11.2 Attacking IPsec VPNs
To fully assess the security of an IPsec VPN, as with any target network or system, you need to perform enumeration, initial testing, investigation, and exploitation. Here I discuss how to enumerate, probe, and investigate vulnerable IPsec VPN components efficiently. If you have access to the wire, there are a number of complex man in the middle (MITM) and sniffing attacks that can be launched to compromise IPsec VPN tunnels; however, these attacks lie outside of the scope of this book.
11.2.1 IPsec Enumeration
ipsecscan is a Win32 command-line utility that can identify IPsec enabled devices and hosts; it's available at http://ntsecurity.nu/toolbox/ipsecscan/.[1]
[1] URLs for tools in this book are mirrored at the O'Reilly site, http://examples.oreilly.com/networksa/tools.
Example 11-1 shows ipsecscan in action, scanning from 10.0.0.1 to 10.0.0.10 for IPsec support.
Example 11-1. ipsecscan in use to identify IPsec enabled devices
D:\> ipsecscan 10.0.0.1 10.0.0.10
IPSecScan 1.1 - (c) 2001, Arne Vidstrom, arne.vidstrom@ntsecurity.nu
- http://ntsecurity.nu/toolbox/ipsecscan/
10.0.0.1 IPSec status: Indeterminable
10.0.0.2 IPSec status: Indeterminable
10.0.0.3 IPSec status: Enabled
10.0.0.4 IPSec status: Indeterminable
10.0.0.5 IPSec status: Indeterminable
10.0.0.6 IPSec status: Enabled
10.0.0.7 IPSec status: Indeterminable
10.0.0.8 IPSec status: Indeterminable
10.0.0.9 IPSec status: Indeterminable
10.0.0.10 IPSec status: Indeterminable
You can also use nmap to identify the ISAKMP service on UDP port 500. After identifying accessible ISAKMP services, you can probe and investigate these services to fingerprint and identify them.
11.2.2 Initial ISAKMP Service Probing
You can use Roy Hills' ike-scan to fingerprint the ISAKMP service and derive the software package of which it is a part. ike-scan is available for download at http://www.nta-monitor.com/ike-scan.
Example 11-2 shows ike-scan being used against the two IP addresses found in the previous example that support IPsec, identifying them as NetScreen and Cisco devices.
Example 11-2. ike-scan in use to fingerprint the service
# ike-scan --showbackoff 10.0.0.3 10.0.0.6 Starting ike-scan 1.4 (http://www.nta-monitor.com/ike-scan/) 10.0.0.3 IKE Main Mode Handshake returned (1 transforms) 10.0.0.6 IKE Main Mode Handshake returned (1 transforms) IKE Backoff Patterns: IP Address No. Recv time Delta Time 10.0.0.3 1 1065942743.329658 0.000000 10.0.0.3 2 1065942747.314266 3.984608 10.0.0.3 3 1065942751.307847 3.993581 10.0.0.3 4 1065942755.301361 3.993514 10.0.0.3 5 1065942759.294996 3.993635 10.0.0.3 6 1065942763.291496 3.996500 10.0.0.3 7 1065942767.282147 3.990651 10.0.0.3 8 1065942771.275722 3.993575 10.0.0.3 9 1065942775.269286 3.993564 10.0.0.3 10 1065942779.262847 3.993561 10.0.0.3 11 1065942783.253430 3.990583 10.0.0.3 12 1065942787.243944 3.990514 10.0.0.3 Implementation guess: netscreen IKE Backoff Patterns: IP Address No. Recv time Delta Time 10.0.0.6 1 1042797937.070152 0.000000 10.0.0.6 2 1042797952.061102 14.990950 10.0.0.6 3 1042797967.064137 15.003035 10.0.0.6 Implementation guess: Cisco IOS / PIX Ending ike-scan 1.4: 2 hosts scanned. 2 returned handshake; 0 returned notify
11.2.3 Investigating Known ISAKMP and IKE Weaknesses
You can identify ISAKMP and IKE security issues (such as denial-of-service conditions) if you know the type of device or host you have access to. Table 11-1 shows a number of serious remotely exploitable issues with these protocols, as listed in the ISS X-Force vulnerability database at http://xforce.iss.net.
|
XF ID |
Date |
Notes |
|---|---|---|
|
14150 |
04/02/2004 |
Check Point IKE buffer overflow |
|
10034 |
03/09/2002 |
Check Point IKE aggressive mode user enumeration |
|
10028 |
03/09/2002 |
Cisco VPN 3000 malformed ISAKMP packet denial of service |
|
9850 |
12/08/2002 |
Multiple vendor IKE response handling buffer overflow |
|
9820 |
12/08/2002 |
Cisco VPN Client IKE packet payload buffer overflow |
|
9819 |
12/08/2002 |
Cisco VPN Client IKE packet long SPI buffer overflow |
At the time of writing, one issue not listed in the X-Force list is SecurityFocus BID 8964, which covers multiple OpenBSD isakmpd IKE payload handling weaknesses. This highlights the fact that you can't rely on a single source for current vulnerability information.
