8.2 FTP Banner Grabbing and Enumeration
When finding a server running FTP, the first piece of information discovered by connecting to the service is the FTP server banner:
# ftp 192.168.0.11 Connected to 192.168.0.11 (192.168.0.11). 220 darkside FTP server ready. Name (192.168.0.11:root):
Here, the banner is that of a Solaris 9 server. Solaris 8 (also known as SunOS 5.8) and prior return the operating system detail in a slightly different banner, as follows:
# ftp 192.168.0.12 Connected to 192.168.0.12 (192.168.0.12). 220 lackie FTP server (SunOS 5.8) ready. Name (192.168.0.12:root):
If the banner is obfuscated or modified to remove service version or operating system information, the service can sometimes be identified by analyzing responses to quote help and syst commands after logging in anonymously, as shown in Example 8-1.
Example 8-1. Fingerprinting FTP services through issuing commands
# ftp 192.168.0.250 Connected to 192.168.0.250 (192.168.0.250). 220 ftp.trustmatta.com FTP server ready. Name (ftp.trustmatta.com:root): ftp 331 Guest login ok, send your complete e-mail address as password. Password: hello@world.com 230 Guest login ok, access restrictions apply. Remote system type is UNIX. Using binary mode to transfer files. ftp> quote help 214-The following commands are recognized (* =>'s unimplemented). USER PORT STOR MSAM* RNTO NLST MKD CDUP PASS PASV APPE MRSQ* ABOR SITE XMKD XCUP ACCT* TYPE MLFL* MRCP* DELE SYST RMD STOU SMNT* STRU MAIL* ALLO CWD STAT XRMD SIZE REIN* MODE MSND* REST XCWD HELP PWD MDTM QUIT RETR MSOM* RNFR LIST NOOP XPWD 214 Direct comments to ftpadmin@ftp.trustmatta.com ftp> syst 215 UNIX Type: L8 Version: SUNOS
In this example, the FTP service type and version details aren't revealed in the banner. However, by querying the server when logged in, I learn it is a Sun Microsystems FTP daemon. By performing IP fingerprinting of the port, I can probably ascertain which version of Solaris is running.
8.2.1 Analyzing FTP Banners
To analyze FTP service banners you will grab when performing assessment exercises, I've assembled the banner list in Table 8-1.
|
Operating system |
FTP banner |
|---|---|
|
Solaris 7 |
220 hostname FTP server (SunOS 5.7) ready |
|
SunOS 4.1.x |
220 hostname FTP server (SunOS 4.1) ready |
|
FreeBSD 3.x |
220 hostname FTP server (Version 6.00) ready |
|
FreeBSD 4.x |
220 hostname FTP server (Version 6.00LS) ready |
|
NetBSD 1.5.x |
220 hostname FTP server (NetBSD-ftpd 20010329) ready |
|
OpenBSD |
220 hostname FTP server (Version 6.5/OpenBSD) ready |
|
SGI IRIX 6.x |
220 hostname FTP server ready |
|
IBM AIX 4.x |
220 hostname FTP server (Version 4.1 Tue Sep 8 17:35:59 CDT 1998) ready |
|
Compaq Tru64 |
220 hostname FTP server (Digital Unix Version 5.60) ready |
|
HP-UX 11.x |
220 hostname FTP server (Version 1.1.214.6 Wed Feb 9 08:03:34 GMT 2000) ready |
|
Apple MacOS |
220 hostname FTP server (Version 6.00) ready |
|
Windows NT 4.0 |
220 hostname Microsoft FTP Service (Version 4.0) |
|
Windows 2000 |
220 hostname Microsoft FTP Service (Version 5.0) |
Various Linux distributions can be found running Washington University FTP (WU-FTP) services. ProFTP is also popular, found running on FreeBSD and Linux platforms alike. Table 8-2 lists common WU-FTP and ProFTP banners.
|
FTP service |
FTP banner |
|---|---|
|
WU-FTPD 2.4.2 |
220 hostname FTP server (Version wu-2.4.2-academ[BETA-18](1) Mon Jan 15 15:02:27 JST 1999) ready |
|
WU-FTPD 2.5.0 |
220 hostname FTP server (Version wu-2.5.0(1) Tue Jun 15 12:43:57 MST 1999) ready |
|
ProFTPD 1.2.4 |
220 ProFTPD 1.2.4 Server (hostname) [hostname] |
8.2.2 Assessing FTP Permissions
Upon gaining access to the FTP service, you should assess exactly what kind of access you have to the accessible directory structure. Many FTP exploits require an attacker to be able to create files and directories to work correctly. Example 8-2 shows an anonymous FTP session and the file permissions returned.
