Introducing Ethernet
Ethernet's origins begin with the Aloha Radio System, a packet satellite system developed at the University of Hawaii. Beginning in the late 1960s, the Aloha Radio System was designed to facilitate communication between the university's IBM mainframe, located on the island of Oahu, with card readers located among different islands and ships at sea. Work on the Aloha Radio System proved to be the foundation for most modern packet broadcast systems including Ethernet.
Ethernet as it is known today took shape in the 1970s as a research project at Xerox's Palo Alto Research Center. Ethernet was eventually standardized by Digital, Intel, and Xerox in 1979, and harmonized with the international standard, IEEE 802.3, in 1982.
Modern LAN switched networks are based on the theory and operation of Ethernet. This section discusses the basic theory and operation of Ethernet. The initial version of Ethernet operated with a speed of 3 Mbps and used an algorithm called carrier sense multiple access collision detect (CSMA/CD) protocol to determine when a device could use the network. Ethernet is currently available in 10 Mbps, 100 Mbps, 1000 Mbps (1 Gbps), and 10000 Mbps (10 Gbps).
Types of Ethernet
As mentioned earlier, Ethernet provides various data rates with different physical layouts. A variety of Ethernet types have come and gone over the years, such as the following:
10BASE5 (Thicknet)
10BASE2 (Thinnet)
10BASE-FL
10BASE-T
In the mid 1990s, 100BASE-T (unshielded twisted-pair [UTP]) and 100BASE-FX (using fiber) were ubiquitous in the enterprise network, and they still are. Since the start of the millennium, enterprise networks have actively implemented Gigabit Ethernet, 1000BASE-T, in their network. The push for today is 10 Gbps in the core of the enterprise network.
Transmission Media
The more common transmission media are twisted pair and fiber optics. Coaxial cable is mentioned in this section for historical purpose. Categories defined under twisted pair support transmission over various distances and data rates. The most common UTP cable in the enterprise network is Category 5, which supports 100 Mbps and 1000 Mbps rates.
Ethernet over Twisted-Pair Cabling
Ethernet technology standards are the responsibility of the IEEE 802.3 working group. This group is responsible for evaluating and eventually approving Ethernet specifications as new Ethernet technologies are developed such as Gigabit and 10Gigabit Ethernet. Although this group defines the standards for Ethernet, it looks to other established standards organizations to define the specifications for physical cabling and connectors. These organizations include the American National Standards Institute (ANSI), Engineering Industry Association (EIA), and Telecommunications Industry Association (TIA). The TIA/EIA published specifications for twisted-pair cabling are found in the TIA/EIA-568-B specification document.
The more common forms of cabling are unshielded twisted-pair (UTP) and optical fiber. Twisted pair cable comes in a variety of forms. The most common categories in today's networks are the following:
Category 3
Category 5
Category 5E
Category 6
The categories represent the certification of the radio frequency capability of the cabling.
Category 3 was initially designed as voice grade cable and is capable of handling transmissions using up to 16 MHz. Category 5 is capable of handling transmissions up to 100 MHz. Category 5E is an improved version of Category 5; while still limited to 100 MHz, Category 5E defines performance parameters sufficient to support 1000BASE-T operation.
Category 6 provides the best possible performance specification for UTP cabling. Category 6 specifies much stricter requirements for cabling than Category 5 and 5E. The frequency range of Category 6 extends to 250 MHz, in contrast to Category 5 and 5E's 100 MHz. While new cabling installations typically install Category 5E or 6 cabling, Category 5 cabling can be utilized for 1000BASE-T applications. With few exceptions, if 100 Mbps Ethernet is operating without issues up to 100 meters on a Category 5 cable plant, 1000BASE-T will operate as well.
Although 10 Mbps and 100 Mbps Ethernet often use two pairs (pins 1, 2, 3, and 6) of twisted-pair cabling, Gigabit Ethernet over twisted pair uses all four pairs of wiring in the twisted-pair cable.
