Address Translation and Redundancy
One of the concerns with any network design is redundancy. The Cisco IOS provides two methods of redundancy for address translation:
Static NAT redundancy with Hot Standby Router Protocol (HSRP), available Cisco IOS in 12.2(4)T
Stateful address translation failover, available in Cisco IOS 12.2(13)T
The following sections cover both of these methods.
Static NAT Redundancy with HSRP
Static NAT redundancy with HSRP typically is used in a small network, usually with one subnet or network number, that is connected to two perimeter routers for redundancy. In this situation, the concern is providing redundancy for the internal servers that have private addresses; the perimeter router is performing the address translation function. In a single-router design, if the router fails, external users cannot access the internal resources. To provide redundancy, a second router is added. However, if the primary router fails, the secondary router needs to know that it must perform address translation. This is accomplished using HSRP.
HSRP Redundancy Process
When using HSRP to provide static NAT redundancy, the static NAT configuration is mirrored on the two routers, and the active router processes traffic. HSRP is configured on the default gateways in the subnet, with one configured as the active router and the rest as backup, or standby, routers. A virtual IP address is chosen and assigned to the routers. User devices send traffic to the virtual IP address, which is serviced by the active router. The other routers monitor the active router. If the active router fails, a standby router processes traffic. Note that only static NAT is supported in this configuration, not dynamic NAT; therefore, whatever static NAT commands you configure on the active HSRP router, you also need to configure on the standby router(s).
Look at Figure 12-5 to illustrate how this is set up. In this network, there are two routers. The top router is the active HSRP router, and the bottom one is the standby router. The virtual IP address is 10.0.0.254, which is the default gateway that internal devices use. If the active router fails, within 10 seconds, the standby router promotes itself and processes traffic sent to 10.0.0.254.
Figure 12-5. Static NAT HSRP Example 1
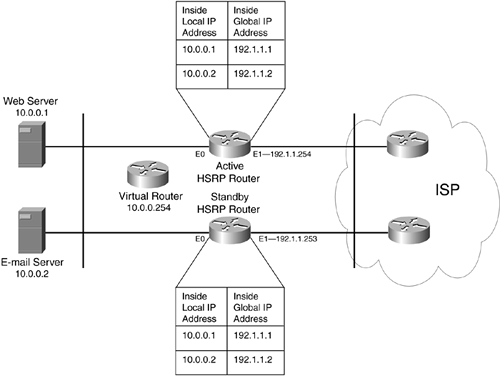
Assuming that the ISP assigned you 192.1.1.0/24 and that you had to use this for the external interfaces of your two routers, as shown in Figure 12-5, and also assuming that Internet traffic was trying to reach one of the two statically translated addresses, you have an issue with ARP. For example, assume that an external user was trying to reach 192.1.1.1, the web server. Because the ISP router is connected to 192.1.1.0/24, it performs an ARP for the MAC address of 192.1.1.1. Obviously, this device isn't on this segment; it's the web server at 10.0.0.1. In this situation, the active router responds to the ARP with its BIA address, basically performing a proxy function. Of course, this presents a problem if the active router fails and the standby router is promoted: The ISP still is using the BIA addresses of the active router (that no longer is functioning). To get around this problem, you manually must duplicate the static NAT entries on all HSRP routers, allowing a standby router to assume the responsibility when the active router fails.
NOTE
For the example in Figure 12-5, you must manually configure both sets of static NAT translations on the active and standby routers for failover to occur correctly.
