Network Security Basic Rules
You need to keep in mind several basic rules when setting up secure Layer 2 switched VLANs:
VLANs should be set up in such a way that the VLAN clearly separates the network's various logical components from each other, in turn segregating logical workgroups. This is the first step toward segregating those portions of your network that need more security from portions that need less.
If some switch ports are not being used, it is best practice to disable these ports and assign them to a special VLAN that collects these unused ports. This special VLAN should have no Layer 3 connectivity, such as to a router or other Layer 3 device capable of switching.
Although devices in a particular VLAN cannot access devices in another VLAN unless a trunking or routing mechanism is available, VLANs should not be used as the single mechanism for providing network security. VLAN protocols are not designed with network security as the primary goal, and because of this VLAN protocols can be compromised rather easily. Unfortunately, VLANs enable loopholes into the network. Because VLAN protocols are not security conscious, you should use other mechanisms, such as those discussed in the next sections, to secure the network.
Because VLANs lack security, devices at different security levels should be isolated on physically separate Layer 2 devices. For example, having the same switch chassis on both the inside and outside of a firewall is not recommended, as illustrated in Figure 9-2.
Figure 9-2. Public and Private VLAN Behind the Same Firewall
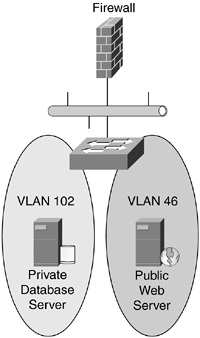
Putting both the public (VLAN 46) and private (VLAN 102) VLANs on the same switch, behind the firewall, is not a good idea. The VLAN separation does not provide enough security for your private information, such as a corporate database. This is not recommended because the management of the switch is more easily compromised by having a public VLAN. In addition, this is not recommended because a simple misconfiguration or incorrect cabling could expose the management interface of the switch. Figure 9-3 illustrates the solution to this type of scenario.
Figure 9-3. Public and Private VLANs Separated by Two Switches
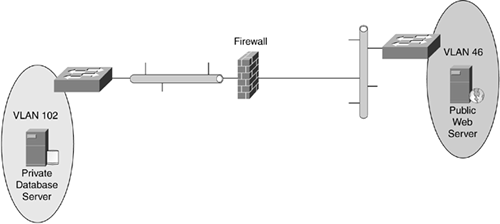
Two separate switches should be used for the secure and nonsecure sides of the firewall: one switch on the public side of the firewall and one switch on the private side of the firewall.
note
High-end switches can perform firewall functions without using an external firewall device. |
An important point to remember is that you need to make sure VLAN trunking in your network does not become a security risk in the network switching environment. VLAN trunks should not use switch port numbers that belong to the native VLAN. Because the native VLAN is a VLAN that is not associated explicitly to a trunk link, the native VLAN enables network packets from the trunk port to reach other ports located in the same native VLAN, as illustrated in Figure 9-4.
Figure 9-4. When VLAN Trunking Goes Awry
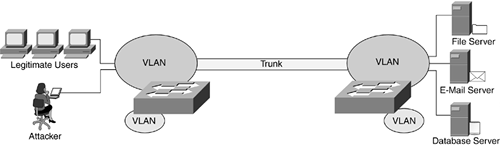
The VLAN trunk between the two switches in Figure 9-4 is part of an active VLAN. Therefore, if an attacker gains access to that VLAN, that same person now has access to all network resources inside that VLAN, such as user workstations or servers. (Aren't network attackers annoying?)
Switch ports that do not require trunking should have trunking disabled because, as illustrated in Figure 9-4, an attacker can use this trunking to hop from one VLAN to another. The attacker can do this by pretending to be another switch looking to establish a VLAN trunk with an active switch. This impersonation of a switch enables the attacker's machine to become a part of all the VLANs on the switch being attacked.
It's a good idea to use dedicated VLAN IDs for all VLAN trunks rather than using VLAN IDs that are also being used for nontrunking ports. If you don't use separate VLAN IDs, you enable an attacker to be part of a trunking VLAN pretty easily and then in turn use trunking to hop on to other VLANs as well. In other words, your attacker just bribed Patches with a steak.
note
Layer 3 interfaces between switches provide additional access control. |
If one of your network users does not want his workstation to be tampered with, that user must control the physical access to that workstation, such as powering off the computer at the end of the day. In addition, it is important for any network administrator or manager to use all the proven security tools available for his or her specific platforms. These security tools range from the very basic configuration of system passwords, IP permit filters, and login banners, to more advanced tools such as Remote Authentication Dial-In User Service (RADIUS), Terminal Access Controller Access Control System Plus (TACACS+), and intrusion detection systems (IDSs).
Only after the basic security components are in place is it possible to turn attention to some of the more sophisticated security details, such as the use of port security or VLANs in your network, which are discussed in the following sections.