Even if the actual twisted pair is rated a specific category, it does not imply that a cabling infrastructure properly supports the category specification end-to-end. Installation and accessories (such as patch panels and wall plates) must meet the standard as well. Cable plants should be certified from end-to-end. When installing a cabling infrastructure, the installer should be able to use specialized equipment to verify the specifications of the cabling system from end-to-end.
Ethernet over Fiber Optics
Two major types of fiber used in Ethernet networks are multimode and single mode. Multimode fiber (MMF) is used for short haul applications (up to 2000 m). Examples include campus or building networks. MMF is usually driven by LED or low-power laser-based equipment. Single mode fiber (SMF) is used for longer haul applications (up to 10 km) and the equipment is laser based. SMF is generally used in metropolitan-area networks or carrier networks.
Table 1-1 compares Ethernet types over different transmission media.
Ethernet Type | Media Type | Distance Limitations (meters) | Speed (megabits) | Data Encoding |
|---|---|---|---|---|
10BASE-T | UTP Category 3 or better | 100 | 10 | Manchester |
10BASE-FX ? MMF | MMF | 2000 | 10 | Manchester |
100BASE-TX | UTP Category 5 or better | 100 | 100 | 4B/5B |
100BASE-FX ? MMF | MMF | 2000 | 100 | 4B/5B |
100BASE-FX ? SMF | SMF | 10000 | 100 | 4B/5B |
1000BASE-SX | MMF | 2000 | 1000 | 8B/10B |
1000BASE-LX | SMF | 5000[*] | 1000 | 8B/10B |
1000BASE-T | UTP Category 5 or better | 100 | 1000 | PAM 5x5 |
[*] The Cisco implementation of 1000BASE-LX doubles this distance over the standard to 10,000 meters
Ethernet over Coax Cabling
The use of coax cable for LANs is virtually nonexistent. One might run into it in an old abandoned building. Ethernet's eventual support of twisted pair cabling in a star topology virtually ended the use of coaxial cabling for Ethernet. Keep in mind that coax cable was not cheap either. Two major types of coax were used: thinnet (also called cheapernet) and thicknet. Thinnet uses 50 ohm coaxi cable (RG-58 A/U) with a maximum length of 185 meters when used for Ethernet. This cable is thinner and more flexible than thicknet, which is also 50 ohm coax cable. It is packaged and insulated differently than thinnet. It requires a specialized tool, a vampire tap, to pierce into and has a maximum length of 500 meters for Ethernet. The vampire tap was used to pierce the outer shielding of the cable, creating an electrical connection between the device and the shared media. Traditionally, thicknet was used as a backbone technology because of its additional shielding. Both thinnet and thicknet are virtually extinct in production networks today.
Ethernet Cross-Over Cabling
Network devices can be categorized as either data circuit equipment (DCE) or data terminating equipment (DTE). DCE equipment connects to DTE equipment, similar to the male and female end of a garden hose. DCE equipment usually is a type of concentrator or repeater, like a hub. DTE equipment is usually equipment that generates traffic, like a workstation or host.
Sometimes, it is necessary to connect like equipment. Connecting like devices can be accomplished by altering the twisted-pair media, and taking transmit and receive wires and reversing them. This is commonly called a "cross-over" cable. Figure 1-2 shows an RJ-45 connector with its pinouts. Pins 4, 5, 7, and 8 are not used.
Figure 1-2. Crossover Pinouts
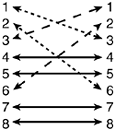
The pinouts are a bit different in a Gigabit scenario because all the pins are used. In addition to the pinouts for 10 Mbps/100 Mbps aforementioned, two additional changes are necessary: pin 4 to 7, and 5 to 8.
A crossover cable can link DCE to DCE, and DTE to DTE. The exception to connecting like devices is that some devices are manufactured to be connected together. An example would be that some hubs and switches have an uplink or Media Dependent Interface (MDI) port. There is typically a selector that allows the user to toggle between MDI and MDI-X (X for crossover), with MDI-X intentionally reversing the pin out of transmit and receive similar to a crossover cable. A setting of MDI-X allows two DCE devices, such as two hubs or switches, to connect to each other using a typical straight through wired twisted-pair cable.
