Categories of Threats
Now that you understand the basic components of a security threat, this section covers how security threats are categorized. When talking about a specific type of a security threat, it typically is categorized by using one of the following terms:
Reconnaissance attacks
Access attacks
Denial of service (DoS) attacks
The following sections cover these three categories more thoroughly, including some specific attacks that fall under these categories and solutions that can be used to deal with these threats.
Reconnaissance Attacks
In a reconnaissance attack, a hacker tries to gain information about your network, including its topology, the devices that reside inside it, the software running on them, and the configuration that has been applied to these devices. The hacker then uses this information to execute further attacks, such as DoS or access attacks. Reconnaissance attacks come in different types, including the following:
Scanning
Eavesdropping
The following sections cover the basics of these types of reconnaissance attacks.
Scanning Attacks
The most common type of reconnaissance attack is a scanning attack. A network scanning attack occurs when a hacker probes the machines in your network. He might do this by sending an ICMP ping to every IP address in your network, or he might use a network ping, in which he pings the IP address of the directed broadcast of every network. As an example, if you have a network of 200.200.200.0/24, the hacker would ping 200.200.200.255. There are other ways to scan networking devices, but these two methods are the most popular.
Of course, a network scan tells the hacker only that there are machines in your network with a configured IP address; it does not tell what services are running on these machines. To find out what services are running on a machine, a hacker uses a port-scanning utility. A port-scanning utility probes the port numbers of a machine to detect whether a service is running. Using this approach, a hacker can determine whether the machine is running SMTP, Telnet, FTP, WWW, or other services. The hacker then can use this to plan further attacks against your device.
TIP
Many scanning tools are available?freeware, shareware, and commercial. One of my favorites, GFI's LANguard Network Security Scanner, is a feature-rich network-scanner tool. It comes with a 30-day trial, after which certain features are disabled unless you purchase the full version. It can be downloaded from http://www.gfi.com/. I use this tool a lot when examining networks to see what services are running, which is helpful in determining whether devices are exposed. I also use a product called Nessus, available at http://www.nessus.org/, and Cisco Scanner (formerly known as NetSonar), available at http://www.cisco.com/univercd/cc/td/doc/pcat/nssq.htm.
The most common method of stopping networking and port-scanning attacks is to use filtering devices. This can be something as simple as using Cisco routers with access control lists or a sophisticated firewall. These concepts are discussed in much more depth in Chapter 2.
Of course, you always should play it safe and disable all services that are not necessary on all of your resources. For instance, if you have a web server, you should disable services such as Telnet, SMTP, finger, and FTP on it. You want to make it as hard as possible for any hacker to get even the smallest of footholds in your network. Performing these tasks on a Cisco router is discussed in Chapter 4.
Eavesdropping Attacks
Another form of reconnaissance attack is eavesdropping. Eavesdropping is the process of examining packets as they are in transit between a source and destination device. A hacker typically uses a protocol-analyzer tool to perform eavesdropping. Figure 1-3 shows how eavesdropping works. In step 1 of this example, the hacker is examining traffic between the user and the server. The hacker notices that the user is establishing a Telnet connection and authenticates with a username and password. Because Telnet passes this information in clear text, the hacker now knows how to log into the Telnet server, spoofing the identity of the user. In step 2, the hacker uses this information to log into the Telnet server.
Figure 1-3. Eavesdropping Attack
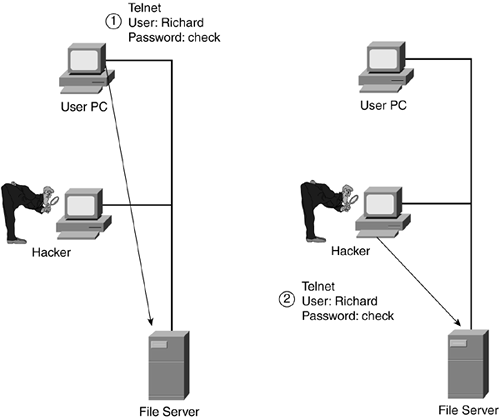
The protocol analyzer used for eavesdropping, sometimes referred to as a packet sniffer, might be a sophisticated hardware-based protocol analyzer, such as the Network Associates Sniffer products, or it might be a software-based application running on a PC (Network Associates also sells a software-based Sniffer version). For software applications, the hacker needs a promiscuous network interface card (NIC); this is a NIC that processes all frames, not just frames with a destination MAC address that matches the one on the NIC. Many commercial, shareware, and freeware protocol-analyzer products are available.
