Network Standards
If the different network standards in place today were in print, they would fill volumes upon volumes of text. These network standards serve specific purposes, as defined by the standard itself. For example, there is a standard for you to communicate across the Internet and a different standard for you to talk across the telephone network.
Standards dictate almost everything that surrounds us during the course of a day. The television signal of your TV follows a standard, as does the lid on your "to-go" coffee cup. Some standards, such as the television signal, are regulated by an administering body such as the National Television System Committee (NTSC) or the new High-Definition Television (HDTV) standard developed in part by the Advanced Television System Committee (ATSV), whereas other standards are nonregulated.
These nonregulated standards are known as de facto standards and become standardized over time by their use. For example, no regulating authority is responsible for "to-go" coffee cup lids, but the sizes of cups used are static, meaning that a "to-go" coffee cup from one coffee shop doesn't usually differ from a "to-go" coffee cup from another shop. Hence it is logical that the lids for these cups will be the same, regardless of the manufacturer.
Standards in the network world work the same way. There are regulated standards such as those published by the International Telecommunication Union (ITU), the American National Standards Institute (ANSI), and the Institute of Electrical and Electronics Engineers (IEEE). There are also de facto standards, such as those put forth by network vendors, such as Cisco, and adopted over time by everyone else.
ITU (International Telecommunication Union)
TheInternational Telecommunication Union (ITU) is made up of telecommunication policy makers and regulators, network operators, equipment manufacturers, hardware and software developers, regional standards-making organizations, and financing institutions. The activities, policies, and strategic direction of the ITU are determined and shaped by the industry it serves.
The three sectors of the ITU are Radiocommunication (ITU-R), Telecommunication Standardization (ITU-T), and Telecommunication Development (ITU-D).
ITU-R draws up the technical characteristics of terrestrial and space-based wireless services and systems, and develops operational procedures. It also undertakes the important technical studies, which serve as a basis for the regulatory decisions made at radio communication conferences.
ITU-T experts prepare the technical specifications for telecommunication systems, networks, and services, including their operation, performance, and maintenance. Their work also covers the tariff principles and accounting methods used to provide international service.
ITU-D experts focus their work on the preparation and development of recommendations, opinions, guidelines, handbooks, manuals and reports. These documents provide decision makers with "best business practices" relating to a host of issues ranging from development strategies and policies to network management.
Each of the three ITU sectors works through conferences and meetings at which members negotiate the agreements that serve as the basis for the operation of global telecommunication services. The activities of the ITU cover all aspects of telecommunication: setting standards that facilitate seamless interworking of equipment and systems on a global basis; adopting operational procedures for the vast and growing array of wireless services; and designing programs to improve telecommunication infrastructure in the developing world.
ANSI (American National Standards Institute)
American National Standards Institute (ANSI) serves as administrator and coordinator of the United States private-sector voluntary standardization system. ANSI was founded in 1918 by five engineering societies and three governmental agencies, and is a private, nonprofit membership organization. ANSI ensures each foot-long ruler is accurate in its dimensions, for instance, essentially using a ruler to measure a ruler. ANSI ensures that each inch on the ruler is in fact 1 inch, and that the foot-long ruler is in fact made up of 12 of these inches.
ANSI, like the ITU, regulates telecommunications standards; unlike the ITU, however, ANSI regulates standards in North America, whereas the ITU regulates standards in Europe. For example, ANSI regulates the T1 telecommunications standard, whereas the ITU regulates the E1 telecommunications standard in Europe.
IEEE 802 Group
The Institute of Electrical and Electronics Engineers (IEEE, pronounced "eye-triple-E") is a nonprofit, technical professional association in 150 countries. The IEEE is a leading authority in technical areas ranging from computer engineering, to biomedical technology, to telecommunications, to electric power, to aerospace and consumer electronics. The IEEE produces 30 percent of the world's published literature in electrical engineering, computers, and control technology and has nearly 900 active standards with 700 under development.
Some of the best-known IEEE standards are as follows:
IEEE 802.1 (LAN/MAN)
IEEE 802.3 (Ethernet)
IEEE 802.5 (Token Ring)
IEEE 802.11 (Wireless LAN)
IEEE 802.1 LAN/MAN Standards
The IEEE 802.1 group defined internetworking standards, with IEEE 802.1d and IEEE 802.1q used in the local-area networking environment. The standards are as follows:
IEEE 802.1d?Spanning Tree Protocol (STP)? STP is a link-management protocol that is part of the IEEE 802.1 standard for Media Access Control bridges and is used for Layer 2 redundancy. Using the spanning-tree algorithm, STP provides redundant paths through the LAN while preventing loops in the LAN that are created by multiple active paths between stations. These multiple paths, or loops, occur when there are alternative routes between hosts. To establish path redundancy, STP creates a tree that spans all the switches in an extended network, forcing redundant paths into a standby, or blocked, state. STP allows for one active path at a time between any two network devices, preventing loops, but establishing the redundant links as a backup (in case the primary link fails). If a change occurs in the LAN, such as a network segment becoming unreachable, the spanning-tree algorithm reconfigures the tree topology and reestablishes the link by activating the standby path. Without STP in place, both primary and redundant connections might be simultaneously live, resulting in an endless loop of traffic on the LAN. Chapter 7, "Spanning Tree Protocol (STP)," discusses STP in more detail.
IEEE 802.1q?virtual LANs (VLANs)? A VLAN is a network of computers that behaves as if the computers are connected to the same physical network segment, even though these computers might be physically located on different segments of a LAN. VLANs are configured in software and are not limited by physical location or to specific switch ports. This makes VLANS flexible to use within a network. One of the advantages of VLANs is that when a computer is physically moved to another location, it can stay on the same VLAN without any end-device or protocol reconfiguration. Chapter 9, "Switching Security," discusses VLANs in more detail.