Ethernet Topology
Ethernet is defined at the data link layer of the OSI model and uses what is commonly referred to as a bus topology. A bus topology consists of devices strung together in series with each device connecting to a long cable or bus. Many devices can tap into the bus and begin communication with all other devices on that cable segment. This means that all the network devices are attached to a single wire and are all peers, sharing the same media.
Bus topology has two very glaring faults. First, if there were a break in the main cable, the entire network would go down. Second, it was hard to troubleshoot. It took time to find out where the cable was cut off. The star topology has been deployed for a long time now and is the standard in the LAN environment. Star topologies link nodes directly to a central point. The central point is either a hub or a LAN switch. Ethernet hubs are multiport repeaters, meaning they repeat the signal out each port except the source port.
The advantages of a physical star topology network are reliability and serviceability. If a point-to-point segment has a break, in the star topology, it will affect only the node on that link. Other nodes on the network continue to operate as if that connection were nonexistent. Ethernet hubs and LAN switches act as the repeaters that centralize the twisted-pair media. Twisted-pair media can also be used to join like devices. Following the OSI model and the concept of interchangeable parts, even Token Ring, which is a logical ring, can use a physical star topology with twisted pair.
Ethernet Logical Addressing
In Ethernet, LAN devices must have a unique identifier on that specific domain. LAN devices use a Media Access Control (MAC) address for such purpose. MAC addresses are also referred to as hardware addresses or burned-in addresses because they are usually programmed into the Ethernet adapter by the manufacturer of the hardware.
The format of a MAC address is a 48-bit hexadecimal address. Because hexadecimal uses the digits 0-9 and the letters a-f (for numbers 10-15), this yields a 12-digit address. MAC addresses are represented in any one of four formats. All the formats properly identify a MAC address and differ only in the field separators, as follows:
Dashes between each two characters: 00-01-03-23-31-DD
Colons instead of dashes between each two characters: 00:01:03:23:31:DD
Periods between each fourth character: 0001.0323.31DD
The digits without dashes, periods, or colons: 0001032331DD
Cisco routers typically use the 0001.0323.31DD formatting, while Cisco switches running Catalyst Operation System (Catalyst OS) images use 00:01:03:23:31:DD to represent the same address.
CSMA/CD Operation
Ethernet operates using CSMA/CD. By definition, CSMA/CD is half-duplex communication. Half duplex implies that only one device on the Ethernet LAN "talks" at a time, and devices connected to the same Ethernet network are considered to be part of the same collision domain. Devices sending traffic in the same collision domain have the potential of their packets colliding with each other when two devices attempt to transmit at the same time. The logical definition of this range of devices is called a domain, hence the term collision domain.
The old style telephone party line example best illustrates the concept of a collision domain, as shown in Figure 1-3.
Figure 1-3. Telephone Party Line
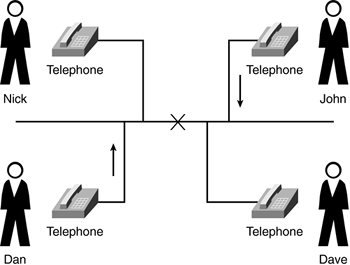
Table 1-2 lists each party line operation and compares it to Ethernet.
Step | Telephone Party Line Operation | Ethernet Operation |
|---|---|---|
1 | I pick up the phone. Is anyone talking? | The LAN device listens to the Ethernet network to sense the carrier signal on the network. |
2 | If no one is speaking, I can start talking. I'll keep listening to make sure no one speaks at the same time as me. | If the LAN device does not detect a carrier signal on the network, it can begin transmitting. The LAN device listens to the carrier signal on the network and matches it to the output. |
3 | If I can't hear myself speak, I'll assume someone is trying to speak at the same time. | If there is a discrepancy between input and output, another LAN device has transmitted. This is a collision. |
4 | I'll then yell out to tell the other person to stop talking. | The LAN device sends out a jamming signal to alert the other LAN devices that there has been a collision. |
5 | I will then wait a random amount of time to start my conversation again. | The LAN device waits a random amount of time to start transmitting again. This is called the backoff algorithm. If multiple attempts to transmit fail, the backoff algorithm increases the amount of time waited. |
In a party line, people occasionally speak over each other. When the party line is loaded with more callers, the more often people attempt to speak at the same time. It is the same with Ethernet collisions. Because users share Ethernet bandwidth and are part of the same collision domain, it is often referred to as shared media or shared Ethernet. (See Figure 1-4.) The efficiency of shared Ethernet is proportional to the number of devices attempting to communicate at the same time. As more devices are added, the efficiency decreases.
