6.2 Identifying the Web Service
You can identify both standard plaintext and SSL web services through analyzing responses to simple HTTP methods such as HEAD and OPTIONS. Error pages can also determine the version and service pack level of IIS web servers. Many security-conscious system administrators modify the server-information field of their web services, so deeper analysis of responses is sometimes required.
6.2.1 HTTP HEAD
In Example 6-1, I use telnet to connect to www.trustmatta.com on port 80 and issue a HEAD / HTTP/1.0 request (followed by two carriage returns).
Example 6-1. Using the HTTP HEAD method against Apache
# telnet www.trustmatta.com 80 Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'. HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:28:50 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Connection: close Content-Type: text/html; charset=iso-8859-1
I learn that the server is running Apache 1.3.27 on a Debian Linux server along with PHP 4.3.2. Example 6-2 shows the same HEAD request against www.nasdaq.com using telnet.
Example 6-2. Using the HTTP HEAD method against Microsoft IIS
# telnet www.nasdaq.com 80 Trying 208.249.117.71... Connected to www.nasdaq.com. Escape character is '^]'. HEAD / HTTP/1.0 HTTP/1.1 200 OK Connection: close Date: Mon, 26 May 2003 14:25:10 GMT Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 1.1.4322 Cache-Control: public Expires: Mon, 26 May 2003 14:25:46 GMT Content-Type: text/html; charset=utf-8 Content-Length: 64223
Here I learn that the NASDAQ web service runs on IIS 6.0, the .NET service packaged with Windows Server 2003. Note that even if the Server: information field is modified, I can differentiate between Apache and IIS web services because of differences in the formatting of the other fields presented.
Example 6-3 shows that internal IP address information is often found when querying IIS 4.0 servers.
Example 6-3. Gathering internal IP address information through IIS 4.0
# telnet www.ebay.com 80 Trying 66.135.208.88... Connected to www.ebay.com. Escape character is '^]'. HEAD / HTTP/1.0 HTTP/1.0 200 OK Age: 44 Accept-Ranges: bytes Date: Mon, 26 May 2003 16:10:00 GMT Content-Length: 47851 Content-Type: text/html Server: Microsoft-IIS/4.0 Content-Location: http://10.8.35.99/index.html Last-Modified: Mon, 26 May 2003 16:01:40 GMT ETag: "04af217a023c31:12517" Via: 1.1 cache16 (NetCache NetApp/5.2.1R3)
Since I know the internal IP address of this host, I can perform DNS querying against internal IP ranges (see Section 5.3.3) and even launch spoofing and proxy scanning attacks in poorly protected environments. Microsoft Knowledge Base article Q218180 describes workarounds for this exposure; see http://support.microsoft.com/directory/article.asp?ID=KB;EN-US;Q218180.
6.2.2 HTTP OPTIONS
A second method you can use to ascertain the web service type and version is to issue an HTTP OPTIONS request. In a similar way to issuing a HEAD request, I use telnet to connect to the web service and issue OPTIONS / HTTP/1.0 (followed by two carriage returns), as shown in Example 6-4.
Example 6-4. Using the HTTP OPTIONS method against Apache
# telnet www.trustmatta.com 80 Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'. OPTIONS / HTTP/1.0 HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:29:55 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close
Again, the Apache web service responds with minimal information, simply defining the HTTP methods that are allowed. Microsoft IIS, on the other hand, responds with a handful of fields (including Allow: and Public:), as shown in Example 6-5.
