Recipe 2.22 Building Complex Rule Trees
2.22.1 Problem
You want to construct complex firewall behaviors, but you are getting lost in the complexity.
2.22.2 Solution
Be modular: isolate behaviors into their own chains. Then connect the chains in the desired manner.
For iptables:
# iptables -N CHAIN1 # iptables -N CHAIN2 # iptables -N CHAIN3 # iptables -N CHAIN4 # iptables -N CHAIN5
Add your rules to each chain. Then connect the chains; for example:
# iptables -A INPUT ...specification... -j CHAIN1 # iptables -A CHAIN1 ...specification... -j CHAIN2 # iptables -A CHAIN2 ...specification... -j CHAIN3 # iptables -A INPUT ...specification... -j CHAIN4 # iptables -A INPUT ...specification... -j CHAIN5
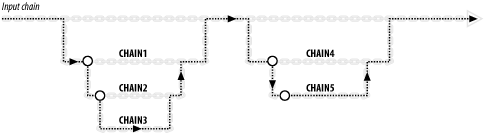
to create a rule structure as in Figure 2-1.
Figure 2-1. Building rule chain structures in iptables or ipchains
For ipchains:
# ipchains -N chain1 # ipchains -N chain2 # ipchains -N chain3 # ipchains -N chain4 # ipchains -N chain5
Add your rules to each chain. Then connect the chains, for example:
# ipchains -A input ...specification... -j chain1 # ipchains -A chain1 ...specification... -j chain2 # ipchains -A chain2 ...specification... -j chain3 # ipchains -A input ...specification... -j chain4 # ipchains -A input ...specification... -j chain5
to create the same rule structure as in Figure 2-1.
2.22.3 Discussion
Connecting chains is like modular programming with subroutines. The rule:
# iptables -A CHAIN1 ...specification... -j CHAIN2
creates a jump point to CHAIN2 from this rule in CHAIN1, if the rule is satisfied. Once CHAIN2 has been traversed, control returns to the next rule in CHAIN1, similar to returning from a subroutine.
2.22.4 See Also
iptables(8), ipchains(8).