To execute this attack, the hacker typically must be connected physically to the network somewhere between the source and the destination, and must see the actual packets. Another approach that a hacker more typically uses is to compromise a PC in the network and download a packet-sniffing program to it. When eavesdropping, the hacker looks for account names and passwords, such as these:
Microsoft Windows login
Novell Netware login
Telnet login
FTP login
HTTP login
Hackers also use eavesdropping to examine other information, perhaps database or financial transactions.
To prevent eavesdropping, your best solution is to use some form of encryption on your packets. VPNs, which are discussed in Part VIII, "Virtual Private Networks," allow you to use Data Encryption Standard (DES), 3DES, and AES encryption algorithms to protect your data. For terminal access, you should use a Secure Shell (SSH) program, which is an encrypted form of Telnet. For web access, you should use HTTP with Secure Socket Layer (HTTPS), which uses Secure Socket Layer (SSL) encryption.
You always should encrypt the following types of information:
Passwords (and sometimes usernames)
Personal information, such as telephone numbers, medical information, driver's license numbers, and social security numbers
Credit card information
Financial transactions
Company trade secrets and sensitive information
Two basic methods of implementing encryption exist:
Link encryption? The entire frame (Ethernet, token ring, Frame Relay, HDLC, and so on) is encrypted. This method of encryption can be used only on point-to-point connections in which both sides are configured for encryption.
Packet encryption? Only the packet contents, such as the TCP or UDP segments in an IP packet (the payload), are encrypted; the addressing information (IP addresses in the IP header) is not. This method of encryption is used on connections that traverse multiple hops, such as internal networks, public networks, and the Internet.
NOTE
Because encryption is very process intensive, it typically is used for external connections; in other words, it typically is not used inside your network. For internal security, you might want to include in your security policy a statement that prohibits eavesdropping, with severe penalties applied. However, for sensitive information, encryption should be used to protect it. Obviously, certain network administrators should be allowed to perform eavesdropping in certain situations, such as troubleshooting connectivity issues. Any other type of eavesdropping by anybody else (other employees), however, should not be tolerated and should be dealt with immediately.
Another solution is to employ a switched infrastructure, giving every device its own switch port connection. Using this design, even if a hacker has compromised one of the PCs in your network and loads a packet-sniffing tool onto the PC, the hacker will be able to see only traffic directed at the compromised PC or multicast or broadcast traffic. However, one concern to consider is the security of the switches themselves. If the hacker can compromise both a PC and the switch connected to the PC, the hacker can set up port mirroring, to have the switch mirror traffic from other ports to the port of the compromised PC. Cisco calls this mirroring process SPAN, short for switched port analyzer.
Access Attacks
Another common type of attack is an access attack. In an access attack, a hacker attempts to gain unauthorized or illegal access to your network and its resources, particularly resources such as file, e-mail, and web servers. He typically does this by trying to access password files, using password-cracking programs, or examining traffic on your network for packets that contain clear-text passwords (eavesdropping attack). Other types of attacks include exploiting weaknesses in operating systems and applications, such as buffer overflows, that can allow a hacker access without first authenticating.
After a hacker has broken into one of your networking devices, he usually tries to raise his privilege level to the highest possible degree and then uses this account to break into other networking devices. He also might modify files on your resources or, in the worst possible scenario, erase everything on the disk drive and laugh as he tells his story to his friends. The following sections cover the basics of these types of access attacks.