Example 6-5. Using the HTTP OPTIONS method against Microsoft IIS
# telnet www.nasdaq.com 80 Trying 208.249.117.71... Connected to www.nasdaq.com. Escape character is '^]'. OPTIONS / HTTP/1.0 HTTP/1.1 200 OK Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0 Server: Microsoft-IIS/6.0 Public: OPTIONS, TRACE, GET, HEAD, POST X-Powered-By: ASP.NET Date: Mon, 26 May 2003 14:39:58 GMT Connection: close
6.2.2.1 Common HTTP OPTIONS responses
The public and allowed methods within Apache, IIS, and other web services can be modified and customized (however, in most environments, they are not). To help you fingerprint web services, I have assembled the following list of HTTP OPTIONS responses:
- Microsoft IIS 4.0
-
Server: Microsoft-IIS/4.0 Date: Tue, 27 May 2003 18:39:20 GMT Public: OPTIONS, TRACE, GET, HEAD, POST, PUT, DELETE Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0
- Microsoft IIS 5.0
-
Server: Microsoft-IIS/5.0 Date: Tue, 15 Jul 2003 17:23:26 GMT MS-Author-Via: DAV Content-Length: 0 Accept-Ranges: none DASL: <DAV:sql> DAV: 1, 2 Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH Allow: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK Cache-Control: private
- Microsoft IIS 6.0
-
Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0 Server: Microsoft-IIS/6.0 Public: OPTIONS, TRACE, GET, HEAD, POST X-Powered-By: ASP.NET Date: Mon, 04 Aug 2003 21:18:33 GMT Connection: close
- Apache 1.3.x
-
Date: Thu, 29 May 2003 22:02:17 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close
- Apache 2.0.x
-
Date: Tue, 15 Jul 2003 17:33:52 GMT Server: Apache/2.0.44 (Win32) Allow: GET, HEAD, POST, OPTIONS, TRACE Content-Length: 0 Connection: close Content-Type: text/html; charset=ISO-8859-1
- Netscape Enterprise Server 3.6 and 4.0
-
Server: Netscape-Enterprise/4.0 Date: Thu, 12 Oct 2002 14:12:32 GMT Content-Length: 0 Allow: HEAD, GET, PUT, POST
- Netscape Enterprise Server 4.1 and 6.0
-
Server: Netscape-Enterprise/6.0 Date: Thu, 12 Oct 2002 12:48:01 GMT Allow: HEAD, GET, PUT, POST, DELETE, TRACE, OPTIONS, MOVE, INDEX, MKDIR, RMDIR Content-Length: 0
An important distinguishing feature is the order in which the data fields are presented. Apache 1.3.x servers will send us the Content-Length: field first followed by the Allow: field, whereas Apache 2.0.x servers reverse the order. The order of the Server: and Date: fields returned is also an indicator of an IIS web service.
6.2.3 Automated Web Service Fingerprinting
I've assembled a small selection of freely available tools for use from both Unix-based and Win32 platforms. These fingerprinting utilities rely on responses to various HTTP requests to identify the particular web service.
6.2.3.1 WebServerFP
This powerful tool performs eight separate checks to identify the web server based on both HTTP header and content responses to multiple HTTP methods. Even if custom error pages, along with a custom Server: string, are used, WebServerFP can identify the server. WebServerFP is available from http://examples.oreilly.com/networksa/tools/WebServerFP.zip.
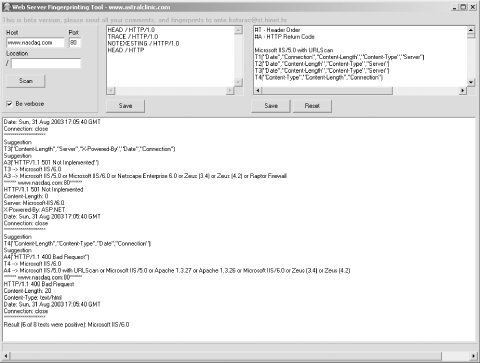
Figure 6-2 shows the tool that identifies the web service running at http://www.nasdaq.com.
Figure 6-2. WebServerFP identifies the web service as IIS 6.0
6.2.3.2 hmap
hmap is a Unix-based alternative to WebServerFP. The tool is a Python 2.2 script that issues over 100 various malformed GET and HEAD requests and analyzes the responses to determine the web service. hmap is available from http://wwwcsif.cs.ucdavis.edu/~leed/hmap/.
Example 6-6 shows how I call the script through python to display its usage.
