Company Profile
The network shown in Figure 21-1 illustrates this case study. The company in this network has two sites?a corporate and branch office?as well as remote access users that connect through the Internet. The following sections discuss the necessary requirements for these components.
Figure 21-1. Case Study Network
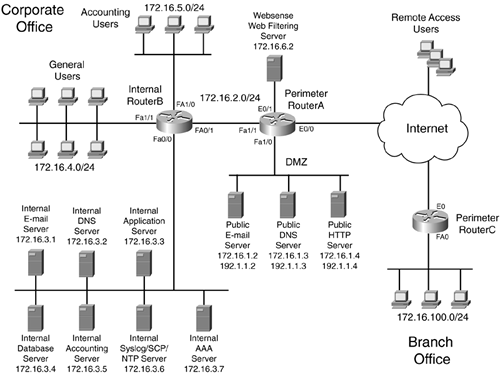
Corporate Office
The corporate office has five segments and two routers: RouterA, which is a perimeter router, and RouterB, which is an internal router. The following two sections cover the roles of the two routers and the network segments.
Perimeter Router
The perimeter router is RouterA and is a 3745. Because of security issues, secure access to this router should be set up and restrictions should be placed on who can access this router. RouterA has three interfaces. E0/0 connects to the company's ISP through a cable-modem connection. It is assigned an IP address of 192.1.1.1. The 192.1.1.0/24 network has been assigned by the ISP to this company, but two of these addresses must be used between this company and the ISP. In this case, 192.1.1.1 is assigned to RouterA, and 192.1.1.254 is assigned to the ISP's router.
FA1/0 connects to the company's DMZ segment. This segment houses a public e-mail server, a DNS server, and an HTTP server. All of these devices have a private address from the network 172.16.1.0/24; however, the perimeter router performs address translation so that these are reachable from users on the Internet.
All internal users should be able to access the DMZ devices and the Internet. However, the company is concerned about web surfing. Interface E0/1 on the perimeter router is a dedicated connection to a content-filtering device.
The public e-mail server acts as a bridge between the internal e-mail server and the SMTP e-mail servers on the Internet. This company uses a standard SMTP e-mail software package and is concerned about the security of the server.
The public DNS server resolves DNS names of the DMZ devices for Internet users. In other words, it resolves the names of the DMZ devices to 192.1.1.x addresses. Note that no internal devices use this DNS server for resolution to access other internal devices. In other words, an internal device would use the internal DNS server when accessing DMZ devices.
The public web server houses public web page information for Internet users, as well as a small e-commerce section where the company sells a few e-book documents. Because of issues of security with the online transactions, SSL is used to transmit an Internet user's personal credit card information (both HTTP and HTTPS are used for access to this server).
Interface FA1/1 of the perimeter router connects to the internal router. The network number used is 172.16.2.0/24. The only two devices on this segment are the two routers.
Internal Router
The perimeter router has a dedicated connection to the internal router, also a 3745, on subnet 172.16.2.0/24. The internal router is responsible for interconnecting the company's internal segments at the corporate site, as well as implementing traffic-flow policies. This router should restrict access to the EXEC shell and use a secure method of access.
The FA0/0 interface of this router connects to the company's server farm, where there are seven servers. An internal e-mail server handles the distribution of all internal e-mail of the users and is a forwarding point of e-mail to the public e-mail server on the DMZ. The DMZ then handles any type of Internet e-mail access.
An internal DNS server handles resolution for all internal devices. However, if the name to be resolved is not an internal device (at either the corporate or branch office sites), the internal DNS server forwards the name-resolution request to the appropriate server.
The internal application server is used as a repository of the company's applications. The more critical applications used by company employees are located on this server. The front end is an HTTP with secure socket layer (HTTPS) web server for these applications. The internal database server is used by most users in the company and holds the data used by the company's critical applications on the internal application server. Access to this server should be restricted to only the application server.
The accounting department's server also is located on this segment. Because of the sensitive nature of this information, care must be taken in who can access this server. The application that runs on this server uses a nonstandard port (TCP 2501) for network access.
The syslog/SCP/NTP (secure copy) server handles remote logging for devices, including the three routers: RouterA, RouterB, and RouterC. It also uses SCP to store configurations and images of devices. This server also serves as the master time source for the network. The last server on the server farm segment is a Cisco Secure ACS AAA server. It handles all AAA functions for the network, including router access.
Two other network segments are connected to this router. Interface FA1/0 is connected to the accounting users. These users need access to all servers in the server farm except the syslog server. Interface FA1/1 is connected to the general user population. These users should be able to access all of the servers in the server farm except the accounting and syslog servers. These users should not be able to access the accounting user segment.
Branch Office
This company has one branch office, which has an existing Internet connection through a 1721 router and a cable modem setup. To save money, the company wants to use a VPN to connect the branch office to the corporate office site. The branch office has only users; all servers are located at the corporate site. Because of security issues, all branch-office traffic must be sent to the corporate site through the VPN before going anywhere else. Because there are only a few dozen users at this site, this will not cause a performance issue. An ISDN dialup connection between these two sites serves as a backup if the cable modem connection fails (the configuration of this is not covered in the case study).
Remote-Access Users
Some of the company's personnel work at home in the evenings, and a few salespeople also work on the road a lot. Because of these issues, a VPN is needed to provide a secure connection between these users to the corporate site through the Internet. Local LAN and Internet access should be allowed for these users, but a software firewall should be installed on their PCs, and all traffic sent to the corporate site should be protected. Remote-access users will be using the subnets 172.16.252.0/24 (network administrators), 127.16.253.0/24 (accounting users), and 172.16.254.0/24 (general users).