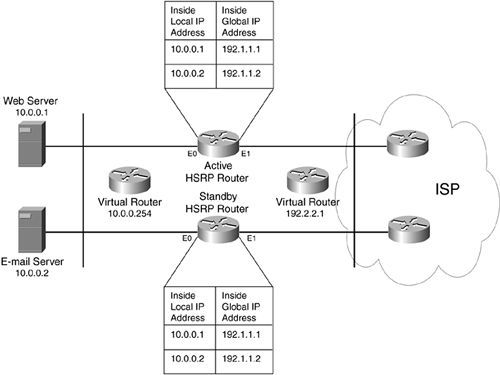
Of course, you might have a network design such as that shown in Figure 12-6. In this example, the network has been assigned 192.1.1.0/24 by the ISP, but the connection from this network to the ISP is using a different address space: 192.2.2.0/24. In this example, you can use HSRP to provide redundancy on both sides of the two redundant routers: on the internal network side and the ISP side. However, for this to function correctly on the ISP side, the ISP must set up a static route to the virtual router IP address. By default, the active router processes all traffic for this next-hop address; if it fails, the standby router promotes itself and processes traffic. But as in the previous example, both HSRP routers still need the same static NAT configuration to provide redundancy.
Figure 12-6. Static NAT HSRP Example 2
HSRP Redundancy Configuration
To set up static NAT redundancy with HSRP, you must perform two steps:
- Step 1. Configure HSRP.
- Step 2. Integrate your static NAT configuration with HSRP.
NOTE
I assume that you know how to configure HSRP, so I do not spend time discussing what the various HSRP commands are for, with the exception of how to integrate HSRP with static NAT.
You use these basic commands to configure HSRP:
Router(config)# interface type [slot_#/]port_# Router(config-if)# ip address IP_address subnet_mask (1) Router(config-if)# no ip redirects (2) Router(config-if)# standby [group_#] name [HSRP_group_name] (3) Router(config-if)# standby [HSRP_group_#] ip IP_address (4) Router(config-if)# standby [group_#] preempt Router(config-if)# standby [group_#] priority priority_# Router(config-if)# standby [group_#] track interface decrement_value
The only four required Interface commands are marked with numbers on the right side; the last two are optional.
After you have set up HSRP, you are ready to set up NAT. You use these commands to do this:
Router(config)# ip nat inside | outside source static local_IP_address global_IP_address redundancy HSRP_group_name Router(config)# interface type [slot_#/]port_# Router(config-if)# ip nat {inside | outside}
The one main difference with the configuration of static NAT is the addition of the redundancy parameter. The name of the HSRP group specified here must match the one configured with the standby name command.
After you have set up static NAT redundancy with HSRP, you can use the HSRP show standby and the address translation show ip nat translations verbose commands to verify that this feature is enabled.
HSRP Redundancy Example
Take a look at a configuration example when using HSRP to provide static NAT redundancy. This example uses the network shown previously in Figure 12-5, but it focuses only on the HSRP and address translation configuration. Example 12-6 shows the configuration for the active HSRP router.
Example 12-6. Using HSRP to Provide Static NAT Redundancy: Active Router
Router(config)# interface ethernet0 Router(config-if)# ip address 10.0.0.253 255.255.255.0 Router(config-if)# no ip redirects Router(config-if)# ip nat inside Router(config-if)# standby 1 ip 10.0.0.254 Router(config-if)# standby 1 priority 110 Router(config-if)# standby 1 preempt Router(config-if)# standby 1 name HSRPGROUP Router(config-if)# standby 1 track ethernet1 Router(config-if)# exit Router(config)# interface ethernet1 Router(config-if)# ip address 192.1.1.254 Router(config-if)# ip nat outside Router(config-if)# exit Router(config)# ip nat inside source static 10.0.0.1 192.1.1.1 redundancy HSRPGROUP Router(config)# ip nat inside source static 10.0.0.2 192.1.1.2 redundancy HSRPGROUP
In Example 12-6, the ethernet0 configuration sets up internal HSRP. At the bottom, notice that the static NAT commands are associated with the HSRP group name.
Example 12-7 shows the configuration for the standby HSRP router.
