CBAC Examples
DoS detection and prevention with CBAC is discussed in Chapter 17. Here I take a look at some examples of using CBAC for inspection and stateful filtering. Each example has four basic configuration components:
Defining an extended ACL(s) to filter traffic
Applying the extended ACL(s) on the appropriate interface(s)
Defining an inspection rule(s) to allow returning traffic
Applying the inspection rule(s) to the appropriate interface(s)
You need to configure many other things to secure the router in this example; however, these examples focus on only the previous four core elements in setting up stateful filtering.
Simple Example
Example 9-8 uses three simple inspection rules for TCP, UDP, and ICMP.
Example 9-8. Setting Up a Simple CBAC Inspection Configuration
Router(config)# ip access-list extended EXTERNAL-ACL Router(config-ext-nacl)# deny tcp any any log Router(config-ext-nacl)# deny udp any any log Router(config-ext-nacl)# deny icmp any any log Router(config-ext-nacl)# deny ip any any Router(config)# ip inspect name CBAC-EXAMPLE tcp Router(config)# ip inspect name CBAC-EXAMPLE udp Router(config)# ip inspect name CBAC-EXAMPLE icmp Router(config)# interface ethernet0 Router(config-if)# ip access-group EXTERNAL-ACL in Router(config-if)# ip inspect CBAC-EXAMPLE out
In this example, EXTERNAL-ACL is an extended IP ACL that denies all IP traffic. I put in the specific deny statements to log the denied TCP, UDP, and ICMP packets. Also notice that there is no reference to CBAC in the ACL; this is not necessary because CBAC dynamically adds entries at the top of the ACL to allow returning traffic. This is true of a Cisco IOS before FAB; however, with FAB, the Cisco IOS uses the state table to process returning traffic and then the static ACL on the returning interface. Without CBAC, the ACL in this configuration would drop all traffic trying to enter the ethernet0 interface.
Below this are three inspection statements for the rule group called CBAC-EXAMPLE: All TCP, UDP, and ICMP traffic is inspected. Ethernet0 is the external interface, where the external ACL is applied inbound and the inspection rules are applied outbound. With this configuration, CBAC knows that inspected traffic leaving the router has dynamic ACL entries automatically added to the top of the applied inbound external ACL (again, before FAB).
NOTE
From my perspective, the configuration of CBAC is simpler than that of RACLs. With RACLs, you need two ACLs, and the placement of the reflect and evaluate entries in the internal and external ACL is critical. With CBAC, you need to worry about only one ACL, and you do not have to worry about where the temporary ACL entries are placed; CBAC takes care of this automatically before FAB or uses the state table only to allow returning traffic with FAB.
To illustrate this further, imagine that an internal user (192.168.1.100) Telnets to an external device (192.168.2.2). Example 9-9 shows the verification on the router of this process.
Example 9-9. State Table Example Using the Configuration in Example 9-8
Router# show ip inspect sessions Established Sessions Session 82040F2C (192.168.1.100:1289)=>(192.168.2.2:23) tcp SIS_OPEN
As you can see, an entry was added to the Cisco IOS state table for the Telnet connection. Example 9-10 shows the display of the ACL information.
Example 9-10. The ACL, Before FAB, Using the Configuration in Example 9-8
Router# show ip access-list Extended IP access list EXTERNAL-ACL permit tcp host 192.168.2.2 eq telnet host 192.168.1.100 eq 1289 (18 matches) 10 deny tcp any any log 20 deny udp any any log 30 deny icmp any any log 40 deny ip any any
As you can see, the very first line of the ACL is the dynamic Telnet entry that CBAC added from the state table.
NOTE
Before FAB, you see the dynamic ACL entries at the top of the ACL on the returning interface; however, with FAB, you see only the ACL entries that you have configured manually. With FAB, the router uses the state table to allow returning traffic and the ACL to filter other traffic. Even for me, this takes some time to get used to because I always am looking for the temporary dynamic ACL entries to verify the operation of CBAC. With FAB, you need to examine the CBAC state table to verify its operation.
