Security Threats
As show in Figure 8-1, there are several forms of security threats to wireless networks. For example, hackers can steal information from a company, obtain unauthorized access to applications, and even disrupt operation of the network.
Figure 8-1. Threats to Wireless Network Security Include Passive Monitoring, Unauthorized Access, and Denial of Service (DoS)
Traffic Monitoring
An experienced hacker, or even casual snooper, can easily monitor unprotected wireless data packets using tools such as AirMagnet and AiroPeek, which fully disclose the contents of wireless data packets. For example, snoopers can monitor all transactions occurring over the wireless portion of the network several hundred feet away from the building that has the wireless LAN. Of course, the issue is that anyone can identify usernames, passwords, credit card numbers, and so on. In fact, war drivers even post their finds on web sites, just for fun.
The solution to this problem is to, at a minimum, employ encryption between the wireless client device and the base station. Encryption alters data bits using a secret key. Because the key is secret, a hacker is not able to decipher the data. As a result, the use of effective encryption mechanisms upholds the privacy of data.
Unauthorized Access
Similar to monitoring a wireless application, someone can effortlessly access a corporate wireless network from outside the facility if the proper precautions are not taken. Someone can, for example, sit in a parked car and associate with one of the wireless base stations located inside a building. Without proper security, this person can access servers and applications residing on the corporate network. This is similar to letting a stranger inside your home or office.
Unfortunately, many companies deploy their wireless networks using the default, unsecured base station configurations, making it possible for anyone to interface with their application servers. In fact, you can go war driving and discover that 30 percent of the wireless LAN access points in an average city do not deploy any form of security. This allows anyone to access hard drives and use resources such as Internet connections.
The Windows XP operating system makes it easy to interface with wireless networks, especially on public wireless LANs. When a laptop associates with the wireless LAN, the user can navigate to any other laptop associated with the same wireless LAN. Without personal firewall protection, someone can browse through your hard drive. This is a tremendous security risk.
Even if you implement all security controls on access points, the possible connection of a rogue access point is a significant threat. (See Figure 8-2.) A rogue access point is an unauthorized access point on the network. An employee might purchase an access point and install it within his office without knowing the security implications. A hacker could also plant a rogue access point within a facility by purposely connecting an unprotected access point to the corporate network.
Figure 8-2. Rogue Access Points Offer an Open Port for Hackers to Exploit
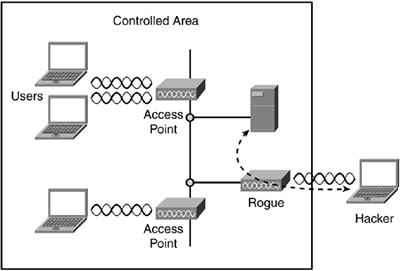
A rogue access point can be exploited because it probably won't have any encryption activated, which provides an open door for someone to easily access the corporate network from outside the facility. For that reason, a company should continually monitor for the presence of rogue access points. Keep in mind that this is a problem whether a wireless network is in place or not. Someone could connect a rogue access point to a completely wired Ethernet network.
To counter unauthorized access, the wireless network should deploy mutual authentication between client devices and the access points. Authentication is the action of proving the identity of a person or device. The wireless network should implement methods for client devices to prove identity to base stations and vice versa. This ensures the validity of the user and proves that the user is connecting to a legitimate access point. In addition, access points should authenticate with the switches to disallow the successful connection of a rogue access point.
Man-in-the-Middle Attacks
The use of encryption and authentication techniques improves the security of a wireless network; however, smart hackers can still find vulnerabilities because of the way that networking protocols operate. A definite weakness is a man-in-the-middle attack, which is when a hacker places a fictitious device between the users and the wireless network. (See Figure 8-3.) For example, a common man-in-the-middle attack exploits the common address resolution protocol (ARP) that all TCP/IP networks utilize. A hacker with the right tools can exploit ARP and take control of the wireless network.
Figure 8-3. Intermediate Devices Enable Man-in-the-Middle Attacks
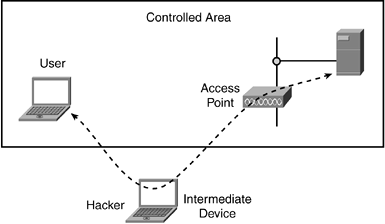
ARP is a crucial function used by sending a wireless or wired NIC to discover the physical address of a destination NIC. The physical address of a card is the same as the medium-access control (MAC) address, which is embedded in the card by the manufacturer and unique from any other NIC or network component. The MAC address is analogous to the street address of your home. Just as someone must know this address to send you a letter, a sending NIC must know the MAC address of the destination. The NIC only understands and responds to the physical MAC address.
The application software that needs to send the data will have the destination IP address, but the sending NIC must use ARP to discover the corresponding physical address. It gets the address by broadcasting an ARP request packet that announces the destination NIC's IP address. All stations will hear this request, and the station with the corresponding IP address will return an ARP response packet containing its MAC address and IP address.