Figure 1-4. Shared Ethernet Segment
The algorithm in CSMA/CD used after a collision is Truncated Binary Exponential Backoff algorithm. When a collision occurs, the device must wait a random number of slot times before attempting to retransmit the packet. The slot time is contingent upon the speed of the link. For instance, slot time will be different for 10 Mbps Ethernet versus 100 Mbps Ethernet. Table 1-3 shows an example for a 10 Mbps Ethernet link. Cisco switches uses a more aggressive Max Wait Time than what is illustrated in this example. The purpose of the example is to give you a feel for how Truncated Binary Exponential Backoff works.
Retry | Range | Max Number | Max Wait Time |
|---|---|---|---|
1st | 0-1 | (2^1)-1 | 51.2us |
2nd | 0-3 | (2^2)-1 | 153.6us |
3rd | 0-7 | (2^3)-1 | 358.4us |
4th | 0-15 | (2^4)-1 | 768.0us |
5th | 0-31 | (2^5)-1 | 1587.2us |
6th | 0-63 | (2^6)-1 | 3225.6us |
7th | 0-127 | (2^7)-1 | 6502.4us |
8th | 0-255 | (2^8)-1 | 13056.0us |
9th | 0-511 | (2^9)-1 | 26163.2us |
10th ? 15th | 0-1023 | (2^10)-1 | 52377.6us |
Cisco switches monitor various collision counters, as follows:
Single
Multiple
Late
Excessive
Of the four types, be wary of late and excessive collisions. Late collisions occur when two devices send data at the same time. Unlike single and multiple collisions, late collisions cause packets to be lost. Late collisions are usually indicative of the cable exceeding IEEE specifications. Cascading hubs (connecting two or more hubs to each other) can also cause the length of the collision domain to increase above specification. You can use a Time Delay Reflectometer (TDR) to detect cable fault and whether the cable is within the IEEE standard. Other factors that cause late collisions include mismatched duplex settings and bad transceivers. Example 1-1 shows the output from a switch that has detected a late collision on one of its ports.
Example 1-1. Late Collision Error Messages
%LANCE-5-LATECOLL: Unit [DEC], late collision error %PQUICC-5-LATECOLL: Unit [DEC], late collision error
The slot time, 51.2 microseconds, used to detect and report collisions is based on the round trip time between the furthest points on the Ethernet link. The value is calculated by taking the smallest Ethernet frame size of 64 bytes and multiplying it by 8 bits, which gives 512 bits. This number is then multiplied by .1 microseconds. The farthest distance between the end points of the cable should be reached within half of this slot time, 25.6 microseconds.
Excessive collisions typically occur when too much traffic is on the wire or too many devices are in the collision domain. After the fifteenth retransmission plus the original attempt, the excessive collisions counter increments, and the packet gets dropped. In this case, too many devices are competing for the wire. In addition, duplex mismatches can also cause the problem. A syslog message is generated by the switch, as depicted in Example 1-2, when excessive collision occurs on the port.
Example 1-2. Excessive Collisions Error Message
%PQUICC-5-COLL: Unit [DEC], excessive collisions. Retry limit [DEC] exceeded
On the switch, the show port mod/port command provides information about collisions, multiple collisions, and so on. Example 1-3 is an excerpt from the show port command that is useful. This example was taken from a switch that was running Catalyst OS software.
