B.1 Structural Modeling
The next few sections present solutions for Part II.
B.1.1 Chapter 3
The figure shows a Report class.
The class has the following attributes:
NextID, which is private, holds an integer value, is initialized to 1, and is shared by all the objects of the class.
ID, which is private, holds an integer value, is not initialized to any value, and is specific to each object of the class.
Name, which is private, holds a string value, is initialized to an empty string, and is specific to each object of the class.
CreationDate, which is private, holds a string value, is initialized to an empty string, and is specific to each object of the class.
SectionName, which is private, holds one or more ordered string values that are initialized to an empty string, and is specific to each object of the class.
ProjectName, which is private, holds one or more unordered string values that are initialized to an empty string, and is specific to each object of the class.
OwnerName, which is private, holds a string value, is not initialized to any value, and is specific to each object of the class.
The class has the following operations:
create, which is public, receives no parameters, returns a value of type Report, and applies to the class rather than a specific object of the class.
create, which is public, receives one parameter, returns a value of type Report, and applies to the class rather than a specific object of the class. The operation receives a parameter named theOwnerName, which is input and may not be modified by the operation, holds a string value, and is initialized to the string "Unknown Owner".
destroy, which is public, receives no parameters, returns nothing, and applies to objects of the class.
getID, which is public, receives no parameters, returns an integer value, and applies to objects of the class.
setName, which is public, receives one parameter, returns nothing, and applies to objects of the class. The operation receives a parameter named theName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
getName, which is public, receives no parameters, returns a string value, and applies to objects of the class.
getCreationDate, which is public, receives no parameters, returns a string value, and applies to objects of the class.
setSectionName, which is public, receives two parameters, returns nothing, and applies to objects of the class. The first parameter that the operation receives is named theSectionName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value. The second parameter that the operation receives is named theSectionOrder, which is input and may not be modified by the operation, holds an integer value, and is initialized to the value 1.
getSectionName, which is public, receives one parameter, returns a string value, and applies to objects of the class. The operation receives a parameter named theSectionOrder, which is input and may not be modified by the operation, holds an integer value, and is initialized to the value 1.
addProjectName, which is public, receives one parameter, returns nothing, and applies to objects of the class. The operation receives a parameter named theProjectName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
removeProjectName, which is public, receives one parameter, returns nothing, and applies to objects of the class. The operation receives a parameter named theProjectName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
setOwnerName, which is protected, receives one parameter, returns nothing, and applies to objects of the class. The operation receives a parameter named theOwnerName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
getOwnerName, which is protected, receives no parameters, returns a string value, and applies to objects of the class.
doesReportHaveProjectName, which is public, receives one parameter, returns a Boolean value, and applies to objects of the class. The operation receives a parameter named theProjectName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
setNameAndOwner, which is public, receives two parameters, returns nothing, and applies to objects of the class. The first parameter that the operation receives is named theName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value. The second parameter that the operation receives is named theOwnerName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value. An operation named getNameAndOwner, which is public, receives two parameters, returns nothing, and applies to objects of the class. The first parameter that the operation receives is named theName, which is output and may be modified by the operation, holds a string value, and is not initialized to any value. The second parameter that the operation receives is named theOwnerName, which is output and may be modified by the operation, holds a string value, and is not initialized to any value.
refreshNameAndOwner, which is public, receives two parameters, returns nothing, and applies to objects of the class. The first parameter that the operation receives is named theName, which is input and may be modified by the operation, holds a string value, and is not initialized to any value. The second parameter that the operation receives is named theOwnerName, which is input and may be modified by the operation, holds a string value, and is not initialized to any value.
The figure shows a Report object named ProjectAndTeamStatus, described in the following:
The object's ID attribute has the integer value of 1.
The object's Name attribute has the string value of "Project Report".
The object's CreationDate attribute has the string value of "January 2002".
The object's SectionName attribute has the ordered string values of "Project Information", "Status Information", and "Team Information".
The object's ProjectName attribute has the unordered string values of "Eagle", "Falcon", and "Hawk".
The object's OwnerName attribute has the string value "Nora".
The following describes the figure: workers and skills are related, projects and activities are related, and activities and skills are related.
Figure B-1 shows the figure.
