Foundation Topics
Understanding IP Addresses
Although the BSCI exam might not ask direct questions about IP addressing, IP addressing is a central topic of the test. Scalability (the "S" in BSCI) in IP routing is found by summarization, and you must understand how to summarize using each routing protocol to be successful on this test.
This section also reviews binary numbering fundamentals by guiding you through the math behind turning the numbers we use in everyday life—decimal—into the numbers used by our computers—binary. This section also reviews calculating classfully assumed network ranges, reviews the concept of address classes (used to assume a mask in the early days of IP), and describes the modern classless approach of calculating network ranges using subnet masks.
Reviewing IP
IP version 4 (IPv4) uses 32-bit numbers that combine a network address and host address. IP addresses are written in four decimal fields separated by periods. Each number represents a byte. The far right bits are the network address because all hosts on this network have addresses that start with that pattern. The left bits are the host address because each host has a different value. A sample IP address might look like 192.168.1.5/24. In this example, the network portion of the address is 192.168.1 and the host portion is ".5."
Reviewing Binary Numbering Fundamentals
Binary numbering, or base two, uses 0 and 1 for counting, and each digit to the left represents an increasing power of two. By comparison, decimal numbers use ten symbols, with each digit to the left representing an increasing power of ten.
Note
A more complete description of binary and the conversion process may be found in the CCNA Exam Certification Guide.
Figure 2-1 shows an example of a decimal and a binary number.
Figure 2-1. Interpreting Decimal and Binary Numbers
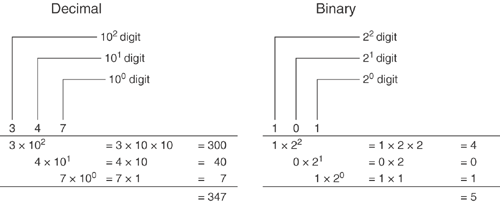
IP addresses are composed of four bytes—eight bits—and you will work with them one byte at a time. You only need to be able to convert binary and decimal numbers between 0000 0000 and 1111 1111 (0 to 255).
To convert a binary byte to decimal, the easiest method is to label each bit position with its decimal value. The far-right bit is 1, and the values double as you move to the left, as follows:
| 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
Then, take the binary value of the byte at each bit position and multiply the byte by the value. For instance, 0101 1010 could be interpreted in this way:
| Values: | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 | |||||||||
| Bits: | 0 | 1 | 0 | 1 | 1 | 0 | 1 | 0 | |||||||||
| = | 0 | + | 64 | + | 0 | + | 16 | + | 8 | + | 0 | + | 2 | + | 0 | = | 90 |
To convert a decimal number to binary, ask if the number is equal to or larger than the bit value at each position, starting from the left. If it is, write a 1 in that space and subtract the value from the number. An example for the number 137 is as follows:
| Values: 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
Is 137 equal to or greater than 128? Yes.
1
Subtract 128 from 137, leaving a remainder of 9. Is 9 equal to or greater than 64? No.
0
Is 9 equal to or greater than 32? No. 16? No. 8? Yes, 9 is greater than 8.
0 0 1
Because 9 - 8 = 1, is 1 equal to or greater than 4? 2? 1? Because 1 = 1, the last bit is 1.
0 0 1
So the decimal 137 is converted to binary as 1000 1001.
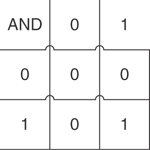
IP addressing uses a binary operation called AND. Figure 2-2 shows the truth table for AND. AND is only true if both inputs are true, so 0 AND 1 is 0, but 1 AND 1 is 1.
Figure 2-2. Truth Table for AND
Calculating Classfully Assumed Network Ranges
A common task in addressing is to take an IP address and to understand the range of addresses that are on the same network. Originally, this was done by reading the first bits of the address to determine a class; this is called classful addressing. The portion of the address consumed by the network prefix was then assumed, based on that class. Table 2-2 shows the first bits of an IP address, the corresponding classes, and the number of bytes assumed to be in the network portion of the address.
| First Bits of IP | Range of First Byte | Class | Network Bytes |
|---|---|---|---|
| 0 _ _ __ _ _ _ | 0–127 | A | 1 |
| 1 0 _ _ _ _ _ _ | 128–191 | B | 2 |
| 1 1 0 _ _ _ _ _ | 192–223 | C | 3 |
| 1 1 1 0 _ _ _ _ | 224–239 | D—Multicast | |
| 1 1 1 1 _ _ _ _ | 240–255 | E—Experimental | |
The address 192.168.1.5 starts with the byte 192. In binary, 192 is 1100 0000, so this is a Class C address. Since it is a Class C address, the network portion of the address is assumed to be 192.168.1 and all IP speakers in this network will have addresses that start with that prefix. However, the last octet will be unique for each of them.
