Authentication
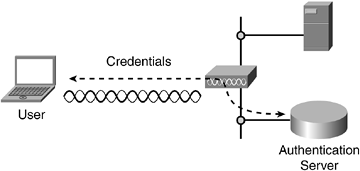
The use of mutual authentication is important in a wireless network. This will guard against many security issues, such as man-in-the-middle attacks. With mutual authentication, the wireless client and the wireless network must prove their identity to each other. This process uses an authentication server, such as Remote Authentication Dial-In User Service (RADIUS), to perform the authentication. Figure 8-6 illustrates the process of authentication.
Figure 8-6. Authentication Verifies the Identity of Users and Client Devices Through Credentials, Such as Passwords and Digital Certificates
802.11 Authentication Vulnerabilities
WEP only provides a method for authenticating radio NICs to access points, not the other way around. As a result, a hacker can reroute data through an alternate unauthorized path that avoids other security mechanisms. Instead of one-way authentication, wireless networks need to implement mutual authentication to avoid this problem.
When a wireless client becomes active, it searches the medium for beacons broadcast by access points. By default, the access point broadcasts beacons containing the service set identifier (SSID) of the access point, as well as other parameters. The access point only enables association if the client SSID matches the access point SSID. This process offers a basic, but weak, form of authentication.
The major vulnerability is the fact that the SSID is sent unencrypted, which makes it visible to wireless packet sniffers. Because of this, a hacker can easily identify the SSID within the beacon frame and authenticate with the wireless network. Even if the access point is set not to broadcast the SSID?an optional feature available in only a few access points?sniffers can still obtain the SSID from association request frames sent from client devices to the access point.
802.11 offers, by default, a form of authentication called open systems authentication. In this mode, the access point grants approval for any request for authentication. The client simply sends an authentication request frame, and the access point responds with an authentication approval. This allows anyone having the correct SSID to associate with the access point.
The 802.11 standard also includes shared key authentication, an optional, more advanced form of authentication. This is a four-step process:
- The client sends an authentication request frame.
- The access point responds with a frame containing a string of characters called challenge text.
- The client then encrypts the challenge text using the common WEP encryption key. The client sends the encrypted challenge text back to the access point, which decrypts the text using the common key and compares the result with the text originally sent.
- If the decrypted text matches, the access point authenticates the client.
This seems adequate for authentication, but a problem is that shared key authentication only proves that the client has the correct WEP key.
MAC Filters
Some wireless base stations offer medium access control (MAC) filtering. When implementing MAC filtering, the access point examines the source MAC address of each incoming frame. The access point will deny frames without a MAC address that matches a specific list programmed by the administrator. As a result, MAC filtering provides a primitive form of authentication.
MAC filtering, however, has some weaknesses. For example, WEP encryption does not encrypt the MAC address field of the frame. This allows a hacker to easily sniff the transmission of frames and discover valid MAC addresses. And, a hacker can use freely available software to change the MAC address radio NICs to match a valid MAC address. This enables the hacker to masquerade as a real user and fool the access point when the legitimate user is not present on the network.
In addition, MAC filtering can be tedious to manage when there are several users. An administrator must enter each user's MAC address in a table, and then make applicable changes when new users come about. For example, an employee from another company location might need access to the wireless LAN during a visit. The administrator must determine the MAC address and program it in the system before the visitor can access the network. MAC address filtering might be adequate for smaller home and office applications, but the hands-on nature of this approach is not desirable by administrators of enterprise wireless networks.
Authentication Using Public Key Cryptography
In addition to protecting information from hackers, stations can use public key cryptography to authenticate themselves to other stations or access points. This might be necessary before an access point or controller allows a particular station to interface with a protected side of the network. Likewise, the client can authenticate the access point in a similar manner.
