Static and Black Hole Routing
This section covers the use of static routes to provide Layer 3 connectivity, as well as a solution called black hole routing, which is an alternative solution to ACLs when you want to drop unwanted traffic.
Static Routes
One of the safest routing solutions for your router is to use static routes to provide for Layer 3 connectivity. These are secure from route spoofing attacks because your router does not rely on routing information being sent and received from other routers: You configure all of the routing information locally on your perimeter router.
Static routes typically are used in these circumstances:
You have a small number of destinations to configure.
Only one or two paths exist to each destination.
With static routes, the following is true:
A default route is used on the perimeter router to reach external resources.
Specific internal routes are used to reach internal resources.
When using static routes, one of the two following commands is used:
Router(config)# ip route destination_network_# [subnet_mask] IP_address_of_next_hop_neighbor [administrative_distance] [permanent] Router(config)# ip route destination_network_# [subnet_mask] interface_to_exit [administrative_distance] [permanent]
You already should be familiar with these two Cisco router commands. If you want to set up a default route, specify 0.0.0.0 0.0.0.0 for the destination network number and the subnet mask.
Null Routes
Even though static routes are very secure, they present a scalability problem: The more networks that you have, and the more redundant paths that you have to these networks, the more difficult it becomes to manage routing on your router. In this situation, you might have to run a dynamic routing protocol, such as OSPF. However, you can complement a dynamic routing protocol with static routes to provide optimal protection.
One of the concepts that you should be familiar with by now is traffic filtering with ACLs. ACLs enable you to filter packets based on the information contained in their headers. One problem of packet filtering is performance because the router must examine packet headers to make a filtering decision, thus adding some overhead to the processing of the packets.
A complementary solution to both routing and filtering is to use black hole routes. A black hole route is used to forward unwanted or undesirable traffic into a black hole. In Cisco terminology, a special logical interface, called a null interface, is used to create the black hole. Static routes are created for destinations that are not desirable, and the static route configuration points to the null interface. Any traffic that has a destination address that has a best match of the black hole static route automatically is dropped. Unlike with ACLs, all switching processes of the Cisco IOS, including CEF, can handle black hole routes without any performance degradation.
Setting up a black hole route is easy because it uses the static route configuration:
Router(config)# ip route destination_network_# [subnet_mask] null0
Notice that the only unique thing about this command is that the destination interface is null0, the black hole. Any traffic destined to the destination network in the static route command is routed to null0 (that is, it is dropped).
As I mentioned in Chapter 6, "Access List Introduction," and Chapter 7, "Basic Access Lists," you should make your ACLs as short and simple as possible. However, when I discussed how to filter bogon routes in Chapter 7, these ACL commands added quite a bit of length to the ACL. My personal preference is to not use ACLs to filter destination bogon addresses, but instead to use black hole routes.
NOTE
When using the null0 interface for black hole routing, you will want to prevent your router from sending ICMP unreachable messages to the sender of the packet, like this:
Router(config)# interface null0 Router(config-if)# no ip unreachables
If you do not do this, a hacker can take advantage of this loophole in your configuration to create a DoS attack by flooding your router with black-holed addresses, causing your router to generate an ICMP unreachable message for each packet that the router drops. Hackers like to use this type of DoS attack because many administrators forget to disable ICMP unreachables and inadvertently generate just as much traffic back to the source (which is typically a spoofed address), creating a second DoS attack. By preventing the generation of ICMP unreachable messages, your router silently drops the packets.
CAUTION
Black hole routes drop all traffic sent to the specified destination; there is no granularity of looking at other information to drop traffic. Therefore, this security solution should be used only for known destination addresses that you never want your router to forward traffic to. Based on this information, black hole routing ideally is suited for destination bogon addresses.
Examine the network shown in Figure 15-1. I set up the perimeter router to perform bogon filtering with black hole routers, to give you a better understanding of the configuration.