The address 150.159.216.202 starts with the byte 150, which is 1010 0110 in binary. Based on the first two bits, this is a Class B address and the first two bytes establish the network prefix. All devices on this network will have an address that starts 150.159.
Classful addressing is not flexible enough to meet the needs of the modern network. Class C networks are too small for large organizations, and even large organizations do not need 65,000 addresses in one office (which they would have if the first two octets were the prefix).
Calculating Network Ranges Using Subnet Masks
Subnetting is the action of taking the assigned network and breaking it up into smaller pieces. Because the prefix length can no longer be classfully assumed just by looking at the address, the prefix length is now specified. For instance, an address might be written 172.20.1.5/23. This slash notation indicates that the first 23 bits are a routing prefix, and are common to all devices on a subnet. Another way of expressing the same address is to create a subnet mask where 1 shows the position of the network portion and 0 shows the host portion. In this example:
/23 =1111 1111.1111 1111.1111 1110.0000 0000 =255.255.254.0
Hosts use subnet masks to determine whether a destination is local or on a remote subnet. Consider a case where three computers need to communicate, as shown in Figure 2-3.
Figure 2-3. Example of Subnets
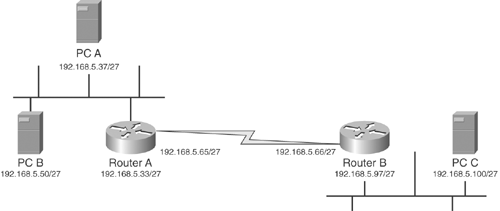
PC A needs to be able to compare its address with the addresses of the destination to determine if devices are local or remote. If a device is local, PC A will use ARP to determine its MAC address and then will transmit directly to it. If a device is remote, PC A will use ARP to get the MAC address of the default gateway and will transmit through that router.
To determine the topology, an IP device takes a bit-wise binary AND of its own address and subnet mask and compares it to an AND of the destination address. Since any devices that share a link will also share the same prefix, if both numbers are the same then they are both on the same network.
Remember the AND truth table shown in the "Reviewing Binary Numbering Fundamentals" section. In the case of PC A communicating with PC B, PC A starts by taking a bit-wise binary AND of its source address and its subnet mask. Remember that /27 means that the first 27 bits of the subnet mask are on, which translates to 255.255.255.224.
| PC A 192.168.5.37 | 11000000.10101000.00000101.00100101 |
| Mask 255.255.255.224 | 11111111.11111111.11111111.11100000 |
| Subnet 192.168.5.32 | 11000000.10101000.00000101.00100000 |
This shows that the network address of PC A is 192.168.5.32. Notice that the subnet mask "masks" the host portion of the address. Performing the same operation against PC B yields the same result, so PC A knows they are on the same network.
| PC B 192.168.5.50 | 11000000.10101000.00000101.00110010 |
| Mask 255.255.255.224 | 11111111.11111111.11111111.11100000 |
| Subnet 192.168.5.32 | 11000000.10101000.00000101.00100000 |
However, when PC A tries to communicate with PC C a different network number is determined. Because PC C is on the 192.168.5.96 network, PC A must pass traffic through its default gateway to reach this peer.
| PC C 192.168.5.100 | 11000000.10101000.00000101.01100100 |
| Mask 255.255.255.224 | 11111111.11111111.11111111.11100000 |
| Subnet 192.168.5.96 | 11000000.10101000.00000101.01100000 |
A common task in network support involves performing the same kind of operation. Imagine that you have to support the network that PC A and PC B reside on. If you need to add another PC, what IP address could be used for the new PC? The following procedure may be used to determine the range of addresses supported by a network.
Step 1. | If the mask is given in dotted decimal notation, convert it to CIDR notation. |
Step 2. | To determine the network address, copy the network bits from the address as shown by the CIDR notation. Fill in the remaining bits with zeros. |
Step 3. | The last address in the range is the broadcast address. Again, copy the network bits from the address and then fill in the remaining bits with ones. |
Step 4. | The usable set of addresses on this network falls between these two numbers. |
Step 5. | To check your math, subtract the CIDR notation from 32 to determine the number of host bits. There should be 2n-2 host addresses, where n is the number of host bits. |
As an example, consider PC C (192.168.5.100).