Example 12-7. Using HSRP to Provide Static NAT Redundancy: Standby Router
Router(config)# interface ethernet0 Router(config-if)# ip address 10.0.0.252 255.255.255.0 Router(config-if)# no ip redirects Router(config-if)# ip nat inside Router(config-if)# standby 1 ip 10.0.0.254 Router(config-if)# standby 1 priority 90 Router(config-if)# standby 1 preempt Router(config-if)# standby 1 name HSRPGROUP Router(config-if)# standby 1 track ethernet1 Router(config-if)# exit Router(config)# interface ethernet1 Router(config-if)# ip address 192.1.1.253 Router(config-if)# ip nat outside Router(config-if)# exit Router(config)# ip nat inside source static 10.0.0.1 192.1.1.1 redundancy HSRPGROUP Router(config)# ip nat inside source static 10.0.0.2 192.1.1.2 redundancy HSRPGROUP
Notice that the standby router manually had to replicate the two static NAT entries, located at the bottom of the configuration.
Stateful Address Translation Failover
The main problem with static NAT redundancy with HSRP is that it is not a stateful address translation solution: It provides redundancy only for static NAT translations. In other words, if you also are using dynamic address translation, all these translations are lost when the active router fails. This can cause connectivity problems.
Stateful Failover Features and Restrictions
Starting with Cisco IOS 12.2(13)T, Cisco introduced Phase 1 of its stateful address translation failover, referred to as stateful NAT (SNAT). This is Cisco's first step in implementing SNAT. In this solution, two address translation routers are used: a primary, and a backup or backups. These routers commonly are called a translation group. The primary router in the translation group performs active address translations. The backup accepts address translation updates (additions and deletions) from the primary and also checks to make sure that the primary is functioning. If the primary fails, the backup begins processing traffic using its address translation table that was shared with the primary. The address translation information is shared between the primary and backup routers by using a TCP connection.
SNAT even can work with HSRP; however, this process is different than the one described in the previous "Static NAT Redundancy with HSRP" section. Static NAT redundancy with HSRP provides redundancy for only static translation, not dynamic translation. With SNAT and HSRP, redundancy can be provided for both types of translations.
NOTE
SNAT provides redundancy for dynamic translations; to provide redundancy for static translations, configure the static translations on all routers in the translation group.
Currently, SNAT Phase 1 does not support ALG examination (embedding of addressing information). Therefore, certain applications, such as FTP, NetMeeting, RAS, SIP, Skinny, TFTP, and asymmetrical routing, will not work because they have embedded addresses in packet payloads. SNAT Phase 2 will address this limitation and provide additional redundancy and translation features.
SNAT with HSRP
SNAT can be configured in two ways: with HSRP and without it. The following two sections discuss how to configure both.
To configure SNAT with HSRP, you perform the following steps:
- Step 1. Configure HSRP.
- Step 2. Configure stateful failover.
- Step 3. Configure address translation.
HSRP Configuration
In Step 1, you configure HSRP, typically using these commands:
Router(config)# interface type [slot_#/]port_# Router(config-if)# ip address IP_address subnet_mask (1) Router(config-if)# no ip redirects (2) Router(config-if)# standby [group_#] name [HSRP_group_name] (3) Router(config-if)# standby [HSRP_group_#] ip IP_address (4) Router(config-if)# standby [group_#] preempt Router(config-if)# standby [group_#] priority priority_# Router(config-if)# standby [group_#] track interface decrement_value
The only four required Interface commands are marked here; the last three are optional. Whichever router becomes the active HSRP router processes traffic, adds and removes translations from the address translation table, and updates the other HSRP routers in the group.
HSRP with SNAT Stateful Failover Configuration
After you have set up HSRP, you are ready to set up your stateful failover:
Router(config)# ip nat stateful id router_ID_# Router(config-ipnat-snat)# redundancy HSRP_group_name Router(config-ipnat-snat-red)# mapping-id mapping_ID_#
The ip nat stateful id command specifies an identification of the router in the SNAT group. Each router that is participating needs a unique identification number. This number can range from 1 to 2,147,483,647. For example, if two routers will be participating in stateful failover address translation with HSRP, you can use the ID numbers of 1 and 2. The redundancy command specifies the name of the HSRP group providing the redundancy; this is configured with the standby name command on the router's interface. The mapping-id command specifies a number from 1 to 2,147,483,647, to uniquely identify the translations that the active HSRP router will send to the standby router(s). These commands must be configured on all routers in the HSRP group. The main difference in the configuration of the routers is that each router needs a unique router ID; otherwise, the HSRP group name and mapping ID number are the same.