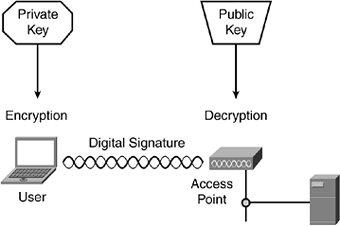
A station authenticates itself by encrypting a string of text within a packet using its private key. The receiving station decrypts the text with the sending station's public key. If the decrypted text matches some predetermined text, such as the station's name, the receiving station knows that the sending station is valid. The encryption of a particular string of text in this case acts as a digital signature. Figure 8-7 illustrates the concept of using public key encryption for authentication.
Figure 8-7. Public Key Encryption Enables Authentication
802.1x
The use of IEEE 802.1x offers an effective framework for automatically authenticating and controlling user traffic to a protected network, as well as dynamically varying encryption keys. 802.1x ties a protocol called Extensible Authentication Protocol (EAP) to both the wired and wireless network media and supports multiple authentication methods, such as token cards, Kerberos, one-time passwords, certificates, and public key authentication.
802.1x Operation
Initial 802.1x communication begins with an unauthenticated supplicant (wireless client device) attempting to connect with an authenticator (wireless base station). The base station responds by enabling a port for passing only EAP packets from the client to an authentication server located on the wired side of the base station. The base station blocks all other traffic, such as HTTP, DHCP, and POP3 packets, until the base station can verify the client's identity using an authentication server, such as RADIUS. Once authenticated, the base station opens the client's port for other types of traffic based on access rights held by the authentication server.
To get a better idea of how the 802.1x process takes place, the following specific interactions occur among the various 802.1x elements:
The client sends an EAP start message. This begins a series of message exchanges to authenticate the client; think of this as a group of visitors entering the front gate of a theme park and the group's leader (client) asking the gatekeeper (base station) whether they can enter.
The base station replies with an EAP request identity message. In the case of the theme park, the gatekeeper will ask the leader for her name and driver's license.
The client sends an EAP response packet containing the identity to the authentication server. The leader in this example will provide her name and driver's license, and the gatekeeper forwards this information to the group tour manager (authentication server), who determines whether the group has entry rights.
The authentication server uses a specific authentication algorithm to verify the client's identity. This could be through the use of digital certificates or another EAP authentication type. In this example, this process simply involves verifying the validity of the leader's driver's license and ensuring that the picture on the license matches the leader. Assume the leader is authorized.
The authentication server will their send an accept or reject message to the base station. In this case, an accept means the group tour manager at the theme park tells the gatekeeper to let the group enter.
The base station sends an EAP success packet to the client. The gatekeeper informs the leader that the group can enter the park. The gatekeeper, of course, would not let the group in if the group tour manager had rejected the group's admittance.
If the authentication server accepts the client, the base station will transition the client's port to an authorized state and forward additional traffic. This is similar to the gatekeeper automatically opening the gate to let in only people belonging to the group cleared for entry.
The basic 802.1x protocol provides effective authentication regardless of whether you implement 802.11 WEP keys or no encryption at all. Most major wireless network vendors, however, are offering proprietary versions of dynamic key management using 802.1x as a delivery mechanism. If configured to implement dynamic key exchange, the 802.1x authentication server can return session keys to the base station along with the accept message.
The base station uses the session keys to build, sign, and encrypt an EAP key message that is sent to the client immediately after sending the success message. The client can then use contents of the key message to define applicable encryption keys. In typical 802.1x implementations, the client can automatically change encryption keys frequently to minimize the risk of eavesdroppers having enough time to crack the key in current use.
Authentication Types
It's important to note that 802.1x doesn't provide the actual authentication mechanisms. When utilizing 802.1x, you need to choose an EAP type (such as EAP Transport Layer Security [EAP-TLS], EAP Tunneled Transport Layer Security [EAP-TTLS], or Cisco's Lightweight EAP [LEAP]), which defines how the authentication takes place. The software supporting the specific EAP type resides on the authentication server and within the operating system or application software on the client devices.