Two-Interface CBAC Example
Figure 9-10 illustrates how to use CBAC in a router that has two interfaces. This example is the same one used in Chapter 8, "Reflexive Access Lists." However, I configure CBAC instead of using RACLs to implement the stateful filtering.
Figure 9-10. Two-Interface CBAC Example
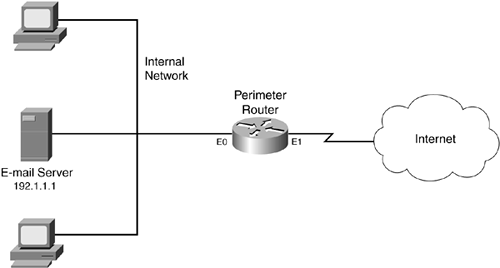
In this example, the network has two policies: allow Internet traffic to the internal e-mail server, and allow users access to the Internet. To accomplish this, you need an ACL configuration, such as the following:
Allow all internal users access to the Internet
External ACL (apply inbound on E1):
- Allow returning traffic from the Internet to the internal users
- Allow Internet traffic to the e-mail server
- Deny all other traffic
Example 9-11 shows the configuration to enforce these policies.
Example 9-11. Using CBAC to Implement Policies on a Two-Interface Router
Router(config)# ip access-list extended external_ACL Router(config-ext-nacl)# permit tcp any host 192.1.1.1 eq smtp Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# ip inspect name CBAC smtp Router(config)# ip inspect name CBAC tftp Router(config)# ip inspect name CBAC ftp Router(config)# ip inspect name CBAC http Router(config)# ip inspect name CBAC realaudio Router(config)# ip inspect name CBAC tcp Router(config)# ip inspect name CBAC udp Router(config)# ip inspect name CBAC icmp Router(config)# ip inspect tcp idle-time 300 Router(config)# interface ethernet1 Router(config-if)# ip inspect CBAC out Router(config-if)# ip access-group external_ACL in
In this example, the external_ACL allows only e-mail traffic to be sent to the internal e-mail server (192.1.1.1). All other traffic, by default, is denied. Following the ACL are the inspection rules for the inspection group called CBAC. In this example, TCP, UDP, ICMP, SMTP, TFTP, FTP, HTTP, and RealAudio traffic is being inspected. Next, the TCP idle timer for idle TCP connection has been changed from 3600 seconds to 300 seconds (5 minutes). Finally, the ACL and CBAC are activated on the router's external interface (ethernet1). As you can see from this example, the configuration is straightforward.
Three-Interface CBAC Example
Figure 9-11 illustrates how to use CBAC in a router that has three interfaces. This is the same three-interface example used in the last chapter, where RACLs were used to implement a stateful firewall filtering function. Here is a review of the policies discussed in the last chapter for this network:
The Internet should be capable of accessing the DMZ e-mail server.
The Internet should be capable of accessing the DMZ DNS server.
The Internet should be capable of accessing the DMZ web server.
The Internet should not be capable of accessing the internal network.
The internal e-mail server should be capable of accessing only the DMZ e-mail server, nothing else.
The DMZ e-mail server should be capable of accessing the internal e-mail server to forward mail.
Internal users should be able to access the Internet and receive replies.
Internal users should not be able to access the DMZ e-mail server or any external e-mail servers.
