7.8 Citrix
Citrix is a scalable thin-client Windows service that is accessed directly through TCP port 1494 server-side. The protocol that Citrix uses is known as Independent Computing Architecture (ICA). After finding a server with TCP port 1494 open, you should use a Citrix ICA client to connect to the service for further investigation (available from http://www.citrix.com/download/ica_clients.asp).
7.8.1 Using The Citrix ICA Client
When you run the client software, you should add a new ICA connection, using TCP/IP to communicate with the server and provide the IP address of the host with port 1494 open as in Figure 7-4.
Figure 7-4. Setting up the ICA client to connect
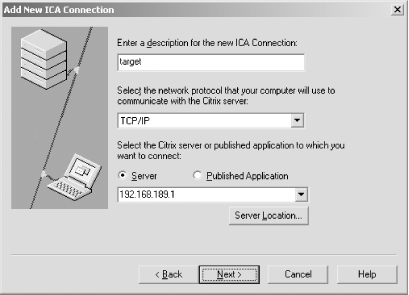
Username, password, and application details can all be left blank if you have no insight into the Citrix configuration. Upon entering the details correctly and connecting, a login screen like that shown in Figure 7-5 (depending on the server configuration) appears.
Figure 7-5. A Windows 2000 Server logon prompt through Citrix ICA
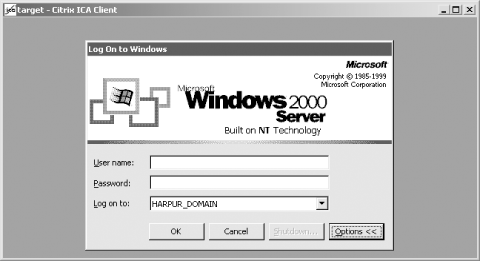
In some instances, you log into a Windows desktop environment with access to published applications such as Microsoft Word. In the case of having to authenticate first (as in Figure 7-5), the options are to provide a username and password combination that has already been compromised or to launch a brute-force attack.
7.8.2 Accessing Nonpublic Published Applications
If the Citrix server is configured to allow access only to specific published applications (i.e., doesn't drop you down to a logon screen), you can use a few techniques to enumerate and access these applications. Ian Vitek (http://www.ixsecurity.com) released two tools at DEF CON 10 to perform Citrix enumeration and attack.
- http://packetstormsecurity.org/defcon10/dc10-vitek/citrix-pa-scan.c
- http://packetstormsecurity.org/defcon10/dc10-vitek/citrix-pa-proxy.pl
Example 7-20.uses the citrix-pa-scan utility to list nonpublic published applications.
Example 7-20. Using citrix-pa-scan to list published applications
# ./citrix-pa-scan 212.123.69.1
Citrix Published Application Scanner version 1.0
By Ian Vitek, ian.vitek@ixsecurity.com
212.123.69.1: Printer Config
Admin Desktop
i-desktop
To connect to these published applications when the master browser isn't publicly accessible, you can use the citrix-pa-proxy script to provide spoofed master browser details to the Citrix server as the connection is initiated:
# perl citrix-pa-proxy.pl 212.123.69.1 192.168.189.10
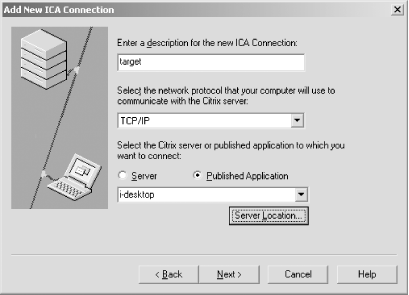
The proxy now listens on 192.168.189.10 and forwards ICA traffic to 212.123.69.1. Next point your ICA client at the proxy (setting it as your master browser through the Server Location button), and specify the published application you wish to connect to, as shown in Figure 7-6.
Figure 7-6. Connecting to a specific published application
Ian Vitek presented and demonstrated these tools at DEF CON 10. His presentation and supporting material is available from the Packet Storm archive at http://packetstormsecurity.org/defcon10/dc10-vitek/defcon-X_vitek.ppt.
7.8.3 Citrix Vulnerabilities
No serious process-manipulation vulnerabilities have been reported in Citrix Metaframe 1.8 or ICA to date. Citrix NFuse 1.6 and prior (a web-based Citrix system that allows users to access ICA applications and programs through a web browser) have known medium-risk vulnerabilities relating to authentication, information disclosure, and cross-site scripting issues. I recommend that you check sites such as MITRE CVE and ISS X-Force for details of current issues.






