Transparent Bridging
The inability to allow more than one device to transmit simultaneously presents a major challenge when attempting to connect dozens or hundreds of users together through Ethernet.
Transparent bridging is the augmentation of Ethernet allowing partial segmentation of the network into two or more collision domains. The IEEE-defined transparent bridging is an industry standard in 802.1D. Transparent bridges improve network performance by allowing devices in the same segmented collision domain to communicate without that traffic unnecessarily being forwarded to the other collision domain.
Transparent bridges are the predominant bridge type for Ethernet, and it is important to understand Ethernet switches essentially act as multiport transparent bridges.
Figure 1-10 shows a transparent bridge supporting Ethernet segments or collision domains. If Host1 and Host2 are talking to each other, their conversation will use bandwidth only on their side of the bridge. This allows Host4 and Host5 to also hold a conversation. If all devices were in the same collision domain, only one conversation would be possible.
Figure 1-10. Host1 to Host2 and Host4 to Host5
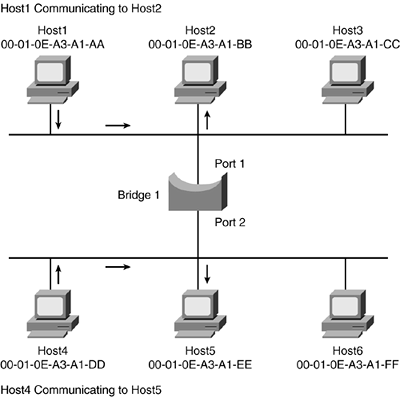
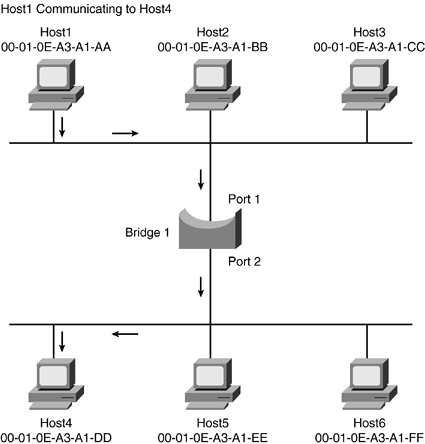
However, if Host1 wants to talk to Host4, as shown in Figure 1-11, the bandwidth will be utilized on both sides of the bridge, allowing only the one conversation.
Figure 1-11. Host1 to Host4
How does the transparent bridge determine which users are connected to which side of the bridge? Well, transparent bridging has a little more "under the hood" than the example illustrates. The 802.1D specification for transparent bridging defines five unique processes as part of transparent bridging:
Learning
Flooding
Filtering
Forwarding
Aging
The following sections describe each of these processes in more detail.
Learning
Learning is the process of obtaining the MAC address of devices. When a bridge is first turned on, it has no entries in its bridge table. As traffic passes through the bridge, the sender's MAC addresses are stored in a table along with the associated port on which the traffic was received. This table is often called a bridge table, MAC table, or content addressable memory (CAM) table.
Table 1-7 shows a listing of all the devices on the sample network in Figure 1-10 and Figure 1-11.
Hosts | Port 1 | Port 2 |
|---|---|---|
Host1/ 00-01-0E-A3-A1-AA | X | |
Host2/ 00-01-0E-A3-A1-BB | X | |
Host3/ 00-01-0E-A3-A1-CC | X | |
Host4/ 00-01-0E-A3-A1-DD | X | |
Host5/ 00-01-0E-A3-A1-EE | X | |
Host6/ 00-01-0E-A3-A1-FF | X |
Flooding
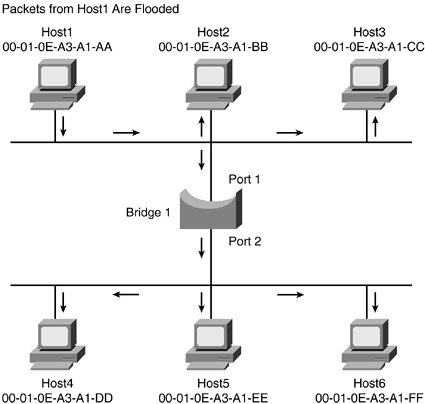
When a bridge does not have an entry in its bridge table for a specific address, it must transparently pass the traffic through all its ports except the source port. This is known as flooding. The source port is not "flooded" because the original traffic came in on this port and already exists on that segment. Flooding allows the bridge to learn, as well as stay transparent to the rest of the network, because no traffic is lost while the bridge is learning. Figure 1-12 shows how the bridge forwards the traffic on all its ports.
Figure 1-12. Bridge1 Floods Traffic
Filtering
After the bridge learns the MAC address and associated port of the devices to which it is connected, the benefits of transparent bridging can be seen by way of filtering. Filtering occurs when the source and destination are on the same side (same bridge port) of the bridge. In Figure 1-10, filtering occurs each time Host1 and Host2 talk, as well as when Host4 and Host5 talk.
Forwarding
Forwarding is simply passing traffic from a known device located on one bridge port to another known device located on a different bridge port. Again, referring back to Figure 1-11, after the initial devices were learned, forwarding occurs when Host1 and Host4 talk.
Aging
In addition to the MAC address and the associated port, a bridge also records the time that the device was learned. Aging of learned MAC addresses allows the bridge to adapt to moves, adds, and changes of devices to the network. After a device is learned, the bridge starts an aging timer. Each time the bridge forwards or filters a frame from a device, it restarts that device's timer. If the bridge doesn't hear from a device in a preset period of time, the aging timer expires and the bridge removes the device from its table.
Aging ensures that the bridge tracks only active systems, and ensures that the MAC address table does not consume too much system memory.