Figure B-1. Class diagram (question 3 part a)
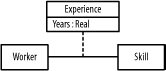
Figure B-2 shows the figure.
Figure B-2. Class diagram (question 3 part b)
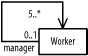
Figure B-3 shows the figure.
Figure B-3. Class diagram (question 3 part c)
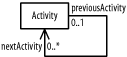
Figure B-4 shows the figure.
Figure B-4. Class diagram (question 3 part d)
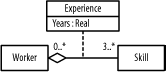
Figure B-5 shows the figure.
Figure B-5. Class diagram (question 3 part e)
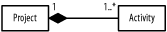
Figure B-6 shows the figure.
Figure B-6. Class diagram (question 3 part f)

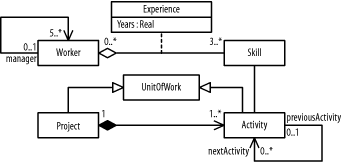
Figure B-7 shows the resulting diagram, which includes all the steps in this question.
Figure B-7. Class diagram (question 3)
The following describes the figure: a plan relates workers and activities on a project.
Figure B-8 shows the figure.
Figure B-8. Class diagram (question 4 part a)
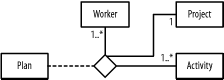
Figure B-9 shows the figure.
Figure B-9. Class diagram (question 4 part b)
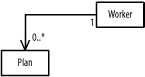
Figure B-10 shows the figure.
Figure B-10. Class diagram (question 4 part c)

Figure B-11 shows the figure.
Figure B-11. Class diagram (question 4 part d)
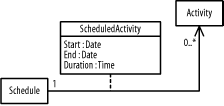
Figure B-12 shows the figure.
Figure B-12. Class diagram (question 4 part e)
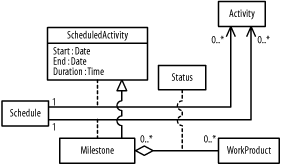
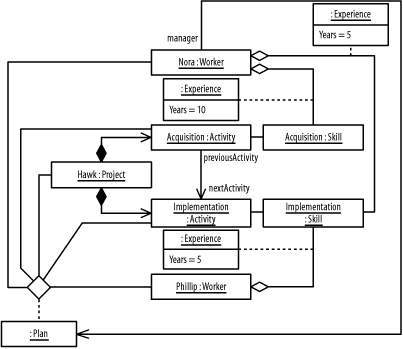
Figure B-13 shows the resulting diagram, which includes all the steps in this question.
Figure B-13. Class diagram (question 4)
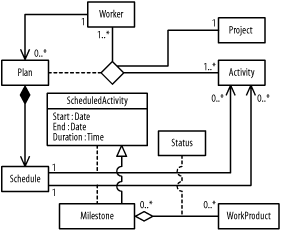
The following figures result:
Figure B-14 results from the description.
Figure B-14. Nora, Andy, Jonathan, and their skills (question 5 part a)
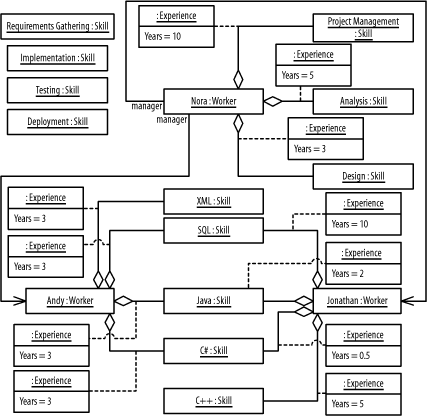
Figure B-15 results from the description.
Figure B-15. The Eagle project (question 5 part b)
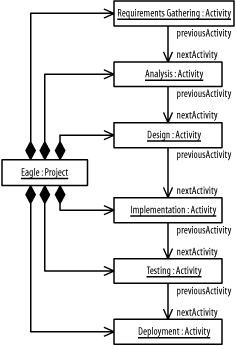
Figure B-16 results from the description.
Figure B-16. The Hawk project (question 5 part c)
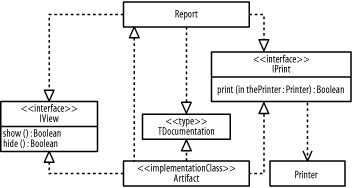
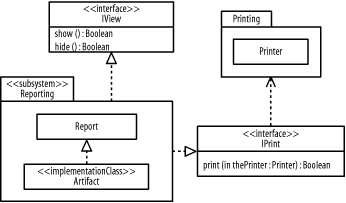
The following describes the figure:
There is one type, named TDocumentation.