Figure 9-11. Three-Interface CBAC Example
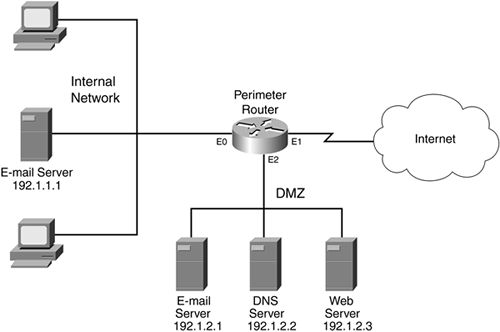
To accomplish these policies, you need three ACLs:
Internal ACL (apply inbound on E0):
- Allow internal e-mail server to access DMZ e-mail server
- Deny internal users to access the DMZ e-mail server and other e-mail servers
- Deny internal e-mail server from accessing anything else
- Allow internal users to access all other services (DMZ and Internet)
- Examine outbound traffic and build the state table entries for new sessions to the DMZ (not a part of the ACL, but part of the CBAC inspection process)
- Examine outbound traffic and build the state table entries for new sessions to the Internet (not a part of the ACL, but part of the CBAC inspection process)
DMZ ACL (apply inbound on E2). This restricts traffic from the DMZ to the internal network and the DMZ to the Internet:
- Allow the DMZ e-mail server to send e-mail to the internal server
- Allow the DMZ e-mail server to send e-mail to external e-mail servers
- Allow the DMZ DNS server to query other DNS servers
- Examine DMZ-related traffic to allow returning traffic from the DMZ to the internal and Internet users (not a part of the ACL, but part of the CBAC inspection process)
External ACL (apply inbound on E1):
- Allow Internet users access to the DMZ e-mail server
- Allow Internet users access to the DMZ DNS server for DNS queries
- Allow Internet users access to the DMZ web server
- Examine the traffic sent from the internal network and the DMZ e-mail server to be returned (not a part of the ACL, but part of the CBAC inspection process)
As you can see from the previous list of policies, setup of the ACLs and CBAC is a lot more difficult than in the two-interface CBAC example:
You need three ACLs: one to restrict traffic coming into the network, one to restrict traffic from the users to the DMZ, and one to restrict traffic from the DMZ to the Internet
You need a minimum of one, and possibly three, inspection rules, depending on what must be inspected from which interface.
Example 9-12 shows the configuration to enforce these policies.
Example 9-12. Using CBAC to Implement Policies on a Three-Interface Router
Router(config)# ip access-list extended internal_ACL Router(config-ext-nacl)# permit tcp host 192.1.1.1 (1) host 192.1.2.1 eq smtp Router(config-ext-nacl)# deny tcp any any eq pop (2) Router(config-ext-nacl)# deny tcp any any eq smtp Router(config-ext-nacl)# deny ip host 192.1.1.1 any (3) Router(config-ext-nacl)# permit ip any any (4) Router(config-ext-nacl)# exit Router(config)# Router(config)# ip inspect name internal_CBAC smtp audit-trail on (5) Router(config)# ip inspect name internal_CBAC ftp Router(config)# ip inspect name internal_CBAC http Router(config)# ip inspect name internal_CBAC realaudio Router(config)# ip inspect name internal_CBAC tcp Router(config)# ip inspect name internal_CBAC udp Router(config)# ip inspect name internal_CBAC icmp Router(config)# Router(config)# ip access-list extended DMZ_ACL Router(config-ext-nacl)# permit tcp host 192.1.2.1 any eq smtp (6) Router(config-ext-nacl)# permit udp host 192.1.2.2 any eq dns (7) Router(config-ext-nacl)# exit Router(config)# Router(config)# ip inspect name DMZ_CBAC smtp audit-trail on (8) Router(config)# ip inspect name DMZ_CBAC http Router(config)# ip inspect name DMZ_CBAC tcp Router(config)# ip inspect name DMZ_CBAC udp Router(config)# Router(config)# ip access-list extended external_ACL Router(config-ext-nacl)# permit tcp any host 192.1.2.1 eq smtp (9) Router(config-ext-nacl)# permit udp any host 192.1.2.2 eq dns Router(config-ext-nacl)# permit tcp any host 192.1.2.3 eq http Router(config-ext-nacl)# exit Router(config)# Router(config)# ip inspect name external_CBAC smtp (10) audit-trail on Router(config)# ip inspect name external_CBAC ftp Router(config)# ip inspect name external_CBAC http Router(config)# ip inspect name external_CBAC realaudio Router(config)# ip inspect name external_CBAC tcp Router(config)# ip inspect name external_CBAC udp Router(config)# ip inspect name external_CBAC icmp Router(config)# Router(config)# interface ethernet0 (11) Router(config-if)# description Internal Network Router(config-if)# ip access-group internal_ACL in Router(config-if)# ip inspect internal_CBAC in Router(config-if)# exit Router(config)# interface ethernet2 (12) Router(config-if)# description DMZ Router(config-if)# ip access-group DMZ_ACL in Router(config-if)# ip inspect DMZ_CBAC in Router(config-if)# exit Router(config)# interface ethernet1 (13) Router(config-if)# description Internet Router(config-if)# ip access-group external_ACL in Router(config-if)# exit Router(config)# ip inspect tcp synwait-time 15 (14) Router(config)# ip inspect tcp idle-time 120 Router(config)# ip inspect udp idle-time 20
The following is an explanation of Example 9-12, with reference to the numbering on the right side of the example:
internal_ACL is used to filter traffic from the internal segment (connected to ethernet0). The first statement in this ACL allows the internal e-mail server to send e-mail to the DMZ e-mail server.
