IPsec Overview
IPsec is a technology that offers security services across an IP network:
Confidentiality through the use of encryption
Authenticity through the use of peer and message authentication
Integrity through the use of message integrity checks
Anti-replay, by using authenticated sequence numbers, to guarantee freshness of a message
One of the key advantages of IPsec is that its security services are all applied in Layer 3, the network layer, just as with IP. This way, the security services remain independent of the underlying transport mechanism as well as the protocols and applications used on top of the stack.
NOTE
IPsec addresses most typical security requirements, such as confidentiality, as just discussed. An important requirement that IPsec does not provide an answer to, however, is availability. The use of IPsec typically does not make networks less vulnerable to DoS attacks.
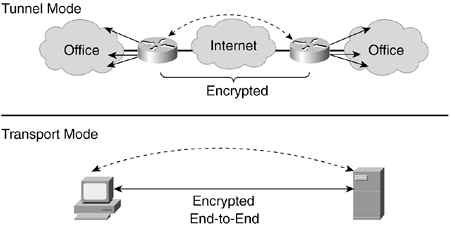
IPsec can, in principle, be applied end to end, for example, between a client and a server. IPsec transport mode can be used for this. However, the most widespread use of IPsec today is between specific IPsec gateways?in a company network, for example. In that case, traffic within an office (a trusted zone) is usually in clear, with the IPsec gateways securing the traffic over the public network. In this case, tunnel mode is used to tunnel packets securely from one office to the other. Figure 6-1 shows both transport mode and tunnel mode with their typical applications.
Figure 6-1. IPsec Transport Mode and Tunnel Mode
NOTE
In colloquial language, IPsec "encrypts" packets. Here we use the term "secure" instead because encryption is only one of several features of IPsec.
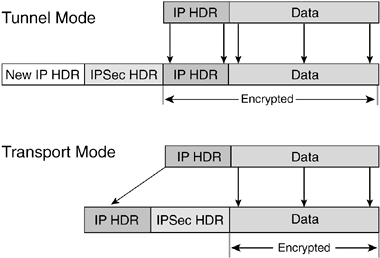
With those two connection modes, there are two ways to map clear-text IP packets into an IPsec packet. In tunnel mode, the entire clear-text IP packet is secured, and a new IP header is prepended, followed by an IPsec header that identifies the logical connection between the IPsec gateways. In transport mode, the original IP header is preserved, and the IPsec header is inserted before the secured IP packet. Figure 6-2 displays these two packet formats.
Figure 6-2. IPsec Packet Formats
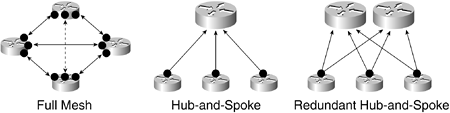
A single IPsec tunnel connects two sites. By adding more tunnels, a VPN can be constructed between the IPsec gateways. This can be done in a full mesh topology, a hub-and-spoke topology, or any mixture of the two. Figure 6-3 shows basic VPN topologies that can be built using IPsec.
Figure 6-3. IPsec VPN Topologies
When securing a network?for example, let's say a bank network with two central offices and 100 branch offices?the key design criterion is where to place the IPsec gateways. In most designs, the offices of the bank each would be considered a trusted zone, with the communication infrastructure between them being untrusted from the VPN customer's point of view. In such a design, the IPsec gateways must be inside the trusted zones for the overall VPN to remain protected with the IPsec services.
When designing an IPsec overlay network, two main topics must be discussed:
Where should the IPsec tunnels be applied?
How should the tunnels be established?
For both questions, there are a number of options. So, we'll first discuss the location of the IPsec termination points; later, we'll discuss the way tunnels are established between those sites.