There are two interfaces, named IView and IPrint. The IView interface has two operations, named show and hide, which receive no parameters and return a Boolean value. The IPrint interface has one operation, named print, which receives one parameter and returns a Boolean value. The print operation receives a parameter, named thePrinter, which is input and may not be modified by the operation, holds a value of type Printer, and is not initialized to any value.
There is one implementation class, named Artifact.
There are two undifferentiated classes, named Report and Printer.
Figure B-17 shows the resulting diagram, which includes all the steps in this question.
Figure B-17. Class diagram (question 6)
The figure shows a security subsystem, named Security, which has the following specification elements:
An operation, named start, which receives no parameters and returns a Boolean value.
An operation, named stop, which receives no parameters and returns a Boolean value.
A Login use case that is realized by the SecurityManager class.
An IUserManagement interface.
An ISecureResourceManagement interface.
An ISecurity interface that specifies an operation, named validateUserNameAndPassword, which receives two parameters and returns a Boolean value. The first parameter is named theUserName, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value. The second parameter is named thePassword, which is input and may not be modified by the operation, holds a string value, and is not initialized to any value.
The subsystem has the following realization elements:
A SecurityManager class that offers the start and stop operations.
The SecurityManager class also realizes the Login use case.
Figure B-18 shows the resulting diagram.
Figure B-18. Reporting subsystem (question 8)
B.1.2 Chapter 4
The following describes the figure:
The project management system interacts with human resources, printers, project web servers, and backup systems. Human resources include project managers, resource managers, and system administrators.
A human resource may log in and out of the system.
A project manager may manage projects, including maintaining projects, activities, and tasks.
A project manager may publish project status by either generating a report involving a printer or generating a web site involving a project web server.
A system administrator may administer the system, including starting up or shutting down the system. Before starting up the system, the system administrator may restore data; after shutting down the system, the system administrator may backup data. Likewise, the system administrator may initiate the process or the system may initiate an interaction with the system administrator informing the actor of the system's status.
A resource manager may manage resources.
When a project manager manages projects, a system administrator administers the system, or a resource manger manages resources, their activities are logged.
The following updates are made to the diagram:
Figure B-19 shows the figure.
Figure B-19. Use-case diagram (question 2 part a)
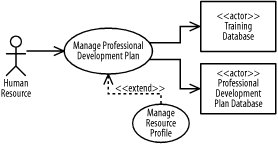
Figure B-20 shows the figure.
Figure B-20. Use-case diagram (question 2 part b)
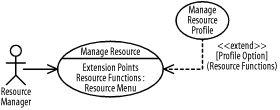
Figure B-21 shows the figure.
Figure B-21. Use-case diagram (question 2 part c)
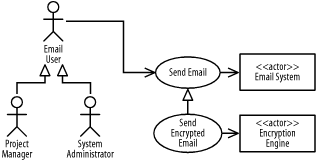
Notice that a generalization relationship is used from the Send Encrypted Email use case to the Send Email use case, because when sending email and selecting the secure option, the whole interaction with the system is secure, not just the resulting email message being encrypted. If only the email message was encrypted and the interaction was not, this could have been modeled as an extend relationship from the Send Encrypted Email use case to the Send Email use case, and the Send Encrypted Email use case would have been named Encrypt Email.
Figure B-22 shows the figure.
Figure B-22. Use-case diagram (question 2 part d)
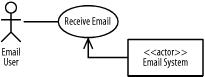
Figure B-23 shows the figure.
Figure B-23. Use-case diagram (question 2 part e)
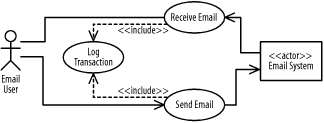
Figure B-24 shows the resulting diagram, which includes all the steps in this question.