Figure 15-1. Black Hole Routing Example
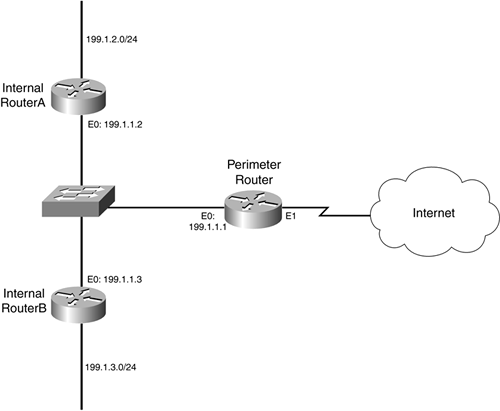
Example 15-1 shows the configuration for the perimeter router in Figure 15-1, focusing on only the black hole routing component.
Example 15-1. Using Black Hole Routing for Destination Bogon Addresses
Router(config)# interface null0 (1) Router(config-if)# no ip unreachables Router(config-if)# exit Router(config)# Router(config)# ip route 199.1.2.0 255.255.255.0 199.1.1.2 (2) Router(config)# ip route 199.1.3.0 255.255.255.0 199.1.1.3 Router(config)# ip route 0.0.0.0 0.0.0.0.0 ethernet1 Router(config)# Router(config)# ip route 1.0.0.0 255.0.0.0 null0 (3) Router(config)# ip route 2.0.0.0 255.0.0.0 null0 Router(config)# ip route 5.0.0.0 255.0.0.0 null0 Router(config)# ip route 7.0.0.0 255.0.0.0 null0 Router(config)# ip route 23.0.0.0 255.0.0.0 null0 Router(config)# ip route 27.0.0.0 255.0.0.0 null0 Router(config)# ip route 31.0.0.0 255.0.0.0 null0 Router(config)# ! <--omitted bogon routes--> Router(config)# ip route 197.0.0.0 255.0.0.0 null0 Router(config)# ip route 201.0.0.0 255.0.0.0 null0 Router(config)# ip route 10.0.0.0 255.0.0.0 null0 Router(config)# ip route 172.16.0.0 255.240.0.0 null0 Router(config)# ip route 192.168.0.0 255.255.0.0 null0 Router(config)# ip route 0.0.0.0 255.0.0.0 null0 Router(config)# ip route 224.0.0.0 240.0.0.0 null0 Router(config)# ip route 240.0.0.0 240.0.0.0 null0 Router(config)# ip route 169.254.0.0 255.255.0.0 null0 Router(config)# ip route 192.0.2.0 255.255.255.0 null0 Router(config)# ip route 127.0.0.0 255.0.0.0 null0
In Example 15-1, Statement 1 (referring to the numbers on the right side of Example 15-1) disables ICMP unreachable messages for the black hole routes. The first two statements in Statement 2 set up static routes for the two internal networks, and the third statement is a default route to reach the Internet. All of the statements following Statement 3 are black hole routes.
Policy-Based Routing
Policy-based routing (PBR) is a more flexible alternative to implementing black hole routing than using static routes. I briefly discussed the use of PBR in Chapter 10, "Filtering Web and Application Traffic." In this chapter, I discussed how you can use PBR to mark traffic and then have an ACL drop the traffic. However, there is an alternative solution to dropping the traffic instead of using an ACL: a black hole route.
I do not spend much time discussing the policy commands because many of them were discussed in Chapter 10. To set up PBR for black hole routing, follow these steps:
- Step 1. Create an ACL that will match on the packets you have marked (either the DSCP or Type of Service [ToS] field in the IP header).
- Step 2. Create a route map that will route the traffic matching the ACL to the null0 interface. Use these commands:
Router(config)# route-map route_map_name sequence_# Router(config-route-map)# match ip address extended_ACL_#_or_name Router(config-route-map)# set interface null0
The route-map command creates the route map; give it a descriptive name and a sequence number. The sequence number is used to insert a route map statement into an existing route map. Use the match ip address command that points to the ACL in Step 3. The set interface null0 command specifies where to route the matching packets. - Step 3. Activate the route map on the external interface (if filtering external-to-internal traffic):
Router(config)# interface type [slot_#/]port_# Router(config-if)# ip policy route-map route_map_name
It is important to point out here that this is different from what was described in Chapter 10. In Chapter 10, the packets were marked on the ingress interface and were filtered by an ACL on the egress interface: This was necessary because packets cannot be processed twice by an ACL on the same interface. However PBR is a routing function, which occurs after the ACL filtering, so activating your service policies and route map policies on the same interface is correct. Also, PBR supports CEF switching; you do not need to do anything to enable this feature except to configure CEF itself.