HSRP with SNAT Address Translation Configuration
After you set up stateful failover for address translation, you can proceed with your address translation commands. For static translations, manually configure these on all routers in the HSRP group: Remember that stateful failover applies only to dynamic translations. Next, configure your dynamic translations using the first command and any of the following commands:
Router(config)# ip nat pool global_pool_name begin_IP_address end_IP_address prefix-length prefix_length Router(config)# ip nat inside source route-map route_map_name pool global_pool_name mapping-id mapping_ID_# [overload] Router(config)# ip nat inside source list ACL_#_or_name pool global_pool_name mapping-id mapping_ID_# [overload]
The ip nat pool command defines the global addresses that your local addresses will be translated to; this was discussed in the previous chapter and is a required command. The next two commands specify which local addresses, either through a route map or through an ACL number or name, are to be translated using the global pool. Based on your needs, you configure one of these last two commands. One additional parameter to these two commands is the mapping-id command, which tells the Cisco IOS that these dynamic translations are stateful translations. This number must match the mapping ID number in the mapping-id command in the ip nat stateful id configuration. The last thing you need to do is specify which interfaces are internal and external to the router for address translation by using the ip nat {inside | outside} Interface command.
HSRP and SNAT Stateful Failover Example
Take a look at an example that uses stateful address translation failover with HSRP. In the network shown in Figure 12-7, two routers are used to connect to the same ISP: RouterA and RouterB. This network will use dynamic PAT for the address translation from inside to outside connections.
Figure 12-7. Stateful Address Translation Failover with HSRP
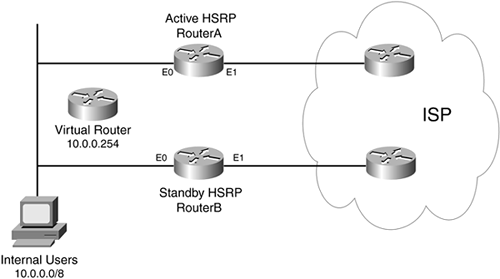
Example 12-8 shows the configuration for RouterA.
Example 12-8. Using PAT, HSRP, and SNAT on the Active Router
RouterA(config)# interface ethernet0 RouterA(config-if)# ip address 10.0.0.253 255.255.255.0 RouterA(config-if)# ip nat inside RouterA(config-if)# standby 1 ip 10.0.0.254 (1) RouterA(config-if)# standby 1 timers 1 3 RouterA(config-if)# standby 1 priority 150 (2) RouterA(config-if)# standby 1 name SNAT-HSRP (3) RouterA(config-if)# standby 1 track ethernet1 (4) RouterA(config-if)# exit RouterA(config)# interface ethernet1 RouterA(config-if)# ip nat outside RouterA(config-if)# exit RouterA(config)# ip nat stateful id 1 (5) RouterA(config-ipnat-snat)# redundancy SNAT-HSRP RouterA(config-ipnat-snat-red)# mapping-id 100 RouterA(config-ipnat-snat-red)# exit RouterA(config)# ip nat pool SNAT-POOL 192.1.1.240 192.1.1.254 (6) prefix-length 24 RouterA(config)# ip nat inside source route-map SNAT-MAP (7) pool SNAT-POOL mapping-id 100 overload RouterA(config)# route-map SNAT-MAP permit 10 (8) RouterA(config-route-map)# match ip address SNAT-ACL RouterA(config)# ip access-list extended SNAT-ACL (9) RouterA(config-ext-nacl)# permit ip 10.0.0.0 0.255.255.255 any
Refer to the numbers on the right side of Example 12-8 for the following explanation of the configuration for RouterA:
This command assigns the virtual IP address of the default gateway for the internal subnet.
This command ensures that RouterA becomes the active router. The default HSRP priority is 100, at which the router with the highest priority becomes the active router, and the next highest the standby.