Example 8-2. Connecting to a Solaris 2.5.1 FTP server
# ftp 192.168.189.10 Connected to 192.168.189.10. 220 hyperon FTP server (UNIX(r) System V Release 4.0) ready. Name (hyperon.widgets.com:root): ftp 331 Guest login ok, send ident as password. Password: hello@world.com 230 Guest login ok, access restrictions apply. ftp> ls 227 Entering Passive Mode (192,168,189,10,156,68) 150 ASCII data connection for /bin/ls total 14 lrwxrwxrwx 1 0 1 7 Jun 6 1997 bin -> usr/bin dr-xr-xr-x 2 0 1 512 Jun 6 1997 dev dr-------- 2 0 1 512 Nov 13 1996 etc dr-xr-xr-x 3 0 1 512 May 7 12:21 org dr-xr-xr-x 9 0 1 512 May 7 12:23 pub dr-xr-xr-x 5 0 1 512 Nov 29 1997 usr -rw-r--r-- 1 0 1 227 Nov 19 1997 welcome.msg 226 ASCII Transfer complete.
Here I have no write access to the server and can't read anything under /etc or traverse into that directory. The welcome.msg file is accessible, but that's about it.
Regardless of whether you're logged into a Unix or Windows-based FTP server, the Unix-like permission structure is the same. Example 8-3 shows the permissions found on Microsoft's public FTP server.
Example 8-3. Assessing permissions on ftp.microsoft.com
# ftp ftp.microsoft.com Connected to 207.46.133.140 (207.46.133.140). 220 Microsoft FTP Service Name (ftp.microsoft.com:root): ftp 331 Anonymous access allowed, send identity (e-mail) as password. Password: hello@world.com 230-This is FTP.Microsoft.Com. 230 Anonymous user logged in. Remote system type is Windows_NT. ftp> ls 227 Entering Passive Mode (207,46,133,140,53,125). 125 Data connection already open; Transfer starting. dr-xr-xr-x 1 owner group 0 Nov 25 2002 bussys dr-xr-xr-x 1 owner group 0 May 21 2001 deskapps dr-xr-xr-x 1 owner group 0 Apr 20 2001 developr dr-xr-xr-x 1 owner group 0 Nov 18 2002 KBHelp dr-xr-xr-x 1 owner group 0 Jul 2 2002 MISC dr-xr-xr-x 1 owner group 0 Dec 16 2002 MISC1 dr-xr-xr-x 1 owner group 0 Feb 25 2000 peropsys dr-xr-xr-x 1 owner group 0 Jan 2 2001 Products dr-xr-xr-x 1 owner group 0 Apr 4 13:54 PSS dr-xr-xr-x 1 owner group 0 Sep 21 2000 ResKit dr-xr-xr-x 1 owner group 0 Feb 25 2000 Services dr-xr-xr-x 1 owner group 0 Feb 25 2000 Softlib 226 Transfer complete.
From reviewing the permissions of the Microsoft FTP service in Example 8-3, I find that I have no write access to the FTP server. The permission structure in its simplest sense is shown in Figure 8-1.
Figure 8-1. Unix file permissions
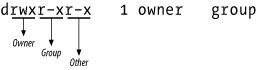
The first character defines the type of filesystem object that is being listed; directories are defined with a d, and symbolic links are defined with an l. The nine characters that follow the file-descriptor character define the owner, group, and other permissions for that file or directory. In Example 8-3, the owner has full read, write, and execute access, and group and other users have only read and execute access.
UUNet runs an FTP server that allows users to upload files to a temporary directory, shown in Example 8-4.
Example 8-4. The UUNet FTP server allows uploads to /tmp
# ftp ftp.uu.net Connected to ftp.uu.net (192.48.96.9). 220 FTP server ready. Name (ftp.uu.net:root): ftp 331 Guest login ok, send your complete e-mail address as password. Password: hello@world.com Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 227 Entering Passive Mode (192,48,96,9,225,134) 150 Opening ASCII mode data connection for /bin/ls. total 199770 d-wx--s--x 6 1 512 Jun 28 2001 etc d--xr-xr-x 3 1 512 Sep 18 2001 home drwxr-sr-x 20 21 1024 Jun 29 2001 index drwxr-sr-x 2 1 512 Jun 29 2001 inet drwxr-sr-x 5 1 512 Apr 10 14:28 info d--x--s--x 44 1 1024 Apr 16 19:41 private drwxr-sr-x 5 1 1024 Mar 8 02:41 pub drwxrwxrwt 35 21 1536 May 18 10:30 tmp d-wx--s--x 3 1 512 Jun 28 2001 usr -rw-r--r-- 1 21 8520221 Jun 29 2001 uumap.tar.Z drwxr-sr-x 2 1 2048 Jun 29 2001 vendor 226 Transfer complete.
Because I am logged in anonymously, I am interested in the last three characters of the permission information returned (drwxrwxrwt in total, with rwt relating to me). The r and w permissions mean that I have standard read and write access to the /tmp directory, and the t bit (known as the sticky bit) ensures that files can't be deleted or renamed after being created in the directory.






