14.5 Methodology Flow Diagram
The overall methodology is relatively straightforward; it covers initial and full network scanning, low-level network testing (depending on the type of network and filtering mechanisms), accessible service identification, investigation of vulnerabilities, and qualification of vulnerabilities. Figure 14-1 shows this flow diagram at a high-level and the data passed between each process.
Figure 14-1. A process flow diagram for network security assessment
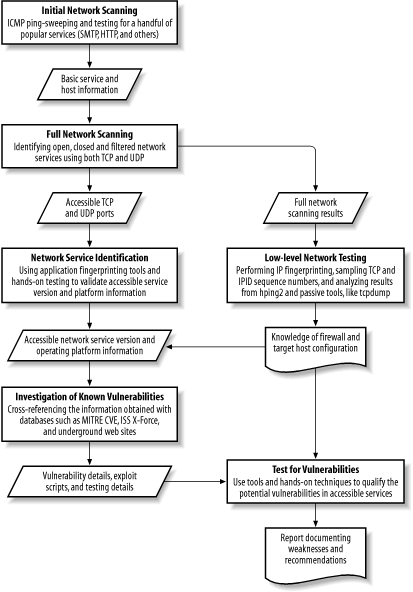
If you are new to security assessment, you will soon realize that it is highly time-consuming to search and cross reference various web sites and information sources for accurate vulnerability information. The "Investigation of Known Vulnerabilities" component shown in Figure 14-1 will prove hard to carry out the first few times you try, but after a while, you will be able to read through the port scan results, and get a good idea of the vulnerabilities to test for, and the exploits to use.






