Hack 70 PPTP Tunneling
![]()
![]()
Set up quick and easy VPN access using the Point-to-Point Tunneling Protocol.
The Point-to-Point Tunneling Protocol (PPTP) is basically a means to set up PPP tunnels [Hack #81] automatically without needing to manually start a PPP daemon on the remote machine. The main benefit of using PPTP is that both Windows and Mac OS X natively support the creation of VPN connections, and both provide easy-to-use GUIs for setting up the connections on the client side. Thus, you can provide a VPN solution without much effort on your users' part.
To set up the server end, you can use PoPToP (http://www.poptop.org), an open source PPTP server. You can get a very simple PPTP VPN going with minimal effort?just download the source distribution and unpack it, then go into the directory it created.
After you've done that, you can run this command to compile it:
$ ./configure && make
Then become root and run this command to install PoPToP:
# make install
The PPTP daemon that this installs is called pptpd. Now you'll need to create a configuration file for pptpd (i.e., /etc/pptpd.conf) and a pppd options file to use with it.
Here's a suitable /etc/pptpd.conf to start out with:
option /etc/ppp/options.pptpd localip 10.0.0.1 remoteip 10.0.0.2-100
This defines the IP address of the local end of the PPTP connection as 10.0.0.1 and creates a pool of addresses to be dynamically allocated to clients (i.e., 10.0.0.2-100). When you create your pptpd.conf file, you should use addresses from the range used by your internal network. In addition, this configuration file tells pptpd to set up the PPP interface using /etc/ppp/options.pptpd when it starts pppd. Otherwise it would use the default of /etc/ppp/options, which probably isn't what you want.
Now you'll need to create the aforementioned /etc/ppp/options.pptpd:
lock name pptpd auth
These options basically tell pppd to use authentication (auth), and indicate what entries in the /etc/ppp/chap-secrets file correspond to this instance of pppd (name pptpd). So, to finish configuring authentication for pptpd, you'll need to create an entry for each client in the /etc/ppp/chap-secrets file.
Here's a simple entry that allows someone with the username of andrew to connect with the password mypassword from any remote IP address:
# Secrets for authentication using CHAP # client server secret IP addresses andrew pptpd mypassword *
The pptpd in the server field should be replaced with whatever you used in the name directive in your /etc/ppp/options.pptpd file (if you didn't use pptpd). You can of course limit the client to specific IP addresses by listing them.
Now that you have a basic setup for PoPToP , you can try it out by connecting to it with a Windows machine. Go to your Network Connections folder and click "Create a new connection" (this is for Windows XP; for Windows 2000, look for "Make New Connection"). After you click this, a wizard dialog should appear that looks similar to Figure 6-1.
Figure 6-1. Windows XP's New Connection Wizard
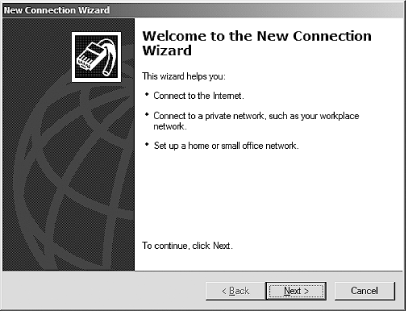
Click Next and then select the "Connect to the network at my workplace" radio button, as shown in Figure 6-2.
Figure 6-2. Choosing the connection type
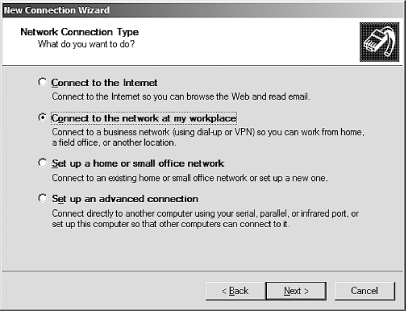
After you've done that, click Next again and then click the "Virtual Private Network connection" radio button. You should now see something similar to Figure 6-3.
Figure 6-3. Selecting a VPN connection
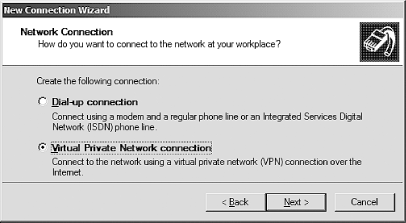
Click Next and fill in a name for the newly created connection (e.g., PoPToP Test). After you've done that, click Next once again and then enter the external IP address of the server running pptpd. Now click Next and then Finish. You'll then be presented with a login dialog similar to the one shown in Figure 6-4.
Figure 6-4. The connection login dialog
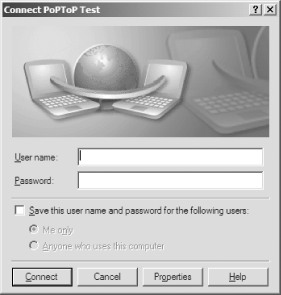
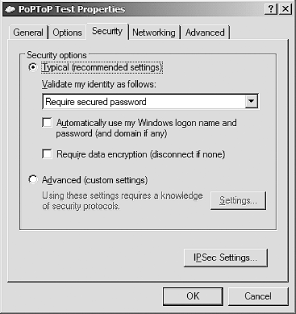
Before entering the username and password that you specified in the /etc/ppp/chap-secrets file, you'll need to click Properties and locate the Security tab. After you've done that, locate the "Require data encryption" checkbox and uncheck it. You should now see something similar to Figure 6-5.
Figure 6-5. Changing the security properties
Now click OK, enter your login information, and then click Connect. In a few seconds you should be connected to the PPTP server and will be allocated an IP address from the pool that you specified. You should now test the connection by pinging the remote end of the tunnel. With the PPTP connection active, all traffic leaving the client side will be encrypted and sent to the PoPToP server. From there, traffic will make its way to its ultimate destination.