The most serious ISAKMP and IKE security issues arise from poor configuration. One very serious remotely exploitable issue arises when a VPN gateway is configured with aggressive mode IKE support, and preshared keys are used as an authentication mechanism. The associated attack is known as aggressive mode IKE PSK cracking.
11.2.4 Aggressive Mode IKE PSK Cracking
Remote users who require remote access to internal network resources often use a preshared key (PSK) to authenticate. A serious flaw exists in IPsec, which can be exploited if a VPN gateway supports aggressive mode IKE, and a PSK is used to provide authentication.
A remote attacker can attempt to authenticate using aggressive mode IKE and obtain a hashed authentication response from the gateway. When using main mode IKE, this authentication response is protected using a Diffie-Hellman shared secret, but aggressive mode doesn't provide any protection. If a PSK is in use (as opposed to digital signatures or public key encryption), the aggressive mode IKE authentication response is the PSK hashed using MD5 or SHA1. This hash can be attacked offline, and the PSK compromised.
Michael Thumann has written an excellent Win32 utility called ikeprobe, which you can use to force a target VPN gateway into using aggressive mode IKE and obtain the encrypted authentication hash. You can sniff and crack the hash using a tool such as Cain & Abel (http://www.oxid.it/cain.html), which can crack both MD5 and SHA1 PSK hashes. You can download ikeprobe at http://www.ernw.de/download/ikeprobe.zip.
Example 11-3 shows ikeprobe in use against a Cisco PIX firewall at 10.0.0.3. The tool attempts to use a number of combinations of ciphers, hashes, and Diffie-Hellman groups to solicit an aggressive mode IKE response containing the hashed PSK.
Example 11-3. Probing 192.168.10.254 to obtain the PSK hash
D:\ikeprobe> ikeprobe 10.0.0.3 IKEProbe 0.1beta (c) 2003 Michael Thumann (www.ernw.de) Portions Copyright (c) 2003 Cipherica Labs (www.cipherica.com) Read license-cipherica.txt for LibIKE License Information IKE Aggressive Mode PSK Vulnerability Scanner (Bugtraq ID 7423) Supported Attributes Ciphers : DES, 3DES, AES-128, CAST Hashes : MD5, SHA1 Diffie Hellman Groups: DH Groups 1,2 and 5 IKE Proposal for Peer: 192.168.10.254 Aggressive Mode activated ... Attribute Settings: Cipher DES Hash SHA1 Diffie Hellman Group 1 0.000 3: ph1_initiated(00443ee0, 007d45b0) 0.016 3: << ph1 (00443ee0, 244) 2.016 3: << ph1 (00443ee0, 244) 5.016 3: << ph1 (00443ee0, 244) 8.016 3: ph1_disposed(00443ee0)
As this process is running, use Cain & Abel to sniff for, and crack, IKE PSK hashes. IKECrack (http://ikecrack.sourceforge.net/) is a very similar tool for use in Unix environments, but it can crack only MD5 hashes at the time of writing. Figure 11-3 shows Cain & Abel sniffing and cracking the PSK hash from the wire, as ikeprobe is run. In the figure, the preshared key is cisco.
Figure 11-3. Cain & Abel attacks the PSK authentication hash
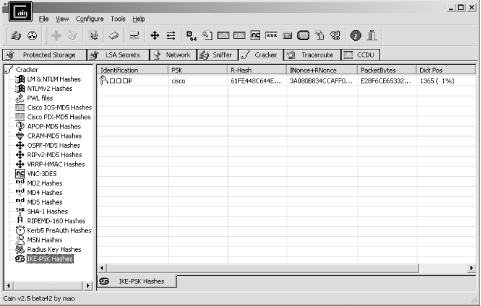
After compromising the PSK, you can use PGPnet or similar IPsec VPN client software to establish a VPN tunnel and assess the amount of internal network access granted. Michael Thumann has written an excellent step-by-step guide for configuring PGPnet after compromising the PSK; it's available as part of his PSK attack paper and is downloadable at http://www.ernw.de/download/pskattack.pdf.