Unauthorized Access Attack
In the most basic form of an access attack, a hacker tries to gain illegal access to equipment in your network. This is called an unauthorized access attack. To accomplish this kind of attack, a hacker can use many tools, including the following:
Guessing passwords for well-known accounts, such as root and Administrator
Using a protocol analyzer and executing an eavesdropping attack to examine clear-text passwords in packets
Accessing a password file and using a password-cracking program on it
Using social engineering
The last item, social engineering, is probably the hacker's easiest method of gaining unauthorized access to resources in your network. With social engineering, a hacker calls various users in your network, pretending to be a network administrator. The hacker tells the user about some fictional network security problem and, using guile and ingenuity, gathers information from the user that the hacker then can use to access resources on your network. This can go the other way, too; the hacker can pretend to be a user and can call a network administrator, acting as if he has forgotten his password.
The solution that you implement to restrict unauthorized access attacks depends on the method the hacker is using to gain unauthorized access. For instance, if the hacker is trying to gain illegal access to your network through your network's remote access (dialup) server, you probably would want to implement the following solutions:
Use the Challenge Handshake Authentication Protocol (CHAP) with PPP (Point-to-Point Protocol), where the password is not sent across the wire, is tied to a specific user, and is verified by a security server
Use double authentication. Cisco IOS routers have two features: Lock-and-key access control lists (ACLs) and authentication proxy. Lock-and-key works hand-in-hand with PPP's CHAP. The user is authenticated first through CHAP and then through lock-and-key. However, lock-and-key also works over nondialup links. Lock-and-key is discussed in Chapter 13, "Lock-and-Key Access Lists." Authentication proxy (AP) is the preferred method of authenticating users and is discussed in Chapter 14, "Authentication Proxy." It also has the capability to authenticate users before allowing them access to network resources. As you will see in Chapter 14, Cisco recommends using AP over lock-and-key because it is more flexible, supporting Telnet, FTP, HTTP, and HTTPS for authentication.
For application security, if your applications support additional security mechanisms, you definitely should implement them. For some applications, you might consider replacing them. For instance, the standard Telnet application uses clear-text passwords when performing authentication. You might want to consider replacing your standard Telnet application with a secure one that encrypts the password before sending it across the network, such as SSH. You also should disable all unnecessary services and consider using a host-based firewall. Host-based firewalls are discussed in more depth in Chapter 2.
Centralizing Authentication FunctionsI once worked with a client that had to manage more than 1000 Cisco routers. This client was using the standard user EXEC and privileged EXEC passwords on these devices for authentication. When the company hired contractors, it hired them only to perform monitoring functions on the network: They never performed configuration tasks. This was because every week a new contractor was hired and an old contractor's time was up, and the old contractor moved on to the next job. The networking department did not want to have to change all of the privileged EXEC passwords on the routers every time a contractor left the company. Therefore, the solution was simple: Give only permanent employees the privileged EXEC password for the routers. |
One of the biggest problems that you will face is the management of your security solution. A much better and more manageable solution than the one discussed in the previous sidebar is to use a centralized security server; Cisco has one called Cisco Secure ACS. You configure all of your user accounts and security policies on this server, and you have your routers and other networking devices use this security server to perform authentication functions. By centralizing the authentication process, you have more control over who is accessing your devices and what they are doing on them, making it easier to determine whether unauthorized access attacks are occurring. Centralizing authentication functions is discussed in Chapter 5.
One often-neglected prevention method, but one that is easy to implement, is user training. By training users not to write their passwords on their desk, to use passwords that do not have common words and that have a mixture of letters and numbers, and to be careful about what they say to people over the telephone or in person, you make your security job easier.
Data-Manipulation Attack
Data manipulation is simply the process of a hacker changing information. These changes could be something as simple as modifying file contents on a file server or something as sophisticated as changing packet contents as they are in transit from a source to a destination machine.
A common attack that hackers employ is to break into your web server and change the content (web pages). This form of attack is called graffiti. This type of attack has happened to many organizations, typically government resources; a hacker breaks into a web server and replaces the web content with pornography or "interesting" political content. To execute this kind of attack, a hacker typically first performs a reconnaissance attack, such as eavesdropping, to discover user accounts and passwords, and then executes an unauthorized access attack. A more ingenious hacker might use Java or ActiveX scripts either to learn information about a client's device or to break into it. Likewise, a hacker might try to take advantage of known vulnerabilities in a web server application or operating system.
