Securing the Device
The first layer of security to consider is that provided by the device itself. Various vendors may employ different mechanisms to secure a device or rely on the facilities of the underlying platform and operating system, such as the Pocket PC running on Windows CE. In addition, organizations can augment the OS software with third-party solutions. Generally, the types of security that can be used to protect the device fall into the categories of authentication, antivirus protection, and lockdown.
Authentication
The simplest step organizations can take to protect devices on which Compact Framework applications run is to require some form of authentication. For example, Pocket PC 2002 and later devices running Windows CE support both simple and strong power-on password authentication for the device.[3] By enabling this feature on the device, the user must type in a simple four-character password or a more complex seven-character password (with upper- and lowercase letters, in addition to numbers or punctuation) at a configurable interval that defaults to one hour as shown in Figure 9-1.
[3] This feature can be downloaded for Pocket PC 2000 by installing Microsoft's Password for Pocket PC at www.microsoft.com/windowsmobile/resources/downloads/pocketpc/powertoys.mspx.
Figure 9-1. Using Pocket PC Power-On Authentication. This screen shot shows the interface used to configure the device for power-on password protection. Note that the reauthentication delay is set to one hour by default.
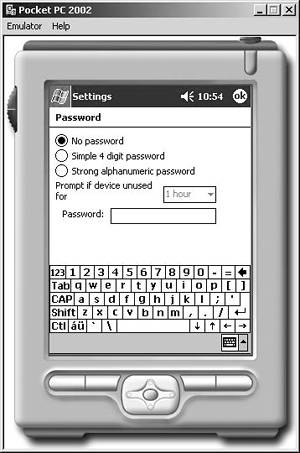
If a user enters an incorrect password, an exponentially increasing time delay is enforced, making it very difficult to guess the password repeatedly. Third-party vendors such as Trust Digital, through its PDASecure product,[4] provide power-on password authentication with additional options that include locking the device after a certain number of invalid password attempts and additionally requiring a soft reset, hard reset, or even "wiping" the device of its data.
[4] See www.trustdigital.com/prod15b.htm.
Although this form of authentication can be quite effective, it is based on knowledge of the password that can perhaps be obtained elsewhere. Implementing authentication based on possession of a physical item, such as a smartcard or a cryptographic certificate located on a removable storage card, or based on who the user is through biometric (fingerprint) or signature identification, requires third-party products. Various vendors such as A2000 Distribution, Certicom Corporation, and Cloakware Corporation provide a variety of such solutions.[5]
|
Antivirus Protection
Even though viruses that target mobile devices are not as prevalent as those targeting desktop computers, they are still a potential threat to any software on the device. Typically, however, devices are not damaged by viruses but rather pass them into a corporate network via e-mail attachments and documents.
There are, as you might expect, a variety of antivirus packages on the market for devices such as the Pocket PC from vendors that include McAfee, Computer Associates, and F-Secure. In addition, personal firewall products such as VPN-1 are available from vendors such as Check Point Software Technologies.
NOTE
If antivirus and third-party authentication software is installed on the device, it is a best practice to place the software in flash ROM, rather than RAM, on the device. In this way, the software will survive a hard reset (in which the user removes the batteries); however, storing your application in RAM can also work in your favor because the application will be lost during a hard reset, thereby disallowing access to it.
Lockdown
Following the principle of reducing the attack surface, many organizations may wish to disable some features of the device. Third-party software such as PDASecure from Trust Digital, for example, does just that by password protecting or disabling infrared communications, ActiveSync, and the voice recorder.