Refer back to Figure 15-1 for a couple of examples of using PBR for black hole routing. This first example looks at filtering bogon networks. Example 15-2 shows the configuration.
Example 15-2. Using PBR for Black Hole Routing
Router(config)# interface null0 (1) Router(config-if)# no ip unreachables Router(config-if)# exit Router(config)# ip route 199.1.2.0 255.255.255.0 199.1.1.2 Router(config)# ip route 199.1.3.0 255.255.255.0 199.1.1.3 Router(config)# ip route 0.0.0.0 0.0.0.0.0 ethernet1 Router(config)# Router(config)# ip access-list extended bogon-ACL (2) Router(config-ext-nacl)# permit ip 1.0.0.0 0.255.255.255 any Router(config-ext-nacl)# permit ip 2.0.0.0 0.255.255.255 any Router(config-ext-nacl)# permit ip 5.0.0.0 0.255.255.255 any Router(config-ext-nacl)# ! <--output omitted (you need to add the rest of the bogons here--> Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# route-map black-hole 10 (3) Router(config-route-map)# match ip address bogon-ACL Router(config-route-map)# set interface null0 Router(config-route-map)# exit Router(config)# interface ethernet0 Router(config-if)# ip policy route-map black-hole (4)
The following is an explanation of Example 15-2, with reference to the numbering on the right side of the configuration:
This set of code has the router not generate ICMP unreachable messages and defines the static routes for connectivity.
This is a partial ACL that matches on all bogon addresses (I have omitted the complete list, but you can look at the previous example for all of these networks).
The route map references the ACL in Step 2 and routes these packets to the null0 interface.
The route map is activated on the external interface (with PBR, the matching and dropping are done on the same interface).
In this next example of using PBR, I change the example used in Chapter 10, where NBAR was used to drop Code Red packets by using a filter. In this example, I change the configuration so that, instead of the ACL dropping the packets, PBR is used. Example 15-3 uses the network in Figure 15-1. I focus only on the policy commands for this configuration.
Example 15-3. Using PBR to Drop Code Red Packets
Router(config)# class-map match-any code-red-attacks (1) Router(config-cmap)# match protocol http url "*.ida*" Router(config-cmap)# match protocol http url "*cmd.exe*" Router(config-cmap)# match protocol http url "*root.exe*" Router(config-cmap)# exit Router(config)# policy-map mark-code-red (2) Router(config-pmap)# class code-red-attacks Router(config-pmap-c)# set ip dscp 1 Router(config-pmac-c)# exit Router(config)# interface ethernet1 Router(config-if)# service-policy input mark-code-red (3) Router(config-if)# exit Router(config)# ip access-list extended match-dscp-ACL (4) Router(config-ext-nacl)# permit ip any any dscp 1 Router(config-ext-nacl)# exit Router(config)# route-map black-hole 10 (5) Router(config-route-map)# match ip address match-dscp-ACL Router(config-route-map)# set interface null0 Router(config-route-map)# exit Router(config)# interface ethernet1 Router(config-if)# ip policy route-map black-hole (6)
Statements 1, 2, and 3 include the same commands discussed in Chapter 10. Statements 4, 5, and 6 are specifically for PBR. The following is an explanation of Example 15-3 with reference to the numbering on the right side of the configuration:
This class map uses NBAR to match on URL contents.
The policy map marks the DSCP field in the IP header for Code Red packets.
The policy map is activated on the external interface as traffic enters the perimeter router from the Internet.
The ACL matches on all packets that have the DSCP field set to 1.
The route map routes all DSCP = 1 packets to the null0 interface.
The route map is activated on the ingress interface (with route maps, you can match and filter on the same interface).
TIP
If you have a choice between using ACLs to filter traffic and using black hole routing, I definitely recommend the latter, especially if you are using static routes. However, I recommend that you use PBR only in situations in which you already are using it because it does affect the processing cycles of the router. For example, if you already are using it to detect and block Code Red, you might want to use it for other filtering policies as well.