The best method of preventing data-manipulation attacks is to implement a centralized and robust authentication and authorization system, such as Cisco Secure ACS, which is discussed briefly in the previous section. With this solution, you can restrict what users can access, restrict what they can do on the service that they access, and record the event for security purposes.
For file servers, tools are available to take a snapshot of your files, and the snapshot then is stored in a secured location. You periodically should compare the critical files on your server to the snapshot that you took previously. If there is a difference between the two, you might be a victim of a data-manipulation attack. One of the most common security tools that performs this function is Tripwire, which can be accessed from http://www.tripwire.com/.
To prevent Java and ActiveX attacks on your users, and possibly your web servers, you should use a filtering solution that can filter Java and ActiveX scripts that are embedded in HTML pages. Many solutions are available, including the use of Cisco IOS routers and the PIX firewall. If you are concerned about the actual content that users access or what Internet sites that they can view, you might want to put in place a web filtering solution, such as WebSense or N2H2. Many sites have inappropriate material for business purposes, as well as hacking and cracking tools. Cisco IOS routers and the PIX firewall can work hand in hand with WebSense and N2H2. Both of these products enable you to enter policy information about what URLs a user can or cannot access. When the Cisco IOS router or PIX sees a web access request from a user, it first verifies it with the policy server before permitting it. Filtering of Java and ActiveX scripts, as well as URL filtering, is discussed in Chapter 10, "Filtering Web and Application Traffic."
To prevent a hacker from using known vulnerabilities to access your system, you should make sure that your applications and operating systems have the latest security patches applied. Microsoft Windows products simplify this process with the Windows Update tool, which automates the process.
Session Attacks
One of the most difficult attacks that a hacker can carry out is a session layer attack. In a session attack, a hacker attacks a session layer connection, hoping either to use this information to mount another attack, or, through subterfuge, to take over the session in which he pretends to be either the source or the destination device. Four general categories of session attacks exist:
Masquerading
Session replay
Session hijacking
Repudiation
The following sections cover these session attacks in more depth.
Masquerading Attack
Masquerading is an attack method that a hacker uses to hide his identity. He pretends to be a different machine by changing his source address in his IP packets. An example of this attack is discussed earlier in the chapter in the "Unstructured and Structured Threats" section and in Figure 1-2.
In TCP/IP, this form of an attack is called IP spoofing. To carry out an IP spoofing attack, a hacker typically uses a software program that changes the source address of packets (and even the TCP sequence numbers for TCP segments). Many programs are available on the Internet to perform this process, including Hping (http://www.hping.org/) and Nemesis (http://www.packetfactory.net/Projects/nemesis/), as well as others. In some instances, the hacker can do this at the operating system level in certain versions of Linux.
A hacker typically implements a reconnaissance attack that involves the use of a port scanner to discover open ports, and possibly even an eavesdropping attack, using a protocol analyzer, to see the actual traffic flow, including usernames and passwords. Sophisticated hackers use a source IP address that resides inside your network to execute a masquerading attack. They combine this with a routing attack so that the packets sent to a destination are returned not to the source inside your network, but to the hacker himself. This requires excellent technology skills on the hacker's part.
NOTE
Most DoS attacks use IP spoofing, which makes tracking down the hacker difficult. I discuss this issue in more depth in Chapter 17, "DoS Protection."
Session-Replay Attacks
When a hacker executes a session-replay attack, he captures (actually, eavesdrops on) packets from a real session data transfer between two devices with a protocol analyzer. Then he uses this information to execute an attack on the source device, the destination, or both, at a later time. Sometimes a hacker downloads Java or ActiveX scripts to clients that capture web transactions?possibly even online order information such as credit card numbers?and then uses this for his own purposes. Another favorite method of hackers is to use cookies to masquerade as a site, and then to get the client device to believe that the hacker's computer is the real web destination.
Session-Hijacking Attacks
In a session-hijacking attack, a hacker attempts to take over an existing session between two computers. As an example, the hacker might cut the source device out of the picture and pretend to be the source, tricking the destination device into believing that the destination still is communicating with the original source. A sophisticated hacker even might be able to insert himself into the middle of the session, pretending to be the source to the real destination, and pretending to be the destination to the real source device.