This statement forces the internal clients to send e-mail through the internal e-mail server. In addition, the statement following this one prevents all e-mail connections, minus the e-mail connection listed in the first statement.
This statement prevents the internal e-mail server from accessing any other device.
All other access from the internal segment to other devices is allowed.
The internal_CBAC inspection rules are used to allow traffic for returning sessions to the internal users. In this example, the administrator has determined the protocols that internal people use and has configured the appropriate inspection statements. Notice that the audit trail function has been enabled for SMTP inspection. This is done to provide more information about SMTP connections and possible attacks.
The second ACL, DMZ_ACL, is used to filter traffic from the DMZ segment. By default, only two connections are allowed. In this first statement, the DMZ e-mail server is allowed to send e-mail to any e-mail server, including the internal e-mail server and Internet e-mail servers.
In the second ACL statement, the DMZ DNS server is allowed to forward DNS queries to other DNS servers.
In the second inspection rule set for CBAC, inspection is set up for traffic entering the DMZ segment, allowing for the return of traffic from the DMZ to the internal and Internet segments. Notice that the number of inspection statements is smaller because the applications running on the DMZ are limited.
This third ACL is used to filter traffic from the Internet that is trying to access internal resources. Only three statements are configured, allowing access to the DMZ e-mail server, the DMZ DNS server, and the DMZ web server.
The third set of CBAC inspection rules allows returning traffic that originally exited the Internet interface. Actually, you could have used the same inspection rule set that I did for the internal interface. However, this adds overhead because some of the traffic is internal to the DMZ, and you do not want these temporary ACL entries to show up on the external interface.
This interface is connected to the internal segment and has internal_ACL activated on it as well as the CBAC inspection rule for the internal traffic.
This interface is connected to the DMZ segment and has DMZ_ACL activated on it as well as the CBAC inspection rule for the DMZ traffic.
This interface is connected to the external (Internet) segment and has external_ACL activated on it.
The last set of three statements changes the default idle timeout for connections. The first statement reduces the TCP setup time from 30 to 15 seconds. The second statement reduces the TCP idle timeout from 3600 to 120 seconds (2 minutes). In the third statement, the UDP idle timer is reduced from 30 to 20 seconds.
If you compare this example to the three-interface example in Chapter 8, this example is much cleaner and easier to implement. This is one of the main reasons administrators prefer to use CBAC instead of RACLs.
CBAC and RACLsWhen CBAC was introduced, I became a happy convert from the use of RACLs. I originally started building packet-filtering firewalls in the early to mid-1990s. These could filter only on basic Layers 3 and 4 information in a packet. One huge limitation of these filters is that they are good for filtering traffic in one direction but are horrible at filtering traffic in two or more directions. When Cisco introduced RACLs, they provided decent bidirectional filtering. Unfortunately, you had to be a guru in converting your policies to ACLs, especially if you needed to filter traffic among more than two interfaces, as you saw in my three-interface example in Chapter 8, "Reflexive Access Lists." I can remember spending days implementing complex filtering configurations with the help of packet sniffers. However, with the introduction of CBAC, this issue has been reduced greatly. Along with CBAC, the Cisco IOS Firewall feature set offers many features that enable you to harden your perimeter router and provide a tough defense against a determined hacker. Teaming the Cisco IOS Firewall feature set with other security products, you easily can create a scalable, secure perimeter defense. |







