OSI Model
This general overview of the Open System Interconnection (OSI) model lays the foundation for the rest of this book, but do not consider it exhaustive. The OSI model defines a networking framework in seven layers. Control of the data passes from one layer to the next, starting at the sending station's application layer, and then working down through the model, to the bottom layer. Control of the data then passes across the physical connection between each station along the path and then back up the model layers to the top layer at the receiving (destination) station. Figure 2-1 shows this process.
Figure 2-1. OSI Model Sending and Receiving
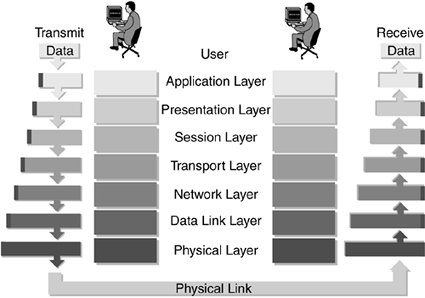
In the networking environment, the OSI is the universal model and is made up of seven layers, each layer providing a service to the layer above it and dependent on the layer below. These seven layers are as follows:
Layer 7? Application
Layer 6? Presentation
Layer 5? Session
Layer 4? Transport
Layer 3? Network
Layer 2? Data link
Layer 1? Physical
Layers 1 through 4 are referred to as the lower layers, and Layers 5 through 7 are referred to as the upper layers. Each layer performs a specific function in itself and provides a service to the layer above it. For example, Layer 2 (data link) depends on services provided to it by Layer 1 (physical) and provides services to the layer above it, Layer 3 (network). Each layer of the OSI model performs a specific function, as discussed in more detail in the following sections, starting with the uppermost?Layer 7, the application layer.
Layer 7?Application Layer
The application layer is the user-interaction layer, enabling the software and end-user processes. Everything at this layer is application specific. For example, a web browser application for surfing the Internet would user this layer. The application layer provides application services for file transfers, e-mail, and other network-based software services, such as your web browser or e-mail software.
Layer 6?Presentation Layer
The presentation layer provides for data representation to the user, such as a document (.doc) or spreadsheet (.xls). The presentation layer also "translates" the user data into a format that can be carried by the network, such as the segments and packets required at the lower layers. The presentation layer converts your data into a form that the application layer can accept, such as converting a string of data into a recognizable file format, such as .doc (word processing document) or .jpeg (graphics format). The presentation layer formats and encrypts data (when required by the user's application) to be sent across the network.
note
Encryption is the process by which original data, or plaintext, is converted into an unreadable format, or ciphertext, that can be read by only its intended recipient. The encryption process is based on a mathematical algorithm, or code, to create the ciphertext. |
Layer 5?Session Layer
The session layer establishes, manages, and terminates virtual communications connections between applications. In other words, the session layer starts and stops communication sessions between network devices. When you place a telephone call, for example, you are establishing a communication session with another person. When you are finished with the call, you hang up the telephone, which terminates the session.
Layer 4?Transport Layer
The transport layer provides data transfer between end systems and is responsible for end-to-end error recovery and flow control. Flow control ensures complete data transfer and provides transparent checking for data that might have been dropped along the way from sender to receiver. Error recovery retrieves lost data if it is dropped or suffers from errors while in transit from source to destination.
Layer 3?Network Layer
The network layer provides the routing technologies, creating a forwarding table or a logical path between the source and destination. These logical paths are known as virtual circuits and are considered to be point-to-point network connections. Routing and forwarding are functions of the network layer. Network addressing, error handling, congestion control, and packet sequencing are all functions of the network layer.
note
The network layer is where routers and routing protocols operate. |
note
Error handling is the response to an error that advises either the user or another process that an error has occurred. Error correction is the action taken to correct the error. Examples of error correction methods include resending the data or the application, or "figuring out" the corrupted data by the use of a checksum (a mathematical operation based on the number of 1s and 0s in the data). |
Layer 2?Data Link Layer
At the data link layer, data packets are placed into frames for subsequent transmission across the network. The data link layer provides the transmission protocol knowledge and management and handles physical layer errors, flow control, and frame synchronization.
The data link layer is divided into two smaller sublayers: the Media Access Control (MAC) layer and the logical link control (LLC) layer. The MAC sublayer controls how a computer on the network gains access to the data and permission to transmit it. The LLC layer controls frame synchronization, flow control, and error checking.
Think of the MAC and LLC sublayers as the pilot and copilot of an aircraft. The MAC sublayer prepares the frame for physical transmission, much as the pilot focuses on the physical aspects of flying the aircraft. The LLC sublayer is concerned with the logical aspects of the transmission, not with the physical aspects of the transmission. The LLC layer acts like the copilot, who focuses on navigation, leaving the physical aspects of flying to the pilot.
note
Bridges and traditional switches operate at the data link layer. |
Layer 1?Physical Layer
The physical layer carries the bit stream through the network. The bit stream can be carried as an electrical, light, or radio signal. This layer provides the hardware means of sending and receiving data on a carrier, including defining the cables, cards, and physical aspects. Gigabit Ethernet, wireless, dense wavelength-division multiplexing (DWDM), Synchronous Optical Network (SONET), Electronic Industries Alliance/Telecommunications Industry Alliance 232 (EIA/TIA-232; formerly RS-232), and Asynchronous Transfer Mode (ATM) are all protocols with physical layer components.
Table 2-1 outlines the signal type carried by each medium.
Medium | Signal Type |
|---|---|
Fiber optic | Light |
Copper | Electrical |
Air | Wireless, radio |
note
Hubs and repeaters operate at the physical layer. |