This command configures the name of the HSRP group, which must match the redundancy command in Statement 5.
This command enables interface tracking on the outside interface. If this interface fails, RouterA demotes itself and allows RouterB to become the active router.
These three commands set up stateful failover for address translation. The router ID specified in the ip nat stateful command must be different from RouterB's. The redundancy command specifies the name of the HSRP group providing the redundancy. The mapping-id assigns a mapping number to the dynamic translation entries that will be shared with RouterB.
This command specifies the group of global addresses to be used in the translation.
This command specifies the local addresses that will be translated, states the global address pool to use for the translation, and specifies that SNAT is used (mapping-id) and that PAT is used for the translation (overload). Notice that this command references a route map for the local addresses.
These two commands specify that the named ACL SNAT-ACL is used to match on the local addresses.
This is the ACL that defines the local addresses that should be translated.
Example 12-9 shows the configuration for RouterB.
Example 12-9. Using PAT, HSRP, and SNAT on the Standby Router
RouterB(config)# interface ethernet0 RouterB(config-if)# ip address 10.0.0.252 255.255.255.0 RouterB(config-if)# ip nat inside RouterB(config-if)# standby 1 ip 10.0.0.254 RouterB(config-if)# standby 1 timers 1 3 RouterB(config-if)# standby 1 priority 90 (1) RouterB(config-if)# standby 1 name SNAT-HSRP RouterB(config-if)# standby 1 track ethernet1 RouterB(config-if)# exit RouterB(config)# interface ethernet1 RouterB(config-if)# ip nat outside RouterB(config-if)# exit RouterB(config)# ip nat stateful id 2 (2) RouterB(config-ipnat-snat)# redundancy SNAT-HSRP RouterB(config-ipnat-snat-red)# mapping-id 100 RouterB(config-ipnat-snat-red)# exit RouterB(config)# ip nat pool SNAT-POOL 192.1.1.240 192.1.1.254 prefix-length 24 RouterB(config)# ip nat inside source route-map SNAT-MAP pool SNAT-POOL mapping-id 100 overload RouterB(config)# route-map SNAT-MAP permit 10 RouterB(config-route-map)# match ip address SNAT-ACL RouterB(config)# ip access-list extended SNAT-ACL RouterB(config-ext-nacl)# permit ip 10.0.0.0 0.255.255.255 any
Notice that only two differences (besides IP addressing) exist between RouterB and RouterA's configuration. First, because RouterB is the standby router, it has a lower HSRP priority than RouterA (Statement 1); make sure that the standby router has a lower priority than the active one. Statement 2 configures RouterB's stateful address translation ID; this number must be different than RouterA's. Otherwise, the configuration is basically the same.
SNAT Without HSRP
SNAT without HSRP typically is used when the two perimeter routers are not handling default gateway functions for internal hosts (see Figure 12-8). As you can see in this example, the internal hosts are not connected to the two perimeter routers. The two perimeters routers have a direct connection between them, allowing for quicker detection of a failure, as well as dedicated bandwidth for the TCP connection used to share the dynamic address translation entries. An intelligent routing protocol is used to detect failure of the primary router.
Figure 12-8. Stateful Address Translation Failover Without HSRP
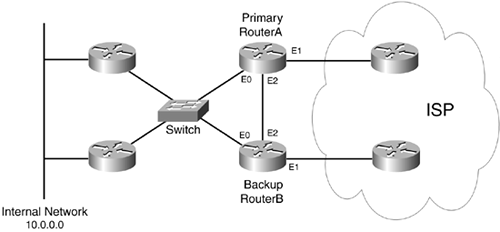
TIP
Typically, HSRP is used with stateful failover for address translation when the network is small and the users are connected to the same subnet as the routers. For larger networks, such as the one shown in Figure 12-8, HSRP typically is not used in the failover configuration.
To configure SNAT without HSRP, perform the following steps:
- Step 1. Configure stateful failover by defining the primary and backup routers.
- Step 2. Configure address translation.
