Small and Medium Businesses and SOHO WLAN Deployments
This section covers examples from small, medium, and SOHO (small office, home office) deployments. In small office and SOHO scenarios, WLAN is considered the primary network connectivity and is preferred to wired Ethernet connectivity. This is primarily due to the desire to minimize overall network deployment costs (that is, eliminate wiring costs). In the medium office scenario, WLAN could be deployed either for primary network connectivity or as an overlay deployment (mainly providing coverage for meeting rooms).
Medium Enterprise WLAN Deployment Scenario Example
In this example, WLAN was deployed as the primary network connectivity for an office of approximately 1000 employees. All users were at a single physical location.
The customer deployment criteria and deployment environment are as follows:
Strong user authentication and strong encryption exist.
Support single sign-on integrates WLAN authentication with Windows logon.
Users are standardized on Windows XP platform and CCX-enabled laptops.
Cisco Secure ACS and Microsoft AD infrastructure are deployed.
Given the preceding deployment requirements and deployment environment, the customer implemented PEAP/MS-CHAPv2 with WPA as the WLAN security policy. Windows XP supplicant was configured to enable PEAP/MS-CHAPv2 authentication using the user's Windows logon credentials to facilitate single sign-on. An X.509v3 compliant server certificate was self-issued using Cisco Secure ACS 3.3 and above. The self-issued server certificate was used for PEAP authentication. The ACS server was configured to authenticate PEAP users via Microsoft AD server.
RF monitoring functionality, including rogue AP detection, was enabled using Cisco SWAN solution. This required WLSE 2.5 or above, AP IOS release 12.2(13)JA or above, and CCXv2 or above for WLAN clients.
Small Office WLAN Deployment Example
In this example, WLAN connectivity was enabled as the primary network connectivity for approximately 100 users at a single location. The customer did not have the IT budget to deploy RADIUS infrastructure for WLAN user authentication. Also, the customer had not deployed Microsoft AD infrastructure. However, the customer did standardize on the Cisco WLAN infrastructure and clients for WLAN deployment. Figure 13-10 illustrates this deployment topology.
Figure 13-10. Small Office WLAN Deployment Example
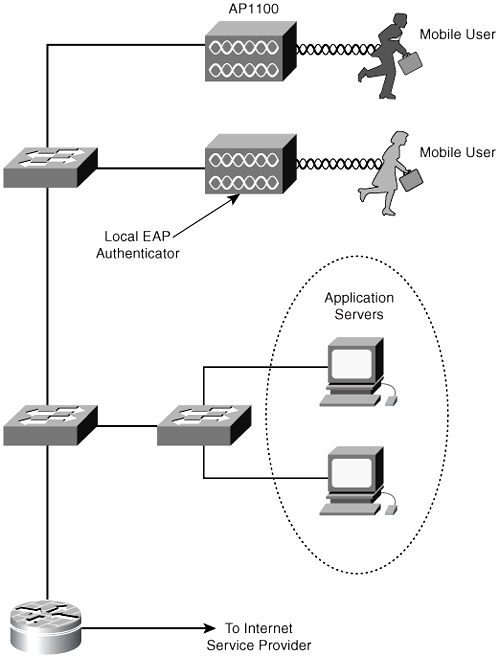
LEAP with WPA was selected as the security model, where the local RADIUS server on the IOS-enabled APs (12.2[11] JA1 release or above) facilitated LEAP authentication. The IT administrator used a strong password policy to generate 15-character passwords with a combination of alphanumeric and nonalphanumeric characters. The LEAP authentication credential was securely stored on each laptop.
SOHO WLAN Deployment Scenario Example
This example provided a secure WLAN deployment at home to enable remote connectivity for a full-time telecommuter. In this example, WPA-PSK mode was used between the WLAN client and the AP to secure the link layer. However, the client was required to launch and terminate the IPSec VPN tunnel with corporate HQ to enable access to corporate applications. A long passphrase (greater than 20 characters) created using a combination of alphanumeric and nonalphanumeric was used as the WPA-PSK passphrase (to minimize risk due to offline dictionary attacks). Figure 13-11 illustrates this deployment topology.







