Security Policies
One of the first steps in providing wireless network security is to formulate effective policies and corresponding enforcement processes. Carefully analyze security requirements and invoke an adequate level of protection. For example, encryption should be part of all wireless network implementations. WEP might be fine for home and small office deployments, but utilize better methods? such as WPA?for corporate applications. An effective mutual authentication method, such as LEAP or EAP-TLS, is also important for corporate applications.
Assessment Steps
After deploying a wireless network, you need to implement a security assessment that ensures that the WLAN complies with security policies. For most situations, this is necessary whether the network implements effective security mechanisms. Don't put too much trust in the design of a system. It's best to run tests to be certain that the network is hardened enough to guard against unauthorized persons attacking company resources.
In fact, companies should conduct regular, periodic security reviews to ensure that changes to the wireless LAN don't make the system vulnerable to hackers. An annual review might suffice for low-risk networks; but a review each quarter or more often might be necessary if the network supports high-risk information, such as financial data, postal mail routing, and manufacturing control functions.
Review Existing Security Policies
Before getting too far with the security assessment, become familiar with company policies regarding wireless network security. This provides a benchmark for determining whether a company is complying with its own policies. In addition, you'll be able to assess and make corresponding recommendations for policy modifications. Determine whether the policy leaves any room for a disgruntled employee to access company resources.
For example, the policy should describe adequate encryption and authentication mechanisms, keeping in mind that 802.11 WEP is broken. Also, the policy should mandate that all employees coordinate with the company's IT department before purchasing or installing base stations. It's important that all base stations have configuration settings that comply with the policies and provide the proper level of security. In addition, you need to ensure that security policies are disseminated to employees in an effective manner.
Review the Existing System
Meet with IT personnel and read through related documentation to gain an understanding of the system's architecture and base stations configurations. You'll need to determine whether there are any design flaws that provide weaknesses that could allow a hacker inside the system.
Learn as much as possible about existing support tools and procedures to spot potential issues. Most companies, for example, configure the base stations over the wired Ethernet backbone. With this process, the passwords sent to open a connection with a particular base stations are sent unencrypted over the wired network. As a result, a hacker with monitoring equipment hooked to the Ethernet network can likely capture the passwords and reconfigure the base station.
Interview Users
Be sure to talk with a sample of employees to determine whether they are aware of the security policies within their control. For example, do the users know that they must coordinate the purchase and installation of wireless network components with the appropriate department? Even though the policy states this, don't count on everyone having knowledge of the policy. Someone might purchase a base station from a local office supply store and install it on the corporate network to provide wireless connectivity within the office. It's also a good idea to verify that people are using personal firewalls.
Verify Configurations of Wireless Devices
As part of the assessment, walk through the facilities with base stations and use tools to capture the base station configurations. If the company has centralized support software in place, you should be able to view the configuration settings from a single console attached to the wired side of the network. This is to determine which security mechanisms are actually in use and whether they comply with effective policies.
For example, the policies might state that base stations must disable the physical console port, but while testing you determine that most base stations have the ports enabled. This would indicate noncompliance with the policies, and it would enable a hacker to reset the base station to the factory default settings with no security enabled. In addition, look at the firmware version of each base station to see if it's up-to-date. Older firmware versions might not implement the more recent patches that fix encryption vulnerabilities.
Also, investigate base stations' physical installations. As you walk through the facilities, investigate the installation of base stations by noting their physical accessibility, antenna type and orientation, and radio wave propagation into portions of the facility that don't have physical security controls. The base stations should be mounted in a position that would make it difficult for someone to physically handle the base station and go unnoticed.
A base station simply placed on top of a bookshelf, for example, would make it easy for a hacker to swap the base station with a rogue one that doesn't have any security enabled. Or, the hacker could attach a laptop to the console port to reset the base station. If the base stations are all mounted above the ceiling tiles and out of plain view, however, someone would need to use a ladder and would probably be noticed by an employee or security guard.
Identify Rogue Base Stations
A problem that's difficult to enforce and significantly undercuts a network's security is when an employee installs a personal base station in her office. Most of the time, these installations don't comply with security policies and result in an open, unsecure entry port to the corporate network. In fact, a hacker can utilize sniffing tools to alert him when such an opportunity exists.
As a result, scan for these unauthorized base stations as part of the assessment. Most companies will be surprised to learn how many they find. The most effective method for detecting rogue base stations is to walk through the facilities with sniffing tools. In addition, the company should periodically scan the network for potential rogue base stations from the wired side of the network. This is available in many of the centralized wireless network management systems.
Perform Penetration Tests
In addition to hunting for rogue base stations, try going a step further and attempt to access corporate resources using common tools available to hackers. For example, can you utilize AirSnort to crack through WEP? Is it possible to associate with a base station from outside the company's controlled perimeter? Of course your job will be easy if WEP is turned off. If strong encryption and authentication techniques are in use, you'll likely not find a way in.
Analyze Security Gaps
The information you gather during the assessment provides a basis for understanding the security posture of a company or organization. After collecting information, spend some time thinking about potential gaps in security. This includes issues with policy, network architecture, operational support, and other items that weaken security, such as presence of unauthorized base stations and abilities to penetrate the network. This requires you to think like a hacker and uncover any and all methods that make it easier for someone to penetrate and access (or control) company resources through the wireless network.
Recommend Improvements
As you spot weaknesses, research and describe methods that will counter the issues. Start by recommending improvements to the policies, which dictate what the company requires in terms of security for the wireless networks. This provides a basis for defining technical and procedural solutions that strengthen the system's security to a level that protects the company's interests.
Common Security Policies
With any wireless network, consider policies that will protect resources from unauthorized people. Here's a look at what you should include.