Example 6-6. hmap usage information
# python hmap.py -h
hmap is a web server fingerprinter.
hmap [-hpgn] {url | filename}
e.g.
hmap http://localhost:82
hmap -p www.somehost.net.80
-h this info...
-n show this many of the top possible matches
-p run with a prefetched file
-g gather only (don't do comparison)
-c show this many closest matches
Example 6-7 shows hmap in use against http://www.trustmatta.com, identifying the web server by performing 123 separate HTTP tests and analyzing the results.
Example 6-7. Running hmap against http://www.trustmatta.com
# python hmap.py http://www.trustmatta.com
gathering data from: http://www.trustmatta.com
matches : mismatches : unknowns
Apache/1.3.23 (RedHat Linux 7.3) 113 : 2 : 8
Apache/1.3.27 (Red Hat 8.0) 113 : 2 : 8
Apache/1.3.26 (Solaris 8) 111 : 4 : 8
Apache 1.3.27 (FreeBSD 4.7) 111 : 4 : 8
Apache/1.3.27 (FreeBSD 5.0) 110 : 5 : 8
Due to the fact that the number of mismatches recorded is higher for Solaris and FreeBSD versions of Apache, it is more likely that the web server is running Apache 1.3.23 to 1.3.27 on a Linux platform. Ideally, you should cross-validate this information with IP fingerprinting to get a better idea of the operating platform (depending on firewall configuration).
6.2.3.3 404print
Erik Parker of Digital Defense, Inc. (http://www.digitaldefense.net) put together a useful utility that can fingerprint IIS web servers to ascertain the exact version of IIS and also the service pack and patch level of the host. The tool is available from http://www.digitaldefense.net/labs/tools/404print.c.
Example 6-8 shows that after downloading and compiling 404print.c, you can use it from any Unix-like environment.
Example 6-8. Building and using the 404print tool
# cc -o 404print 404print.c # ./404print IIS 404 Fingerprinter Copyright 2003 Digital Defense, Inc. Written By: Erik Parker <erik.parker@digitaldefense.net> Usage: ./404print [options] IP -h Print a summary of the options -v Print Version information -p Port To use -s File to request (Default: DDI-BLAH.FOO) # ./404print www.microsoft.com Server: Microsoft-IIS/6.0 Unknown Content-Length: 194 # ./404print www.example.org Server: Microsoft-IIS/5.0 Service Pack 3 or 4 # ./404print 192.168.189.40 Server: Microsoft-IIS/4.0 Service Pack 3
Often, enterprise web environments (e.g., Microsoft, eBay, NASDAQ, etc.) use custom error pages that redirect users back to the front page, so the content-length is unknown to the 404print tool. But overall, it is a useful tool and gives good insight into target server configuration if it is running Microsoft IIS.
6.2.4 Identifying the Web Service Through an SSL Tunnel
When identifying SSL encrypted web services (typically found running on port 443), you can issue the same HEAD and OPTIONS requests. First, you should set up an SSL tunnel using a tool such as stunnel (available from http://www.stunnel.org). At the time of writing, the latest stable stunnel release is Version 4.0.4; it can be run from Windows and Unix-like environments.
Here's a simple stunnel.conf file that creates an SSL tunnel to secure.example.com:443 and listens for plaintext traffic on the local port 80:
client=yes verify=0 [psuedo-https] accept = 80 connect = secure.example.com:443 TIMEOUTclose = 0
After creating this configuration file in the same directory as the executable, simply run stunnel (which runs in the system tray in Windows or forks into background under Unix) and connect to 127.0.0.1 on port 80 as shown in Example 6-9. The program negotiates the SSL connection and allows the user to query the target web service through the tunnel.
Example 6-9. Issuing requests to the HTTP service through stunnel
# telnet 127.0.0.1 80 Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. HEAD / HTTP/1.0 HTTP/1.1 200 OK Server: Netscape-Enterprise/4.1 Date: Mon, 26 May 2003 16:14:29 GMT Content-type: text/html Last-modified: Mon, 19 May 2003 10:32:56 GMT Content-length: 5437 Accept-ranges: bytes Connection: close






