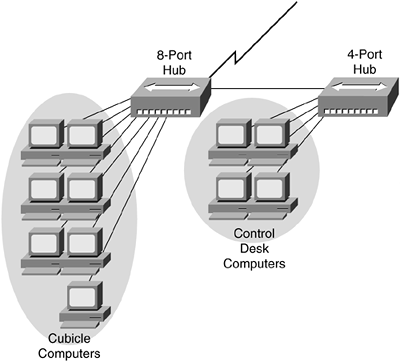
Recall from Chapter 5, "Ethernet LANs," that hubs create both a single broadcast and collision domain, meaning that all devices connected via the hubs can recognize traffic from all other devices. In a small network, this is not significant; with every device you add to the network, however, you are adding more traffic that all other devices must contend with for bandwidth, as illustrated in Figure 12-5.
Figure 12-5. Large Hub-Based Daisy Chain
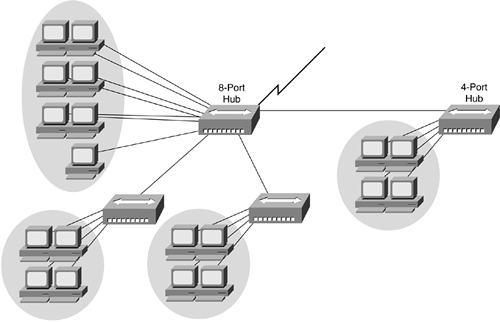
Although the network architecture shown in Figure 12-5 might work, be aware of the single collision domain you've created, and the subsequent complaints from your users: "The network is slow." If your users are using the network for e-mail and web surfing, the issue of the large collision domain probably won't arise. If your users are using more network-intensive applications, such as computer-assisted design/manufacturing (CAD/CAM) applications, however, consider segmenting your network, with switches alone, for example, or switches with virtual local-area networks (VLANs) configured.