A session-hijacking attack typically involves a handful of other attacks, such as masquerading, eavesdropping, and data manipulation. You might think that executing this type of attack would be very complicated; however, some protocols, such as TCP, are fairly predictable, especially in their use of sequence numbers for TCP segments. With a good hacking software program, a skilled hacker can insert himself into the middle of an existing connection. The top part of Figure 1-4 shows what a session looks like from the perspective of the source and destination that have been hijacked. The bottom of Figure 1-4 shows the actual data path of a hijacked session.
Figure 1-4. Session-Hijacking Attack
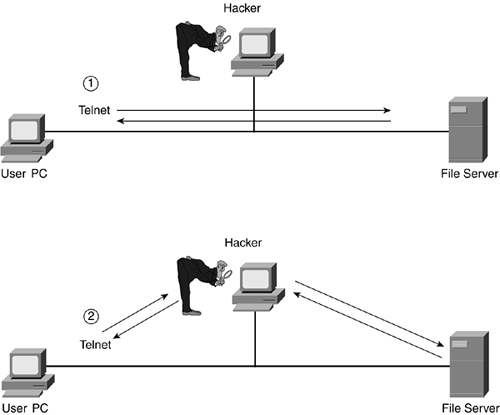
One of the easiest attacks that hackers like to employ involves masquerading and session hijacking. Almost all TCP/IP services use the Domain Name System (DNS) to resolve names to IP addresses. A skilled hacker can intercept DNS replies from servers and replace the IP addresses for the requested names with addresses of machines that the hacker controls, thus providing an easy method for ongoing session attacks.
Repudiation Attacks
Repudiation is a process in which you cannot prove that a transaction took place between two entities. The goal of the hacker is to perform repudiation when executing session layer attacks. Nonrepudiation, on the other hand, is having absolute proof of the identities of the parties in a transaction that has taken place. As an example, certain types of transactions need a nonrepudiation process. For instance, signing electronic documents, transferring money electronically, and buying a product online with your credit card all must have a nonrepudiation process, or else they cannot be legally binding.
Hackers typically use a repudiation attack when users are accessing web information. Hackers like to use Java or ActiveX scripts, port-scanning utilities, masquerading, and eavesdropping to carry out their repudiation attack. Perhaps one of the simplest forms of repudiation attacks is to use public e-mail systems such as hotmail.com, yahoo.com, and others to generate garbage mail and execute a DoS attack against a company's e-mail server. Getting a free e-mail account from these systems is usually a simple process, with little identity proof required. This makes it easy for a hacker to get an e-mail account and hide his activities behind a cloud of anonymity.
Two common issues with e-mail are spamming and e-mail bombs. Spamming is the process by which you receive unsolicited e-mail. This is perhaps one of the biggest complaints of anyone who has an Internet e-mail account; I am constantly getting spam e-mails. Another security problem is an e-mail bomb, an e-mail that contains code that is executed either automatically upon receipt or when a user clicks something, like a hyperlink or an attachment. The most common form of an e-mail bomb is a virus or worm. My Internet provider constantly scans for these types of e-mails, as does the antivirus software that I run on my PC.
Preventing Session Attacks
You can use many solutions to prevent session layer attacks against your user and service connections:
Using VPNs
Using SSL for web browser connections
Authenticating with digital signatures
Filtering Java and ActiveX scripts
Blocking e-mail from public e-mail sites
Probably the most important is using a Virtual Private Network (VPN) to encrypt information going across the connection. With a VPN, a hacker cannot see the actual data that is being transferred between the source and destination devices. Part VIII covers an overview of VPNs using IPSec and discusses how to configure IPSec connections on a Cisco IOS router. Secure Sockets Layer (SSL) provides security in web transactions. The main difference between IPSec and SSL is that IPSec can protect any type of IP traffic, whereas SSL can protect only web application traffic.