Example 1-3. Sample of show port Command
Switch1 (enable) show port 10/3
Port Single-Col Multi-Coll Late-Coll Excess-Col Carri-Sen Runts Giants
----- ---------- ---------- ---------- ---------- --------- --------- ---------
10/3 37 3 24 0 0 0 0
Full-Duplex Ethernet
In the party line scenario, congestion occurs when more than two people attempt to talk at the same time. When only two people are talking, or only two devices, virtually all the bandwidth is available. In cases where only two devices need to communicate, Ethernet can be configured to operate in full-duplex mode as opposed to the normal half-duplex operation. Full-duplex operation allows a network device to "talk" or transmit and "listen" or receive at the same time. (See Figure 1-5.)
Figure 1-5. Full-Duplex Directly Connected Hosts
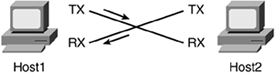
Because Ethernet is based on CSMA/CD, full-duplex devices either need to be directly connected to each other or be connected to a device that allows full-duplex operation (such as a LAN switch). Ethernet hubs do not allow full-duplex operation, as they are only physical layer (Layer 1) signal repeaters for the logical bus (Layer 2). Ethernet still operates as a logical bus under full duplex.
Autonegotiation
Autonegotiation is a mechanism that allows two devices at either end to negotiate speed and duplex settings at physical layer. The benefits of autonegotiation include minimal configuration and operability between dissimilar Ethernet technologies.
In today's networks, 10BASE-T and 100BASE-T are ubiquitous. Newer Cisco modules such as the WS-X6548-GE-TX have ports capable of 10/100/1000BASE-T. Most existing network interface cards (NICs) operate at 10/100 speeds, with newer NICs offering 10/100/1000BASE-T operation. NICs capable of autonegotiating speed and duplex are beneficial because more and more users are becoming mobile. One day, a user might be connected to the office Catalyst switch at 100 Mbps, and the next day, a remote site that supports only 10 Mbps. The primary objective is to ensure that the user not only has easy access to the network but also has network reliability. If the user's laptop NIC is hard coded at 100BASE-T full duplex, the user connectivity might be impacted because the two switches might have different types of modules that operate at different speeds. For instance, the module in the office building is WS-X5225 (24 port 10/100BASE-TX), and the remote site has WS-X5013 (24 port 10BASE-T). In this case, because the switches are set by default to autonegotiate, a user with a NIC hard coded to 100BASE-T full duplex will not get any connectivity. Setting up autonegotiation on both the switch and laptop gets rid of this problem. The user no longer has to worry about the laptop NIC settings because the NIC automatically negotiates the proper physical layer configuration with the end device to which it connects.
The actual mechanics behind autonegotiation are straightforward, as depicted in Figure 1-6. Autonegotiation attempts to match speed and duplex mode at the highest priority with its link partner. Since the introduction of 1000BASE-T, the priorities have been readjusted. Table 1-4 describes each priority level.
Figure 1-6. Ethernet Autonegotiation
Priority | Ethernet Specification | Type of Duplex |
|---|---|---|
1 | 1000BASE-T | Full duplex |
2 | 1000BASE-T | Half duplex |
3 | 100BASE-T2 | Full duplex |
4 | 100BASE-TX | Full duplex |
5 | 100BASE-T2 | Half duplex |
6 | 100BASE-T4 | --- |
7 | 100BASE-TX | Half duplex |
8 | 10BASE-T | Full duplex |
9 | 10BASE-T | Half duplex |
The 10BASE-T specification does not include autonegotiation between devices. Autonegotiation was first introduced in IEEE 802.3u Fast Ethernet specification as an optional parameter. In a 10BASE-T environment, a single pulse, called the Normal Link Pulse (NLP), is sent every 16 ms (±8 ms) on an idle link. The NLP performs a link integrity test for 10BASE-T. When no traffic is on the link, the 10BASE-T device generates a NLP on the wire to keep the link from going down. The 10BASE-T device stops generating pulses when it receives data packets. A link failure occurs under conditions when the 10BASE-T device does not receive NLPs or a single data packet within a specified time slot.