The sending station will then include this MAC address as the destination address in the frame being sent. The sending station also stores the corresponding IP address and MAC address mapping in a table for a specified period of time (or until the station receives another ARP response from the station having that IP address).
A problem with ARP is that it introduces a security risk resulting from ARP spoofing. For example, a hacker can fool a station by sending, from a rogue network device, a fictitious ARP response that includes the IP address of a legitimate network device and the MAC address of the rogue device. This causes all legitimate stations on the network to automatically update their ARP tables with the false mapping.
Of course, these stations will then send future packets to the rogue device rather than to the legitimate access point or router. This is a classic man-in-the-middle attack, which enables a hacker to manipulate user sessions. As a result, the hacker can obtain passwords, capture sensitive data, and even interface with corporate servers as if they were the legitimate user.
In order to circumvent man-in-the-middle attacks using ARP spoofing, vendors such as OptimumPath implement secure ARP (SARP). This enhancement to ARP provides a special secure tunnel between each client and the wireless access point or router, which ignores any ARP responses not associated with the clients on the other end of the tunnel. Therefore, only legitimate ARP responses provide the basis for updating ARP tables. The stations implementing SARP are free from spoofing.
The use of SARP, however, requires the installation of special software on each client. Consequently, SARP is not practical for public hotspots. Enterprises, though, can install SARP on clients and be much freer from man-in-the-middle attacks.
Denial of Service
A Denial of Service (DoS) attack is an assault that can cripple or disable a wireless network. The possibility of such an attack is something that anyone deploying wireless networks should consider. Be sure to think about what could happen if the wireless network becomes unavailable for an indefinite period of time.
The severity of the DoS attack depends on the impact of the wireless network becoming inoperative. For example, a hacker could disable someone's home wireless LAN, but the result will probably just inconvenience the homeowner. A DoS attack that shuts down a wireless inventory system, however, could cause major financial loss.
One form of DoS attack is the brute-force method. For example, a huge flood of packets that uses all of the network's resources and forces the network to shut down is a DoS brute-force attack. There are tools on the Internet that enable hackers to cause excessive flooding on wireless networks. A hacker can perform a packet-based brute-force DoS attack by sending useless packets to the server from other computers on the network. This adds significant overhead on the network and takes away usable bandwidth from legitimate users.
Another way of stopping most wireless networks, especially those that use carrier sense access, is using a strong radio signal to dominate the airwaves and render access points and radio cards useless. Protocols such as 802.11 are very polite and let the DoS attack signal have access to the medium for as long as it wants.
The use of strong radio signals to disrupt the network is a rather risky attack for a hacker to attempt, however. Because a powerful transmitter at a close range must execute this type of attack, the owners of the wireless network can find the hacker through the use of homing tools available in network analyzers. Once the jamming source is found, authorities can stop it and possibly apprehend the culprits.
Sometimes a DoS occurrence on a wireless network is unintentional. For example, 802.11b operates in a crowded radio spectrum. Other devices such as cordless phones, microwaves, and Bluetooth can cause a significant reduction in 802.11b performance. The interference can keep a wireless network from operating.
In addition, some security mechanisms are prime targets for DoS attacks. Wi-Fi Protected Access (WPA), for example, is vulnerable to a type of DoS attack. WPA uses mathematical algorithms to authenticate users to the network. If a user is trying to get in and sends two packets of unauthorized data within one second, WPA will assume it is under attack and shut down.
The only completely effective way to counter DoS attacks is to isolate your computer in a room with heavy security and unplug it from all networks, including the Internet. This means not using a wireless network, of course. The U.S. government uses this method to protect their most sensitive data, but this solution is not practical for any enterprise or home application, where there are benefits for deploying wireless networks.
The most fundamental defense against DoS is developing and maintaining strong security practices. Actions such as implementing and updating firewalls, maintaining updated virus protection, installing up-to-date security patches, ensuring strong passwords, and turning off network devices when they are not needed should be routine practices for all companies and homeowners.
You can protect a wireless LAN against DoS attacks by making the building as resistant as possible to radio signals coming in. Here are some steps to help reduce radio signal leakage:
If interior walls use metal studs, make sure they are grounded.
Install thermally insulated copper or metallic film-based windows.
Use metallic window tint instead of blinds or curtains.
Use metallic-based paint on the interior or exterior walls.
Run tests to determine how far the signal actually leaks outside of the building. Adjust transmitter power accordingly until the leakage is eliminated or reduced to the point that it would be easy to locate a hacker.
Aim directive access point antennas toward the inside of the building.
Because there's no way of completely countering all types of DoS attacks, consider a plan B if a DoS attack will cause significant damage. For example, have a process for switching to batch processing or paper-based methods if the application is subjected to a severe DoS attack. You certainly don't want potential weaknesses in the wireless network to bring down your company!