Another popular method used for providing identity verification is to use digital signatures. A digital signature is similar to a written signature, a person's thumbprint, a retinal scan of a person's eye, or a DNA profile of a person. In other words, it is used to uniquely identify the user. In the online world, a special third-party device called a Certificate Authority (CA) is used to handle the repository of identities. A CA performs a similar function to what a notary does in real life: It handles and validates identities of individuals. For instance, if you wanted to set up a connection to a remote site, but you wanted some kind of proof of the remote site's identity, your networking device could get the digital signature of the remote site from the CA and then request the remote site's own digital signature. Your networking device then would compare the two signatures. If they matched, you would know that you were dealing with the correct device; if they did not match, you would know that a session attack is occurring.
Another tool that you should consider using is a router or firewall that can filter Java and ActiveX scripts from untrusted sites. By filtering these scripts and applets, you are reducing the likelihood of a hacker performing a session layer attack. To make your life easier, your networking devices always should have logging enabled, and they should transfer this logging information to a central repository where you can keep an audit trail of important connections and transaction.
CAUTION
Be very careful if you decide to filter Java and ActiveX. Many, if not most, web sites take advantage of this technology to provide enhanced web features. Therefore, I recommend filtering these scripts only from networks in which known security threats exist.
To prevent spamming and e-mail bombs, as well as to reduce the likelihood of a hacker using a public e-mail site to execute a repudiation attack, you should block all e-mail access from public e-mail sites. This might mean that some legitimate people might not be able to send you e-mail any longer, but, on the other hand, you are greatly reducing the likelihood of exposure to reconnaissance, DoS, and repudiation attacks against your e-mail system. Many commercial products on the market help deal with spamming. The next section discusses some other solutions to e-mail bombs.
TIP
I use a program called MailWasher that scans my e-mail before downloading it. It is excellent for detecting spam messages and bouncing these back to the sender. Information about this excellent freeware product can be found at http://www.mailwasher.net/. However, this tool is for end-user use only; you also should have a good server tool to detect and remove SPAM.
Virus, Trojan Horse, and Worm Attacks
Viruses, worms, and Trojan horses are probably the most well-known attacks on computer systems because these are the most publicized, as well as the most likely to affect the general user public. Many different views actually exist regarding the definition of these three types of attacks. Generally, a virus is a program or a piece of code that is loaded onto and run on your computer without your knowledge. Many viruses also replicate themselves to spread their damage. Unlike bugs, viruses are manmade. A worm is a program that replicates itself over a network with some malicious intent in mind, such as crashing a system or using up all the resources on the system. Many people view viruses and worms as the same type of attack. A Trojan horse is a program loaded onto your computer that acts as a benign application, waiting for the user to activate it through normal computer and application activity. Unlike viruses and worms, Trojan horses do not replicate themselves. Sometimes Trojan horses pretend to be your antivirus software or replace it, hoping to add instead of remove viruses from your system.
These kinds of attacks might be something as simple as an e-mail attachment that you click or something as sophisticated as a software program that is executed because of a security problem with your e-mail program.
Typically, most of these attacks are exploited through the e-mail system, although there are other methods, such as executing an infected program. When executed as a reconnaissance attack, these attacks can send your e-mail's address book or your password file back to the hacker. When executed as a DoS attack, these attacks can affect the CPU cycles, memory, disk space, or bandwidth of a networking device, such as a PC.
You can employ three different methods in combating these kinds of attacks:
User training
Antivirus software
Application-verification software
One of the best defenses is to train your user population. For instance, you should warn your users never to open e-mails or attachments from individuals whom they do not know. Any suspicious e-mail should be reported immediately to a network administrator.
Of course, one of the most popular methods of dealing with these kinds of attacks is to deploy antivirus software. Many packages are available on the market, with the most popular being antivirus software packages from Network Associates and Norton (I use Norton on my PC). When deploying these in an enterprise network, you need to make absolutely sure that all of your desktops and servers have the most recent data files that contain the list of known viruses. You definitely will want to explore some type of automation process, in which a client's software is updated periodically (all commercial antivirus packages that I have dealt with support automatic updates of virus information on clients and servers).