IEEE 802.3 Ethernet Standards
Several Ethernet standards are used in today's network environment. Some of these standards dictate the bandwidth and operation of the Ethernet LAN, such as Ethernet and Fast Ethernet, whereas other standards dictate how these Ethernet networks function, such as the STP.
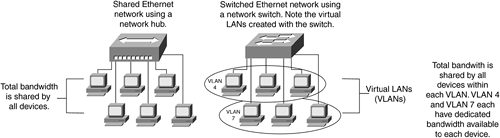
Ethernet is a half-duplex shared-media LAN in which each station on the segment uses part of the total bandwidth. The total LAN bandwidth for Ethernet is 10 megabits per second (Mbps?Ethernet) or 100 Mbps (Fast Ethernet). Ethernet and Fast Ethernet can operate in either half-duplex or full-duplex mode; half-duplex Ethernet shares the LAN media, whereas full-duplex mode has separate LAN media dedicated to the sending and receiving side of the network interface card (NIC). The 1000 Mbps (Gigabit Ethernet) is not a shared-media LAN implementation because Gigabit Ethernet operates in full-duplex mode only. Hubs enable shared-media LANs, and switches enable dedicated-media LANs. With switched Ethernet, each sender and receiver pair has the full bandwidth available for use, as illustrated in Figure 2-5.
Figure 2-5. Switched and Shared Ethernet Networks
note
Switched Ethernet networks enable the creation of virtual LANs, or VLANs. |
The IEEE 802.3 standards define how the Ethernet standard is used in the networking environment. These 802.3 standards are as follows:
IEEE 802.3 (Ethernet)? 10-Mbps Ethernet specification developed by Xerox, served as the basis for the IEEE 802.3 standard. This specification describes the use of carrier sense multiple access collision detect (CSMA/CD) in handling the simultaneous demands for network access. Often used in LAN environments.
IEEE 802.3u (Fast Ethernet)? 100-Mbps Ethernet specification working at 10 times the speed of 10-Mbps Ethernet. Often used in LAN environments.
IEEE 802.3z (Gigabit Ethernet)? 1000-Mbps/1-Gbps Ethernet specification that transfers data at 1 gigabit per second (1000 Mbps). Often used in large LAN environments at the core layer.
IEEE 802.3ae (10Gigabit Ethernet)? 10,000-Mbps/10-Gbps Ethernet specification that transfers data at 10 gigabits per second (10,000 Mbps). Often used in metropolitan-area networks (MANs).
note
CSMA/CD is a standard enabling Ethernet hosts to detect a collision. In a half-duplex Ethernet environment, collisions occur when two nodes begin sending traffic at the same time. Collisions do not occur in full-duplex Ethernet environments. After detecting a collision, the host waits a random amount of time and then tries retransmitting the message. If the sending host detects a collision again when trying to send the same frame, the host waits an exponentially increasing amount of time after each transmission attempt before resending. |
IEEE 802.5 Token Ring Standards
With Ethernet, any host on the network can send data at any time, as long as no one else is on the line. In contrast, the Token Ring works by passing a token around the network, almost like a relay-race runner passing the baton to the next runner. When a host has possession of this token, it has the right to send data across the network, just as the relay runner can run only when in possession of the baton. If a host has nothing to send, it passes the token to the next host down the line in the network.
IEEE 802.5 is a related specification and compatible with the Token Ring standard developed by IBM. Token Ring refers to both IBM Token Ring and IEEE 802.5 network implementations. IBM originally developed the Token Ring network in the 1970s; however, IBM gave up on Token Ring in favor of Ethernet several years ago.
Token Ring is a LAN in which all the hosts are arranged in a logical circle. A special frame, called the token, travels around the circle. To send a message, a host catches the token, attaches its data, and then lets it continue to travel around the network. Token Ring is not found in many LANs nowadays because of its slow speed as compared to Ethernet LANs.
note
The IEEE 802.5 specification was modeled after the IBM Token Ring specification. |
IEEE 802.11 Wireless LAN (WLAN) Standards
The IEEE 802.11 standard refers to a family of specifications developed for wireless LAN technology. IEEE 802.11 specifies an over-the-air interface between a wireless client and a base station, such as a wireless laptop and a wireless base unit or between two wireless clients, such as between two wireless laptops.
Figure 2-6 illustrates a wireless LAN between a laptop and a base unit, with the base unit connected to the Internet, either in the home or the office. The base unit can enable multiple users to share the same Internet connection as long as each user has a wireless-LAN-capable device. The benefit here is straightforward: no wires to get tangled or cables to be hidden. Wireless LANs raise other issues?the most notable is the broadcast of your data into the open air. Wireless LANs should not be implemented without some sort of encryption to protect your data from being stolen out of the air.
Figure 2-6. Wireless LAN Between a Laptop and a Base Unit
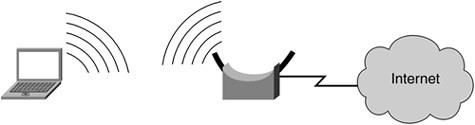
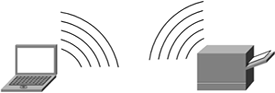
Figure 2-7 illustrates a wireless LAN that might also be found in a home or office. This configuration demonstrates the same sharing concept of the previous example, but this time users are sharing a wireless printer. The benefit here is the same: no wires.
Figure 2-7. Wireless LAN Between a Laptop and a Printer
note
The printer itself does not have to be wireless capable or wireless ready; the printer can be attached to a wireless base unit to enable wireless connectivity.