SNAT Stateful Failover Configuration Without HSRP
In Step 1, you configure SNAT. You use these commands for the primary router:
Router(config)# ip nat stateful id router_ID_# Router(config-ipnat-snat)# primary local_IP_address_to_use Router(config-ipnat-snat-red)# peer backup_router's_IP_address Router(config-ipnat-snat-red)# mapping-id mapping_ID_#
The ip nat stateful id command assigns a unique router ID to this router. The primary command specifies that this is the primary router; you must specify an IP address on the router that it will use when building the TCP connection to the backup router. The peer command specifies the IP address to use to terminate the TCP connection on the backup router. The mapping-id command points to the dynamic translation entries that will be shared with the backup router.
You use these commands for the backup router:
Router(config)# ip nat stateful id router_ID_# Router(config-ipnat-snat)# backup local_IP_address_to_use Router(config-ipnat-snat-red)# peer primary_router's_IP_address Router(config-ipnat-snat-red)# mapping-id mapping_ID_#
This configuration is similar to the primary's configuration. Note that with the ip nat stateful id command, you must use a different ID number for the backup than the one assigned to the primary router. Next, the backup parameter defines this router as the backup, followed by the local address that this router will use to communicate with the primary router (this is the address listed in the primary's peer command). Following this is the peer statement, which specifies the address that the primary router is using (specified in the primary statement on the primary router). Finally, the mapping ID number configured here must match the one (or ones) configured on the primary router.
SNAT Address Translation Configuration Without HSRP
Next, you need to configure your address translation commands. The commands are the same as the ones used in the previous "HSRP with SNAT Address Translation Configuration" section, which discussed how to configure stateful failover with HSRP.
Stateful Failover Without HSRP Example
Now that you have a basic understanding of the commands used, take a look at an example to illustrate how to set up stateful address translation failover without using HSRP. This example uses the network shown previously in Figure 12-8. Example 12-10 shows the configuration for RouterA, which is the primary router.
Example 12-10. Using SNAT Without HSRP on the Primary Router
RouterA(config)# interface ethernet0 RouterA(config-if)# ip address 10.0.0.254 255.255.255.0 RouterA(config-if)# ip nat inside RouterA(config-if)# exit RouterA(config)# interface ethernet2 RouterA(config-if)# ip address 192.168.1.254 255.255.255.0 (1) RouterA(config-if)# exit RouterA(config)# interface ethernet1 RouterA(config-if)# ip nat outside RouterA(config-if)# exit RouterA(config)# ip nat stateful id 1 (2) RouterA(config-ipnat-snat)# primary 192.168.1.254 RouterA(config-ipnat-snat-red)# peer 192.168.1.253 RouterA(config-ipnat-snat-red)# mapping-id 100 RouterA(config-ipnat-snat-red)# exit RouterA(config)# ip nat pool SNAT-POOL 192.1.1.240 192.1.1.254 prefix-length 24 RouterA(config)# ip nat inside source route-map SNAT-MAP pool SNAT-POOL mapping-id 100 overload RouterA(config)# route-map SNAT-MAP permit 10 RouterA(config-route-map)# match ip address SNAT-ACL RouterA(config)# ip access-list extended SNAT-ACL RouterA(config-ext-nacl)# permit ip 10.0.0.0 0.255.255.255 any
This configuration is similar to the one that used HSRP. Notice that RouterA (see Statements 1 and 2 on the right side of Example 12-10) uses ethernet2 for the connection to RouterB. Also, in Statement 2, RouterA is configured as the primary.
Example 12-11 shows the configuration of RouterB, the backup router.