Another typical solution for file servers is to use application verification software. This type of software takes a snapshot of existing files and keeps it in a secure place (usually on a separate, secure device). You typically include files such as executables, batch scripts, and configuration files in this snapshot. You then run a periodic analysis with the application-verification software, comparing the current files on the server with the secured ones. If there is a difference, the application alerts you to this. A difference might indicate that an access attack has taken place, possibly with a worm or Trojan horse attack, and that one of your files has been replaced with a hacker's file.
NOTE
To see an encyclopedia of viruses, worms, and Trojan horses, visit Symantec's site at http://securityresponse.symantec.com/avcenter/vinfodb.html.
Denial of Service Attacks
Besides reconnaissance attacks, the second most common form of security threat and attack is the DoS attack. With a DoS attack, a hacker attempts to deny legitimate traffic and user access to a particular resource, or, at the very least, reduce the quality of service for a resource. Many kinds of DoS attacks exist; the simplest to implement is a flood attack, in which the hacker overwhelms a device or network with a flood of ICMP packets. The next two sections cover some common DoS attacks, as well as methods used to prevent these kinds of attacks.
Types of DoS Attacks
Hackers can use many types of DoS attacks against your network. Some of these affect the performance of a particular service running on a server, and some drastically can affect the performance of all the machines on a particular network segment. Because there are literally hundreds of DoS attacks, the following list is limited to some of the most common ones:
An application attack is simply an attack against an application running on a server. Hackers typically attack such popular applications as Microsoft's IIS web server, web browsers such as Microsoft Internet Explorer and Netscape Navigator, and e-mail applications such as Sendmail and Microsoft Exchange and Outlook because of their widespread use. Hackers try various methods, such as buffer overruns and e-mail bombs, to disable a system or to send information back to the hacker to be used for other types of attacks.
An e-mail bomb is a form of an attack that a hacker uses to tie up e-mail resources on your system or possibly even compromise the security of your e-mail server. An unsophisticated hacker typically sends large messages to your e-mail server, hoping to fill up the disk space and crash it. A sophisticated hacker, on the other hand, includes Trojan horses, viruses, or worms that either are embedded in the e-mail or are included as an attachment. If a user activates these, they can cause damage to your system or open a security hole that will allow a hacker into the networking device.
CPU hogging is a type of attack that affects the CPU cycles of a service. This is a general category of a DoS attack in which more specific attacks, such as packet fragmentation or chargen, are used.
Chargen is a character generator that produces serialized character output. Typically, chargen uses UDP, but it can be implemented with TCP. Chargen runs on port 19 and usually is enabled on most operating systems. Hackers sometimes send garbage data to this port, hoping that your resource will process this information and thus take away CPU cycles from other legitimate processes on the resource.
A packet fragmentation and reassembly attack is an ingenious attack in which a hacker sends hundreds of fragments to a destination service, hoping that the destination device will perceive these as valid connections and thus waste both buffer space and CPU cycles to process them. A good hacker makes this flood of fragments appear as a set of legitimate connections, which can cause a buffer overrun on the destination and possibly crash the machine. Even if the machine does not crash, the hacker is tying up buffer space, which prevents legitimate traffic from being processed.
Land.c is a program that sends TCP segments to a destination where both the source address and destination are the same in the packet. Upon receiving the packet, the destination tries to forward the packet to itself. To make it even more confusing for the destination device, the packet might contain the same port number for both the source and the destination. In some instances, this can cause the device to try repeatedly to establish connections to itself, tying up resources.
Hackers sometimes use Java or ActiveX scripts to create malicious applets. When downloaded to user's desktop, these applets sometimes can damage the user's file system or send information back to the hacker that he then can use to attempt further attacks.
A ping of death attack is one of my favorite attacks because of its simplistic beauty. A hacker sends a single ICMP message with an offset field indicating that the data is larger than 65,535 bytes. On some systems, this crashes the device. When this bug was discovered, for a period of two or three days, many companies were disconnecting their connection to the Internet to prevent hackers and curious people from bringing down their resources.
