Lock-and-Key Overview
As already discussed in Part III, "Nonstateful Filtering Technologies," you can use ACLs to protect your internal resources from external threats. However, in some situations you might need to allow specific users to other internal resources, but prevent the Internet from reaching these services. Unfortunately, normal ACLs, such as standard and extended ACLs, cannot provide this functionality?they filter only on Layers 3 and 4 and cannot authorize access on a per-user basis. This section details how lock-and-key access lists can help address these limitations.
Lock-and-Key and Normal ACLs
Lock-and-key was Cisco's first solution to the problem of authenticating users on unknown devices. Lock-and-key uses dynamic ACLs, somewhat similar to how Context-Based Access Control (CBAC) and reflexive ACLs work. However, whereas CBAC and reflexive ACLs add ACL entries based on inspected traffic, allowing the return of that traffic into the network, lock-and-key works differently. Lock-and-key requires a user first to authenticate to the router through Telnet or SSH. After being authenticated, specific dynamic ACL entries are activated on the ACL applied to the interface. These entries remain active for a specific period of time and then expire. This enables a user to authenticate and access resources that normally would be denied. Lock-and-key ACLs can be combined with other types of ACLs, such as extended ACLs.
The lock-and-key process is different from a normal extended ACL. With an extended ACL, all the statements are static. Therefore, if you want to allow specific users to access resources inside your network, you must set up a static ACL statement to grant this access; it remains active as long as the ACL is applied to the interface and the interface is up. Of course, if you do not know the IP addresses of these users, you must be fairly promiscuous in allowing a large range of addresses, which might be counter to your security policies. Lock-and-key is a more robust solution because static ACLs have the following characteristics:
They cannot authenticate individual users.
They are static and might require you to open a larger hole in your router to allow specific users into your network to access specific resources.
They are difficult to manage, especially when you must control specific users' access to resources, which also might cause the router to perform excessive processing of ACL statements.
When to Use Lock-and-Key
Lock-and-key, also referred to as dynamic ACL, was introduced to the Cisco IOS in version 11.1, so it has been around for quite a while. Originally, it was developed for dialup access and performed double authentication. With double authentication, the user was authenticated first through PPP's CHAP and then through lock-and-key. Sometimes the terms double authentication and lock-and-key are used interchangeably; however, lock-and-key is one specific authentication method used within double authentication. Lock-and-key is not restricted to just dialup access, though?it also can be used for LAN access. This chapter focuses on the latter approach.
Lock-and-key typically is used in one of two situations:
You want restricted access from your network based on a user's identity?with lock-and-key, the user is authenticated first and then granted access.
You want to control external access to internal resources based on a user's identity.
Lock-and-Key Benefits
Lock-and-key actually works hand in hand with extended ACLs, enhancing their functionality. Lock-and-key benefits include the following:
Authentication of the users can be centralized on an AAA server.
Users must provide a username and/or password to authenticate. After they are authenticated, a dynamic ACL entry is activated to allow or restrict additional access.
Management is simplified because ACL entries are created dynamically based on a user's authentication.
ACLs are smaller in size, and dynamic entries are added only when a user authenticates, placing a smaller burden of processing the ACL on the router.
Exposure to your internal resources is limited because dynamic entries are added only when a user authenticates.
Lock-and-Key Process
This section looks at the process that occurs when granting a user access to internal resources when the perimeter router is using lock-and-key. Figure 13-1 illustrates this example.
Figure 13-1. Lock-and-Key Process
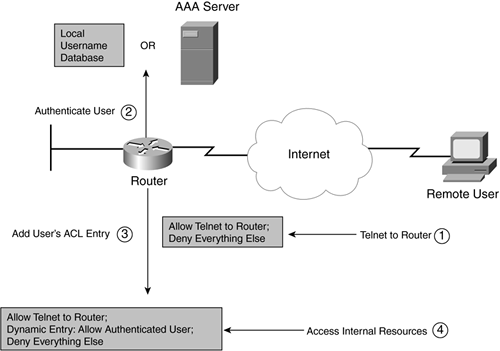
The following is an explanation of the numbered steps in Figure 13-1 that occur during the entire process:
A remote user first opens a Telnet or SSH connection to the router. The router's external ACL must permit this connection. The router prompts the user for a username and password, which the user enters.
Caution
Both Telnet and SSH are supported for the authentication. However, for public access to your router performing lock-and-key, I highly recommend that you use SSH instead of Telnet for the authentication connection. This is because SSH encrypts the session, including the password sent to the router. Remember that Telnet sends all traffic, including usernames and passwords, in clear text
The router authenticates the connection. Three choices can be used for authentication: the local username database defined with username commands, an AAA server using RADIUS or TACACS+, or the password command on the VTY lines. If the user fails the authentication, the user is reprompted for the authentication information. If the authentication is successful, the Telnet/SSH connection is terminated; the function of the Telnet/SSH connection is for authentication only. After the user has been authenticated, the Telnet/SSH connection no longer is needed, so the router terminates it.
After the user successfully authenticates, the Cisco IOS adds a dynamic ACL entry that grants the user access to the configured internal resources. As you will see later in the chapter, you cannot set up per-user access policies. Instead, you define one policy for all your lock-and-key users, and this single policy is applied to all the authenticated users.
At this point, the user can access the internal resources that would otherwise be denied (through the dynamic ACL entry).
If users do not authenticate first, they are allowed to access only resources specified in the static external ACL. To access other internal resources, the users first must authenticate through Telnet or SSH. Then the dynamic ACL entry added by the router allows them to access other internal resources.
CAUTION
Lock-and-key is susceptible to IP spoofing. After a user authenticates and opens a temporary hole in the firewall, the hacker can use this address to exploit a spoofing attack (typically, a DoS attack) if the hacker knows the user's source IP address. To prevent this kind of attack, you might want to consider encryption, such as a VPN. The temporary dynamic ACL entry also is not deleted automatically when the user terminates the session. Instead, it remains in the ACL until the dynamic entry timeout value is reached or until the administrator manually clears the entry (whichever happens first).