As mentioned earlier, the IEEE 802.3u specification has an optional programmable field for autonegotiation. Within autonegotiation, there are various other optional operations, such as Remote Fault Indication and Next Page Function. Remote Fault Indication detects and informs the link partner of physical layer errors. The Next Page Function provides more verbose information about the negotiation process. One of the more appealing features of autonegotiation is compatibility with dissimilar Ethernet technologies. For example, Fast Ethernet is backward-compatible with 10BASE-T through a Parallel Detection mechanism. Essentially, the Fast Ethernet switches to NLP to communicate with a 10BASE-T device. Parallel Detection is when only one of the two link partners is capable of autonegotiation.
Fast Ethernet uses the same pulse structure as 10BASE-T. In 10BASE-T, there is only a single pulse every 16 ms, whereas in Fast Ethernet, there are bursts of pulses in intervals of 16 (±8) ms. In these pulses, or groups of pulses, the capability of the device is encoded in a 16-bit word called a Link Code Word (LCW), also known as Fast Link Pulse (FLP). The length of the burst is approximately 2 ms.
NOTE
Fast Ethernet vendors used their discretion whether to add autonegotiation capabilities to their devices. As a result, Fast Ethernet NICs without autonegotiation capabilities were once found in the marketplace.
Gigabit Ethernet implementation requires that all IEEE 802.3z compliant devices have autonegotiation capability. Autonegotiation can, however, be disabled through a software feature. From the actual hardware perspective, the 802.3z specification requires autonegotiation capabilities on the device. On Cisco Catalyst switches, autonegotiation can be disabled with the following command. Note that this command must be configured on both link partners:
set port negotiation <mod/port> enable | disable
The parameters that 802.3z devices negotiate are
Duplex setting
Flow control
Remote fault information
Although duplex setting can be negotiated, Cisco switches operate Gigabit Ethernet in full-duplex mode only. With the introduction of the newer 1000/100/10 blades, a port can operate at various speeds and duplex settings. However, it is unlikely that Cisco will support Gigabit half duplex in any point-to-point configurations with even the aforementioned blades. Use the show port capabilities command that is available in Catalyst OS to view the features supported by the line module, as shown in Example 1-4.
Example 1-4. Output from show port capabilities Command
Switch1 (enable) show port capabilities 1/1
Model WS-X6K-SUP2-2GE
Port 1/1
Type 1000BaseSX
Speed 1000
Duplex full
Flow control is an optional feature that is part of the 802.3x specification. The concept behind flow control is to help reduce the burden on the port that is overwhelmed with traffic. It does this by creating back-pressure on the network. If the volume of traffic is such that a port runs out of buffers, it drops subsequent packets. The flow control mechanism simply tells the transmitter to back off for a period of time by sending an Ethernet Pause Frame (MAC address of 01-80-c2-00-00-01) to the transmitter. The transmitter receives this frame and buffers the outgoing packets in its output buffer queue. This mechanism provides needed time for the receiver to clear the packets that are in its input queue. The obvious advantage is that packets are not dropped. The negative aspect to this process is latency. Certain multicast, voice, and video traffic are sensitive to latency on the network. It is recommended that flow control should be implemented with care. Typically, this feature is implemented as a quick fix. Not all Cisco switches support this feature.
set port flowcontrol <mod/port>
Remote fault information detects and advertises physical layer problems such as excessive noise, wrong cable types, bad hardware, and so on to the remote peer. The switch is programmed to take a proactive approach when excessive physical layer problems exist. A port that is generating errors can potentially disrupt a network. For instance, it can cause spanning-tree problems and traffic black holing, and drain system resources. As a result, the switch error disables the port.
Looking at some examples will solidify the concept and function of autonegotiation. In Figure 1-7, Host1 and the hub are link partners over a 10BASE-T connection. 10BASE-T has no knowledge of autonegotiation, and therefore, the devices must statically be configured. NLPs are sent by both devices when they come online. In this example, these devices operate over a 10BASE-T half-duplex connection.
Figure 1-7. 10BASE-T Autonegotiation
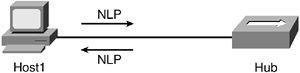
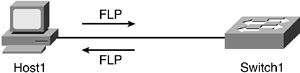
Figure 1-8 shows a straight 100BASE-T connection with both devices enabled for autonegotiation. FLP bursts are sent to advertise the device's capabilities and negotiate a maximum highest bandwidth connection. The highest connection negotiated is priority 4, which is 100BASE-TX full duplex.