One of the most difficult attacks to implement is an attack on your router's routing protocols, called a rerouting attack. In this type of attack, a hacker tries to feed your routers with either bad routing information that will cause your packets to be routed to a dead end, or misinformation that will cause your packets to be routed back to the hacker so that he can perform eavesdropping and use this information to execute another attack. Typically, a hacker uses a protocol analyzer and special software to implement this type of attack.
TCP SYN flood attacks occur when a hacker floods a particular service with TCP SYN segments without any intent of completing the connection. With this kind of attack, the hacker basically is tying up the connection resources on a particular server.
Smurf attacks occur when a hacker sends ICMP traffic to a destination (a directed broadcast address) but replaces its own source IP address in the packet header with the IP address of the device that it wants to attack. When the ICMP traffic reaches the destination network, the devices respond to the spoofed source address, which is the device that the hacker wants to flood.
WinNuke is a program that was developed to take advantage of a bug in certain versions of Microsoft operating systems, including 95, 98, Me, XP, NT, and 2000. The hacker sends out-of-band information to port 139, hoping to bring down the server.
An enhanced form of DoS attacks are Distributed DoS (DDoS) attacks. With a DDoS attack, a hacker subverts or controls multiple sources and uses these sources to attack one or more destinations. Tracing the culprit in these kinds of attacks can be difficult, especially if the hacker is using many different ISPs as the source of the attack. For more information on common DDoS attacks and tools, visit Dave Dittrich's site at http://staff.washington.edu/dittrich/misc/ddos/.
DoS Attack-Prevention Methods
Just as hackers use many DoS attacks to hamper your network's performance, you can use many solutions to prevent or at least hinder a hacker's DoS attack. The following are common solutions used to detect and prevent DoS attacks:
Performing packet filtering
Using an intrusion-detection system (IDS)
Using routing protocols with authentication
Running detailed audits and logs
The first solution that you should implement is filtering. You can use something as simple as ACLs on a Cisco router, or you can use a firewall system such as the PIX or the Cisco IOS Firewall feature set available on Cisco routers. The Cisco IOS Firewall feature set supports a feature called Context-based Access Control (CBAC), which implements a firewall system on a router. To protect yourself from malicious applets, you should use a firewall system, such as the Cisco IOS router or PIX, to filter Java and ActiveX scripts and applets. CBAC is discussed in Chapter 9, "Context-Based Access Control."
You also should consider using an IDS. An IDS solution examines traffic and, based on its contents, classifies the traffic as either an attack or not an attack. One large advantage of using an IDS is that these can detect reconnaissance attacks and probes, alerting you to the fact that possible hacking problems are looming. More sophisticated IDS solutions even can interact with your network equipment, such as routers and firewalls, and automatically configure them to filter the offending traffic when it is detected. Cisco has a range of IDS solutions, which enable you to implement a feature called IP blocking or shunning. With IP blocking, when a Cisco IDS detects an attack, it can log into a Cisco PIX or router and add a temporary filtering rule to block the attack. IDS and IP blocking are discussed in Chapter 16, "Intrusion-Detection System."
To prevent routing attacks, you can use a routing protocol that has built-in authentication, such as RIPv2, EIGRP, OSPF, IS-IS, or BGP. These use the MD5 hashing algorithm, which creates a unique digital signature that is added to all routing information. The MD5 hashing algorithm, which also is used by PPP's CHAP and by IPSec's AH and ESP, is discussed in Chapter 19, "IPSec Site-to-Site Connections." You also might want to configure filters to allow routing update traffic from only certain routing sources; however, if the hacker is smart about this process, he typically changes the source address to match an address that is specified in your allowed list. If your router is located at the perimeter of your network, you might want to consider using static routes instead of using a dynamic routing protocol. Routing protocol protection is discussed in Chapter 15, "Routing Protocol Protection."
At the very least, your networking equipment should keep extensive audits and logs to keep track of security issues. You should peruse these periodically, looking for DoS attacks. Or, if you are smart, you will use a system that parses the logs and does all of this work for you. Logging is discussed in Chapter 18, "Logging Events."
NOTE
For more information on DoS attacks, visit http://www.infosyssec.com/infosyssec/secdos1.htm.







