Types of Security Threats
Now that you have a basic understanding of the kinds of weaknesses that you have to deal with in a security solution, this section turns to some of the many security threats that your network faces. As I mentioned earlier, your network might face thousands of threats daily. The Computer Security Institute (CSI) conducted a study on network security threats and security breaches and discovered that, out of all of the companies polled, 70 percent have had some type of security breach. These security threats can be categorized as external versus internal, and unstructured versus structured.
External and Internal Threats
Security threats can come from two locations:
External users
Internal users
An external security threat occurs when someone outside your network creates a security threat to your network. If you are using an intrusion-detection system (IDS), which detects attacks as they occur, you probably will be mildly shocked at the number of probes and attacks that occur against your network daily.
An internal security threat occurs when someone from inside your network creates a security threat to your network. Interestingly, the CSI study has found that, of the 70 percent of the companies that had security breaches, 60 percent of these breaches come from internal sources. Some of these security breaches were malicious in intent; others were accidental. Therefore, you should not just be concerned about protecting the perimeter of your network, you should also aim to protect every key resource and service. This topic is discussed in more depth in Chapter 2, "Introduction to Firewalls."
CAUTION
Most security threats are internal. Therefore, when you design a security solution, you must address this issue by using internal measures to protect important resources.
Unstructured and Structured Threats
General methods of security threats fall under two categories:
Unstructured threats
Structured threats
An unstructured security threat is one created by an inexperienced person who is trying to gain access to your network?a wannabe hacker. A good security solution easily should thwart this kind of attack. Many tools available to anyone on the Internet can be used to discover weaknesses in a company's network. These include port-scanning tools, address-sweeping tools, and many others. Most of these kinds of probes are done more out of curiosity than with a malicious intent in mind. This is especially true of internal users who are interested in what kinds of devices exist in their own network.
A structured security threat, on the other hand, is implemented by a technically skilled person who is trying to gain access to your network. This hacker creates or uses some very sophisticated tools to break into your network or to disrupt the services running in your network. A good example of a structured attack is a distributed ICMP flood. A person with very little hacking skill probably would send a flood of pings from the same source machine, making it fairly easy to track down the culprit. A sophisticated hacker, on the other hand, will try to hide the source of the ICMP packets by changing the source address inside the packets (called spoofing), as well as executing the attack from several different sources. Tracking down the culprit of this kind of attack takes a lot of work and patience.
Figure 1-2 shows a simple example of a sophisticated spoofing attack. In this example, the hacker changes the source address in ICMP packets to those of Server C, which is the device that the hacker is attacking. He sends these packets to both Server A and Server B.
Figure 1-2. Sophisticated Spoofing Attack
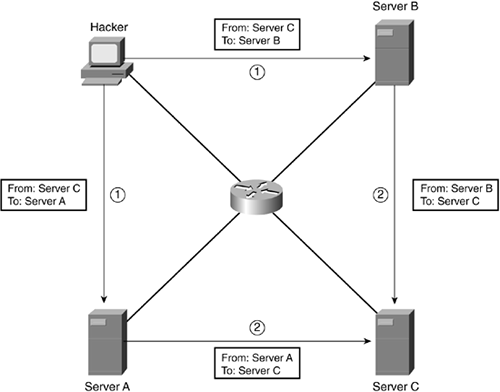
These servers respond to the ICMP messages to the destination listed as the source in the packets, Server C. In this example, with the hacker flooding packets to both Server A and Server B, which, in turn, hit Server C twice as hard, it becomes more difficult, from Server C's perspective, to figure out who the real culprit of the attack is: the hacker.
NOTE
Even though you might be able to determine both the source (external versus internal) and the type of attack (structured versus unstructured), you should take each event seriously.