Figure 1-8. 100BASE-T Autonegotiation
The following is the command that configures a switch to autonegotiate a port:
set port speed <mod/port> auto
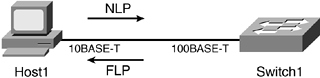
In Figure 1-9, Host1 has a 10BASE-T card. The switch has a capability to operate in both 10BASE-T and 100BASE-T mode. The 10/100 modules are common in a switching environment. Cisco has various 10/100 modules with various features and functionalities. In this example, there is a mismatch between the pulses sent by the Host1 and the switch. Because Host1 has a 10BASE-T card, it can send only NLPs. Initially, when the switch comes online, it generates only FLP bursts. When the switch detects NLPs from its link partner, it ceases to generate FLP bursts and switches to NLP. Depending on the static configuration on Host1, the switch chooses that priority. In this instance, the connection is 10BASE-T operating at half duplex.
Figure 1-9. 10/100BASE-T Autonegotiation
The finer points of autonegotiation have been discussed; however, some drawbacks need to be discussed. Numerous network problems resulted when the autonegotiation feature was first deployed. The issues ranged from degradation in performance to connectivity loss. The cause of some of these problems included advanced software features that came with the NIC, vendors not fully conforming to 802.3u standard, and buggy code. These days, now that manufacturers have resolved these issues, misconfiguration is the biggest remaining problem. Table 1-5 and Table 1-6 show various consequences from misconfigurations. For instance, a duplex mismatch can degrade performance on the wire and potentially cause packet loss.
Configuration NIC (Speed/Duplex) | Configuration Switch (Speed/Duplex) | Resulting NIC Speed/Duplex | Resulting Catalyst Speed/Duplex | Comments |
|---|---|---|---|---|
AUTO | AUTO | 100 Mbps, Full duplex | 100 Mbps, Full duplex | Assuming maximum capability of Catalyst switch and NIC is 100 full duplex. |
100 Mbps, Full duplex | AUTO | 100 Mbps, Full duplex | 100 Mbps, Half duplex | Duplex mismatch. |
AUTO | 100 Mbps, Full duplex | 100 Mbps, Half duplex | 100 Mbps, Full duplex | Duplex mismatch. |
100 Mbps, Full duplex | 100 Mbps, Full duplex | 100 Mbps, Full duplex | 100 Mbps, Full duplex | Correct manual configuration. |
100 Mbps, Half duplex | AUTO | 100 Mbps, Half duplex | 100 Mbps, Half duplex | Link is established, but switch does not see any autonegotiation information from NIC and defaults to half duplex. |
10 Mbps, Half duplex | AUTO | 10 Mbps, Half duplex | 10 Mbps, Half duplex | Link is established, but switch will not see FLP and will default to 10 Mbps half duplex. |
10 Mbps, Half duplex | 100 Mbps, Half duplex | No Link | No Link | Neither side will establish link because of speed mismatch. |
AUTO | 100 Mbps, Half duplex | 10 Mbps, Half duplex | 10 Mbps, Half duplex | Link is established, but NIC will not see FLP and default to 10 Mbps half duplex. |
Switch Port Gigabit | Autonegotiation Setting | NIC Gigabit Autonegotiation Setting | Switch Link/NIC Link |
|---|---|---|---|
Enabled | Enabled | Up | Up |
Disabled | Disabled | Up | Up |
Enabled | Disabled | Down | Up |
Disabled | Enabled | Up | Down |
Network engineers still have heated discussions about whether to enable autonegotiation in the network. As mentioned earlier, autonegotiation is a big advantage for mobile users. A user should not have to worry about configuring his laptop every time he goes to a different location.
The rule of thumb is to enable autonegotiation on access ports that connect to users. Mission-critical devices should be statically configured to protect the network from possible outages and performance hits. Therefore, connections between routers and switches, or servers and switches should be hard coded with the appropriate speed and duplex settings.