Place Wireless Users Outside a Firewall
Consider implementing a wireless demilitarized zone (DMZ) by placing a firewall between the wireless network and the corporate network. (See Figure 8-8.) With this approach, equip each client device with a virtual private network (VPN) that the protected network will accept. As a result, a hacker would need to utilize a correctly configured VPN?which is difficult to do? to gain access to company resources.
Figure 8-8. Firewalls Offer Additional Security to Wireless Networks
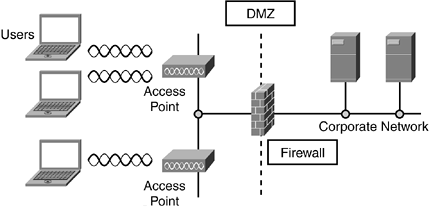
The problem with a VPN solution for all users is that it's difficult to manage and sometimes slows performance. As a result, mainly consider VPNs if users will roam into public areas.
Use Effective Encryption
Skilled hackers can crack into a WEP-protected network using freely available tools. However, WEP does a good job of protecting many home and business networks from the general public. To crack WEP, you need to know how to use complicated tools and capture a lot of network packets, something that most people won't bother with unless the network resources are extremely valuable and they have infinite patience. The use of standard 802.11 WEP for networks with low attack risk is a minimum for any security policy.
If your wireless network hardware supports a form of encryption (such as WPA) that changes keys often, use it. This offers a much more secure solution than using static methods such as WEP. If extremely high security is necessary, utilize superior standards, such as AES.
Ensure Firmware Is Up-to-Date
Vendors often implement patches to firmware in base stations and radio NICs that fix security issues. Start by upgrading the firmware in the base station soon after pulling it out of the box. Make it a habit to periodically check that all devices have the most recent firmware releases to cover up all known security holes. This is why it's a good idea to make certain you can easily upgrade the firmware in the base stations that you purchase.
Physically Secure Base Stations
Some base stations will revert to factory default settings, which do not provide any security, when someone pushes a reset. This makes the base station a fragile entry point. As a result, provide adequate physical security for the base station hardware.
For example, don't place a base station within easy reach on a table in the office. Instead, mount them out of view above ceiling tiles. Some base stations don't have reset buttons, but they allow you to reset through an RS-232 cable via a console connection. To prevent this, be sure to disable the console port.
Also, don't leave base stations within reach of a hacker who can replace a legitimate safeguarded base station with an unsecured, rogue base station that accepts access from any user. In fact, it's a good idea to conceal the base station as much as possible to make it more difficult for a hacker to find. Be sure, however, to note the location of the wireless hardware; otherwise, you'll have a difficult time finding them yourself.
Disable base stations during outage periods. If possible, shut down the base stations when users don't need them. This limits the window of opportunity. You could pull the power plug on each base station; however, consider deploying power-over-Ethernet equipment that provides this feature through centralized operational support tools.
Assign Strong Passwords to Base Stations
Don't use default passwords for base stations. Default passwords are well known, making it easy for someone to change configuration parameters on the base station to her advantage. Instead, use passwords that are difficult to guess. In fact, it's a good idea to use a mix of uppercase and lowercase letters, as well as special symbols. Be sure to alter these passwords periodically. Also, ensure that passwords are encrypted before being sent over the network.
Don't Broadcast SSIDs
If this feature is available, you can avoid having user devices automatically sniff the SSID being used by the wireless LAN access point. Windows XP and other monitoring tools will automatically sniff the 802.11 beacon frames to obtain the SSID. With SSID broadcasting turned off, the base station will not include the SSID in the beacon frame, making most sniffing tools useless. In addition, Windows and XP users will not see that the wireless LAN exists.
The disabling of SSIDs isn't foolproof, however, because someone can still monitor 802.11 association frames and recover the SSID. Shutting off the broadcast mechanism, however, will limit access.
Reduce Propagation of Radio Waves
Through the use of directional antennae, it's possible to confine the propagation of radio waves within an area where hackers are not able to physically access. For example, a wireless network design could specify antenna gain and orientation to reduce the spillage of radio waves outside the perimeter of the facility. This not only optimizes coverage, it also minimizes the ability for a snooper to eavesdrop on user signal transmissions or interface with the corporate network through an access point.
Implement Personal Firewalls
If a hacker is able to associate with a base station, the hacker can easily access files on other users' devices through the Windows operating system that are associated with an access point connected to the same wireless LAN. As a result, it's crucial that all users disable file sharing for all folders and utilize personal firewalls. This is crucial when users are operating in public locations.
Monitor Base Station Configuration
Utilize operational support tools to continually monitor the network and check for base stations that don't conform to configuration policies. A base station that doesn't match specific security settings has likely been reset or is possibly a rogue base station.
If base stations are found with improper settings, restore the settings as soon as possible. Be sure to encrypt management traffic, however, through the use of secure Simple Network Management Protocol (SNMP). SNMP Version 1, for example, sends everything in the clear. You can also deploy intrusion detection sensors, available in some operational support tools, to identify the presence of hackers based on invalid MAC addresses. The main idea is to provide alerts if suspicious behavior is occurring.
Control Deployments
Ensure that all employees and organizations within the company coordinate the installation of wireless networks with the appropriate IT group. For example, forbid the use of unauthorized access points. Mandate the use of approved vendor products after you've had a chance to verify appropriate security safeguards.
Maintain a list of authorized radio NIC and base station MAC addresses that you can use as the basis for identifying rogue base stations during surveys. In addition, deploy management tools that force base stations to comply with corporate security policies.
With these recommendations in mind, you have a basis for forming a solid security policy. When deciding on which techniques to implement, however, consider the actual security needs. For example, WEP might be good enough for home and small business wireless LANs. If you work for a financial institution or retail store transmitting sensitive data, concentrate on using something stronger, such as WPA or AES.






