Security Solutions
It is beyond the scope of this book to cover every type of security solution that is available on the market. This section covers some basic solutions that you should be aware of, as well as a security checklist to help strengthen your company's network security. The rest of this book focuses on the Cisco IOS routers for firewalls in implementing security in your network.
Designing a Security Solution
As you have seen throughout this chapter, a hacker can cause damage to your network in many ways (and this chapter barely skims the surface on the different kinds of attacks that your network will face). Therefore, you need to design a solid security solution to deal with these threats. This solution also should be easy to maintain and should be flexible enough to handle changes in your network. Here is a simple checklist that should describe your security solution:
It should be easy to use and implement? It also should be easy to monitor and maintain. If a security solution is complex, with a lot of configuration tasks to perform and management systems to monitor, you might be making your security worse. Misconfigurations easily can create security holes, and if you have too many management platforms to monitor, the administrators might miss key events or might become lax in their monitoring duties.
It should enable your company to develop and deploy new applications in your network? In other words, you should not have to change your security system completely to accommodate new applications. Remember that your security solution should meet the outline created in your security policy, and your security policy should allow your company to meet the goals that were developed in its business plan.
It should enable your company to use the Internet in a secure manner? The company should feel secure that its key resources are protected and that the Internet can be used to further the company's business goals.
NOTE
Chapter 2 goes into more depth on developing a security solution, particularly the roles that firewalls play in protecting your network and different design philosophies in the use of firewalls.
The Cisco Security Wheel
As you quickly will learn, network security is not a one-time implementation. You do not implement your security solution and walk away from it. Instead, network security is a continuous process that is built around your company's security policy. Cisco developed a concept called the security wheel that outlines a four-step process that is repeated continuously. Here are the four steps in the security wheel, shown in Figure 1-5:
- Secure your network.
- Monitor your network's security.
- Test your network's security.
- Improve your network's security, based on your monitoring and testing results in Steps 2 and 3.
Figure 1-5. Cisco Security Wheel
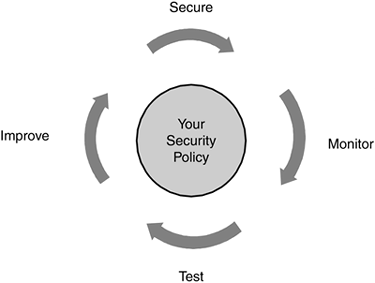
The next four sections cover these four steps in more depth.
Secure Your Network
In the first step, you should do what is necessary to secure your network. This includes many of the prevention methods that I mentioned in this chapter, but it also includes physical security (locking up key components and removing the likelihood that users or strangers physically can get their hands on key resources in your network). Some of the solutions that you might consider implementing are authenticating through the use of one-time passwords, smart cards, and authentication servers; using firewalls to filter traffic; using VPNs to encrypt your traffic; and keeping up-to-date on security holes in your equipment and ensuring that they have the latest security patches applied. Chapter 2 goes into the design philosophy in a lot more depth.
Monitor Your Security
When you have put your security solution in place, your next step is to monitor your network to ensure that no security breaches take place. One very common tool that many companies use is an IDS. These devices enable you to monitor traffic and look for attacks, alerting you through a management station, e-mail, or a pager for a quick response. A security solution is no good if you do not monitor it.
Importance of MonitoringAs an example of the importance of monitoring, I was hired by a company to redesign its network, and one of the components of the design included the existing Internet connection. In the current network, the company had contracted with its ISP to handle all of the security functions. This basically consisted of a firewall sitting at the ISP's site that was responsible for basic filtering functions. Even though the company was trying to save money by taking this approach, I strongly warned of the kinds of problems this could create. About a month later, I was fooling around on the Internet back at my office when, out of curiosity, I tried to access a UNIX server sitting at this company's site. I was somewhat surprised when I got a Telnet prompt. I then proceeded to check what other resources were available to me. I was able to access every single resource in the company's network, including the IBM mainframe. What made this situation worse is that this was a medical facility containing information about people and patients. I immediately notified the data center administrator, and he was absolutely furious with the ISP. Apparently, the ISP had made some changes in the network topology and moved the firewall, never testing whether the move impacted the security of the companies that it was supposed to protect. The CIO of this company learned a very valuable lesson that day: When it comes to security, do not trust other people to do it for you. Fortunately, no hackers noticed this major breach in security, and no harm came of it. As you can see, vigilance in your monitoring duties is extremely important. |
Test Your Security
As the previous sidebar example points out, it is also important to follow the third step: Test your security periodically. The company in my example should have been at least attempting certain kinds of tests on the ISP's security periodically, not just to verify that its assets are protected, but also to ensure that the money that it is paying the ISP is being well spent. These tests should include reconnaissance attacks (network scanning and port probing), as well as checks on the security logs of networking devices.
Improve Your Security
The last step is to examine the results of your monitoring and testing events, and use this information either to make changes to your security system or to improve upon your security system. Likewise, you should use this information to make adjustments to your security policy.
After you have completed these four steps, your job is not over yet. Instead, you should go back to Step 1 and start over. You will repeat this process continually, adjusting your security policy and security solution to meet all existing and newly developing security threats.
Security Checklist
Internet Security Systems (ISS) has developed a similar concept to the Cisco security wheel. I have summarized it in the following security checklist:
Create a well-defined security policy that is complementary to your company's business objectives. | |
Create an easy-to-read security handbook that will be distributed to all of your employees, to help educate and train them in your company's security policies and procedures. | |
Adequately protect your mission-critical resources and services. | |
Develop a security plan of action that lays out what actions and responses your company will take if a security breach or problem occurs. | |
Develop a disaster-recovery plan that deals with the worst-case situations for security breaches, such as if a hacker reformats the hard drives on all of your web servers, or if an arsonist torches your company's headquarters. | |
Purchase damage insurance for the software and hardware that you own, in case an individual intentionally physically damages your company's computer and networking assets. You might even want to include insurance for lost data and downtime requirements to restore your system to its previous state. | |
Train your networking employees so that they can implement and monitor your proposed security solution. | |
Use an IDS to detect security attacks. | |
Use a firewall system to filter all unnecessary traffic as it comes into your network. | |
Use a VPN solution to protect data between sites and devices in a remote access network. | |
Implement a corporate-wide antivirus solution that incorporates your PCs, laptops, and file servers. | |
Disable all unnecessary services on your devices. |
This is not meant to be a comprehensive checklist, but it contains some of the basic things that you should be doing and implementing in your network. More information about ISS and their products can be found at http://www.internetsecuritysystems.com/.
Additional Information
If you are a novice to security, you will soon find that you have a lot to learn about security, threats, and solutions. To help you with this process, I have included some links to additional information that you will find useful:
For an overview of security, visit http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/security.htm.
For information about CERT and published security threats, visit http://www.cert.org.
For information concerning the security life cycle and checklist, visit this ISS document at http://documents.iss.net/whitepapers/securityCycle.pdf.
For an overview of Cisco security products, visit either of these two URLs:
- http://www.cisco.com/univercd/cc/td/doc/product/vpn/ciscosec/index.htm
- http://www.cisco.com/en/US/netsol/index.html
For an overview of Cisco security features, visit http://www.cisco.com/univercd/cc/td/doc/product/iaabu/newsecf/index.htm.
Other important security sites that I commonly use include these:
- http://www.infosyssec.com/
- http://www.securityfocus.com/








