Overview of VPN Technologies
It is difficult to define precisely what constitutes a virtual private network (VPN) because the term means different things to different people. To some people, separation of their traffic on a network is sufficient to call it "private"; others expect encryption when they hear the word "private." The opposite seems clearer: a private network is strictly speaking completely separate from other networks. Of course, with this definition almost any network invented after the telegraph system in 1837 by Samuel Morse would be a virtual network. Today's "private" leased lines, for example, use a shared SONET or Synchronous Digital Hierarchy (SDH) infrastructure, and the physical lines or fibers carry many different "private" networks.
For any practical discussion in the context of MPLS, ATM, Frame Relay, and other VPN technologies, operators currently understand that services delivered over SONET or SDH are regarded as private because separation over these carrier technologies is so efficient that users cannot detect the sharing of core fibers.
VPNs thus exist in many different forms and have been classified in a variety of ways. All of these classifications exist because of different user requirements. VPN technologies can also be used in a nested way, that is, over an existing VPN such as a company intranet where it is possible to further define more detailed VPNs.
The criteria that distinguish VPN technologies from each other include the following:
Connection-oriented/connectionless technologies? Many VPN technologies are connection oriented. That means that a VPN user who connects to the VPN service appears to have a connection to another VPN user. Examples for connection-oriented VPNs are IPsec, GRE, and IP-in-IP. Also point-to-multipoint technologies, such as multipoint GRE (mGRE), introduced in IOS Version 12.2T, are essentially connection oriented, even if the other endpoints might not be configured but discovered dynamically.
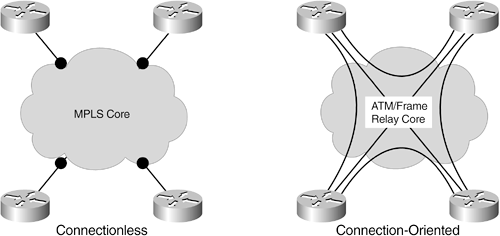
MPLS is a connectionless VPN technology: a VPN user (customer equipment) does not have a direct relationship with any other VPN user; rather, it is connected to the MPLS service as a "cloud," which ensures that packets are forwarded correctly to the other VPN user site. Specifically, a VPN user does not have explicit knowledge of other VPN users. This is one of the key advantages of MPLS IP VPNs: they scale very well because less VPN information needs to be kept at the edge. Figure 1-2 shows the differences between connectionless and connection-oriented technologies.
Figure 1-2. Connectionless Versus Connection-Oriented VPN Types
Encrypted/non-encrypted? Encrypted VPN types are typically used where confidentiality of data in transit is required, such as over a wireless network or the public Internet. The most widely used encrypting VPN technology today is IPsec, although other types based on transport layer security (TLS) or secure sockets layer (SSL) are on the increase. MPLS is by default nonencrypting. Encryption can be added (using PE-PE IPsec, for example).
Internet based/not Internet based? Some VPN types can be used over the public Internet and thus allow easy interconnection of sites worldwide, assuming availability of Internet services in these locations. IPsec, GRE, IP-in-IP, TLS, and SSH are examples of VPN technologies that can be used over the Internet. The advantage of Internet-based VPN types is their mostly worldwide availability; the disadvantage is that often no quality-of-service guarantees are available for such services.
NOTE
Today, most MPLS VPN deployments use private infrastructure. The Internet is used within a core only in exceptional cases. Many deployments use Internet-based technologies such as IPsec to connect to a PE from the outside. So while the access to the MPLS VPN core is often Internet based, the core itself is usually built on private infrastructure.
VPN technologies can only be judged in the context they are being used in. There is no overall valid definition of "good" or "bad" VPN services. For a small public organization with few but far away offices, it might be perfectly acceptable to use a simple tunneling technique, such as GRE or IP-in-IP, to be able to interconnect sites over the public Internet. For larger companies, this type of VPN would be harder to manage for scalability reasons; they might prefer MPLS-based VPNs to keep their network simpler and easier to manage. For organizations dealing with secret information, confidentiality would be essential, and they would use some encrypting VPN technology such as IPsec.
Several VPN technologies can be used together in one common solution. This is being done where different technologies address different needs. For example, IPsec VPNs can be used on top of an MPLS VPN. This type of architecture is not necessarily redundant: IPsec might be chosen because there is a need for confidentiality on the data path. Many European countries, for example, by law require encryption of personal data over any public data network, and this is often addressed by using IPsec. However, the organization still requires connectivity between its sites for its IPsec traffic to pass between the offices. This could be addressed over the public Internet, but also over ATM, Frame Relay VPN services, or MPLS. Each of these options has its advantages and disadvantages, but MPLS VPN services have been used often in the past due to consistent service guarantees not available on the public Internet, as well as to often better prices than on other VPN technologies.