Example 12-11. Using SNAT Without HSRP on the Backup Router
RouterB(config)# interface ethernet0 RouterB(config-if)# ip address 10.0.0.252 255.255.255.0 RouterB(config-if)# exit RouterA(config)# interface ethernet2 RouterA(config-if)# ip address 192.168.1.253 255.255.255.0 RouterA(config-if)# exit RouterB(config)# interface ethernet1 RouterB(config-if)# ip nat outside RouterB(config-if)# exit RouterA(config)# ip nat stateful id 2 RouterA(config-ipnat-snat)# backup 192.168.1.253 RouterA(config-ipnat-snat-red)# peer 192.168.1.254 RouterA(config-ipnat-snat-red)# mapping-id 100 RouterA(config-ipnat-snat-red)# exit RouterB(config)# ip nat pool SNAT-POOL 192.1.1.240 192.1.1.254 prefix-length 24 RouterB(config)# ip nat inside source route-map SNAT-MAP pool SNAT-POOL mapping-id 100 overload RouterB(config)# route-map SNAT-MAP permit 10 RouterB(config-route-map)# match ip address SNAT-ACL RouterB(config)# ip access-list extended SNAT-ACL RouterB(config-ext-nacl)# permit ip 10.0.0.0 0.255.255.255 any
The only major difference between this configuration and the one used by the primary router is the stateful configuration with the backup and peer commands.
SNAT Verification
When you have finished configuring SNAT on your routers, you can use various commands, in addition to the troubleshooting address translation commands discussed in Chapter 11, to verify and troubleshoot the configuration of SNAT. You can use this basic show command to view SNAT information:
Router# show ip snat [distributed [verbose] | peer IP_address]
The distributed parameter enables you to see information about the distributed NAT information, as well as the status of the peer connection. With the verbose option, you can see detailed information about the stateful translations themselves (if they exist). If you use the peer parameter instead of the distributed parameter, you can see information about the TCP connection to the other stateful peer. Example 12-12 shows sample output from this command.
Example 12-12. Using the show ip nat Command
Router# show ip snat distributed verbose Stateful NAT Connected Peers SNAT: Mode IP-REDUNDANCY :: ACTIVE : State READY : Local Address 10.0.1.254 : Local NAT id 1 : Peer Address 10.0.1.253 : Peer NAT id 2 : Mapping List 100 : InMsgs 384, OutMsgs 385, tcb 0x82BF8BFC, listener 0x0
In this command, you can see that SNAT is configured with HSRP (IP-REDUNDANCY) and that this router is the active HSRP router. If this was failover without HSRP, you would see PRIMARY or BACKUP as the specified mode. At the bottom of the display, you can see the number of SNAT messages received and sent between the two routers.
If you want to clear the dynamic address translations used for stateful failover, use the following clear command:
Router# clear ip snat translation {distributed * | peer peer's_IP_address [refresh]}
You can clear all the SNAT dynamic translations with the distributed * parameter, or just the translations for a specific SNAT peer. With the peer parameter on the backup router, you can specify the optional refresh parameter, which causes the standby backup router to clear the dynamic SNAT translations in its local address translation table, as well as request a current table update from the active or primary router.
You can clear all the sessions to peer SNAT routers or just a specific session with this command:
Router# clear ip snat sessions [* | peer's_IP_address]
For detailed troubleshooting of SNAT, use the following command:
Router# debug ip snat [detailed]
This command enables you to see the actual messages shared between the active/primary and the standby/backup SNAT routers. Example 12-13 shows a sample of the use of this command.
Example 12-13. Using the debug ip snat Command
Router# debug ip snat detailed
2w3d:SNAT:Establish TCP peers for PRIMARY
2w3d:SNAT (Send):Enqueuing SYNC Message for Router-Id 1
2w3d:SNAT(write2net):192.168.1.254 <---> 192.168.1.253 send message
2w3d:SNAT(write2net):ver 2, id 100, opcode 1, len 68
2w3d:SNAT (Send):Enqueuing DUMP-REQUEST Message for Router-Id 1
In Example 12-13, stateful configuration was set up without HSRP. This router is the primary router. DUMP-REQUEST messages are requests for a dump (complete listing) of the primary's dynamic translation entries.
CAUTION
The debug ip snat command is very CPU intensive and should be used only when a small amount of traffic is being translated by the router; otherwise, it might overload the router and cause it to crash, in the worst-case scenario.