Figure B-24. Use-case diagram (question 2)
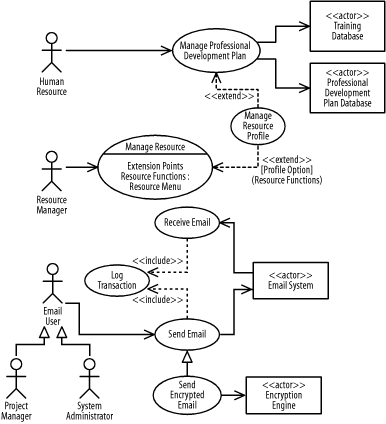
The following describes the rules for what use cases must be developed before other use cases:
The Log Activity use case must be developed before the Manage Project, Manage Resource, and Administer System use cases.
The Manage Project use case must be developed before the Maintain Project, Maintain Activity, and Maintain Task use cases.
The Publish Status use case must be developed before the Generate Report and Generate Website use cases.
The Administer System use case must be developed before the Startup System and Shutdown System use cases.
The Startup System use case must be developed before the Restore Data use case.
The Shutdown System use case must be developed before the Backup System use case.
The Manage Professional Development Plan use case must be developed before the Manage Resource Profile use case.
The Manage Resource use case must be developed before the Manage Resource Profile use case.
The Log Transaction use case must be developed before the Send Email and Receive Email use cases.
The Send Email use case must be developed before the Send Encrypted Email use case.
B.1.3 Chapter 5
The following describes the figure:
The User Interface package uses the Utility package and the IBusiness Processing interface provided by the Business Processing subsystem.
The Business Processing subsystem provides the IBusiness Processing interface, uses the Utility package, and uses the IConsumable and IProducible interfaces provided by the Data subsystem.
The Data subsystem uses the Utility package and provides the IConsumable and IProducible interfaces.
The User Interface package, Business Processing subsystem, and Data subsystem reside in the User Interface component.
The User Interface component provides the IBusiness Processing, IConsumable, and IProducible interfaces.
The User Interface component is deployed on the Desktop Client node.
The Desktop Client node is connected to the Backup Storage Device node.
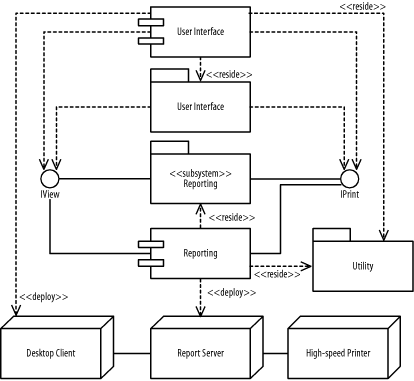
The following describes the figure: there are User Interface and Utility packages, and a Reporting subsystem that provides the IView and IPrint interfaces.
Figure B-25 shows the figure.
Figure B-25. Packages and subsystems (question 2 part a)
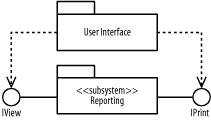
Figure B-26 shows the figure.
Figure B-26. Component diagram (question 2 part b)
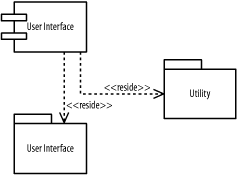
Figure B-27 shows the figure.
Figure B-27. Component diagram (question 2 part c)
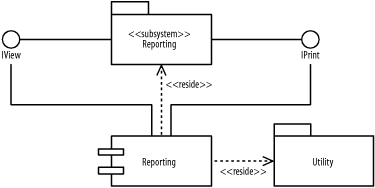
Figure B-28 shows the figure.
Figure B-28. Deployment diagram (question 2 part d)
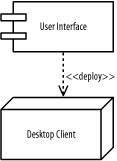
Figure B-29 shows the figure.
Figure B-29. Deployment diagram (question 2 part e)
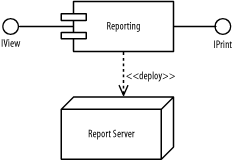
Figure B-30 shows the figure.
Figure B-30. Deployment diagram (question 2 part f)
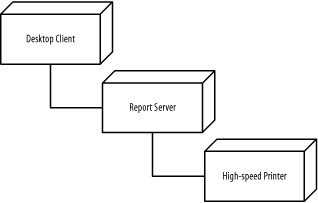
Figure B-31 shows the resulting diagram, which includes all the steps in this question.
Figure B-31. Components and nodes (question 2)