Foreword
Foreword
After managing the performance of over 20,000 infrastructure and applications penetration tests, I have come to realize the importance of technical testing and providing information security assurance.
This book accurately defines a pure technical assessment methodology, giving you the ability to gain a much deeper understanding of the threats, vulnerabilities, and exposures modern public networks face. The purpose for conducting the tens of thousands of penetration tests during my 20+ years working in information systems security was "to identify technical vulnerabilities in the tested system in order to correct the vulnerability or mitigate any risk posed by it." In my opinion, this is a clear, concise, and perfectly wrong reason to conduct penetration testing.
As you read this book, you will realize that vulnerabilities and exposures in most environments are due to poor system management, patches not installed in a timely fashion, weak password policy, poor access control, etc. Therefore, the principal reason and objective behind penetration testing should be to identify and correct the underlying systems management process failures that produced the vulnerability detected by the test. The most common of these systems management process failures exist in the following areas:
System software configuration
Applications software configuration
Software maintenance
User management and administration
Unfortunately, many IT security consultants provide detailed lists of specific test findings and never attempt the higher order analysis needed to answer the question of "why." This failure to identify and correct the underlying management cause of the test findings assures that, when the consultant returns to test the client after six months, a whole new set of findings will appear.
If you are an IT professional who is responsible for security, use this book to help you assess your networks; it is effectively a technical briefing of the tools and techniques that your enemies can use against your systems. If you are a consultant performing security assessment for a client, it is vital that you bear in mind the mismanagement reasons for the vulnerabilities, as discussed here.
Several years ago, my company conducted a series of penetration tests for a very large international client. The client was organized regionally; IT security policy was issued centrally and implemented regionally. We mapped the technical results to the following management categories:
- OS configuration
-
Vulnerabilities due to improperly configured operating system software
- Software maintenance
-
Vulnerabilities due to failure to apply patches to known vulnerabilities
- Password/access control
-
Failure to comply with password policy and improper access control settings
- Malicious software
-
Existence of malicious software (Trojans, worms, etc.) or evidence of use
- Dangerous services
-
Existence of vulnerable or easily exploited services or processes
- Application configuration
-
Vulnerabilities due to improperly configured applications
We then computed the average number of security assessment findings per 100 systems tested for the total organization and produced the chart shown in Figure P-1.
Figure P-1. Average vulnerabilities by management category
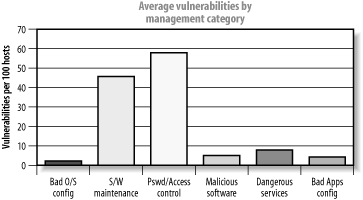
We then conducted a comparison of the performance of each region against the corporate average. The results were quite striking, as shown in Figure P-2 (above the average is bad, with more findings than the corporate average).
Figure P-2. Regional comparisons against the corporate average
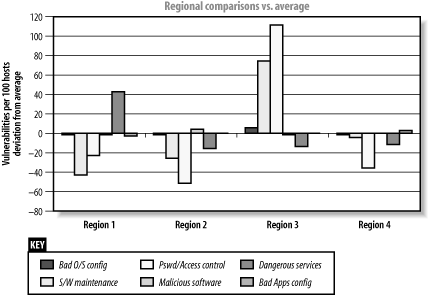
Figure P-2 clearly shows discernible and quantifiable differences in the effectiveness of the security management in each of the regions. For example, the IT manager in region 3 clearly was not performing software maintenance or password/access controls management, and the IT manager in region 1 failed to remove unneeded services from his systems.
It is important that, as you read this book, you place vulnerabilities and exposures into categories and look at them in a new light. You can present a report to a client that fully documents the low-level technical issues at hand, but unless the underlying high-level mismanagement issues are tackled, network security won't improve, and different incarnations of the same vulnerabilities will be found later on. This book will show you how to perform professional Internet-based assessment, but it is vital that you always ask the question "why are these vulnerabilities present?"