1. | The mask in CIDR notation is /27. |
2. | Step 2 says to "Copy the network bits from the address as shown by the CIDR notation. Fill in the remaining bits with zeros." The first three bytes (24 bits) are all within the /27 so those portions may be copied directly. The last octet is converted to binary and the first three bits are copied, while the remaining bits are changed to zeros. PC C 192.168.5.100 11000000.10101000.00000101.01100000 The result is a network address of 192.168.5.96. |
3. | To determine the broadcast address, copy the network bits and fill in the remaining bits with ones: PC C 192.168.5.100 11000000.10101000.00000101.01111111 The broadcast address is 192.168.5.127. |
4. | The usable set of addresses on this network falls between these two numbers (from 96 to 127), so addresses from 192.168.5.97 through 192.168.5.126 are usable. |
5. | To check ourselves, subtract 32–27 = 5. There are five host bits. There should be 25–2=30 hosts on this network, which matches what step four told us. |
Understanding Summarization
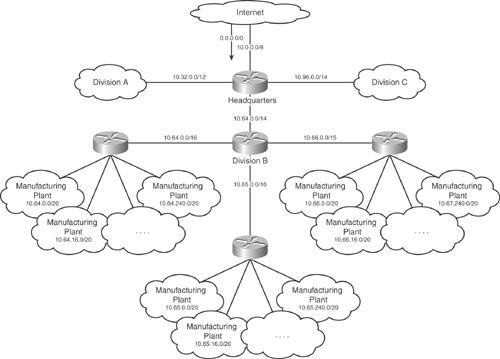
This section describes the process of summarization. Summarization is the technique of grouping IP networks together to minimize advertisements. For instance, imagine that a division's network consisted of the subnets 172.21.0.0/24 through 172.21.255.0/24. To advertise each network using a routing protocol, the division will send 256 advertisements to other divisions.
To extend the example, consider Figure 2-4. There are many routers in this company, but the three routers shown are the three that tie the divisions together. If each router announces every route in its division, there will be 768 advertisements!
Figure 2-4. Advertisements in a Fictional Company
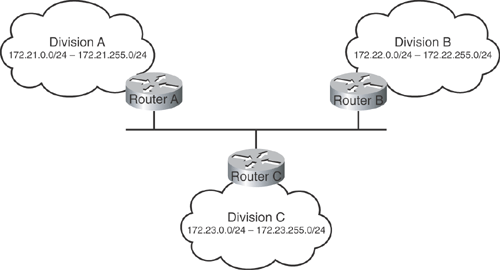
As an alternative, Router A could advertise 172.21.0.0/16. This would be equivalent to saying "all the addresses that start with the 16 bits 172.21 can be found behind Router A. Do not worry about the details—let Router A worry about how to forward your traffic within the division." This is the process of summarization—replacing a large set of individual advertisements with a smaller set that advertise the same range.
Summarization Advantages
Summarization hides details to simplify the routing process. One of the keys to scalable routing is to take large complicated sets of advertisements and reduce them as much as possible.
Summarization reduces router resource consumption (CPU and memory) required to store and process routes by reducing the number of routes. Summarization also saves network capacity, because fewer advertisements are required and each advertisement is smaller.
Summarization also hides unimportant details, such as flapping links. A flapping link is a network that goes up and down, sometimes several times per minute. In Figure 2-4, imagine that the 172.23.5.0/24 link interior to division C began to flap. In an unsummarized network, Router C has to advertise 172.23.5.0/24 every time the link comes up and withdraw it every time the link goes down. In a summarized network, Router C does not pass on this level of detail. Traffic to 172.23.5.0/24 will simply be dropped within the division if the network is down.
This might strike you as counter-intuitive, but IP devices are capable of recognizing when responses are not received. The inefficiency of allowing some traffic to pass and then be dropped is less than the inefficiency of re-advertising the route.
Convergence is sped up in a summarized network because each router has a smaller set of routes to consider, because each router can receive updates faster, and because each router has fewer routes to process.
Summarization Solutions
Subsequent chapters show techniques for summarizing routes for each of the routing protocols described in this book. However, it is important that you understand how to compose the summary address.
The method for determining the summary is
Step 1. | Write each network in binary. |
Step 2. | Determine the number of bits that match. This gives a single summary that includes all the routes, but may include a range of addresses that is too large (also called over-summarization). |
Step 3. | If step two unacceptably over-summarizes, start from the first address and add bits to the prefix until a portion of the range is summarized. Take the remaining addresses and start this process again. |
Suppose a network is composed of the links 172.16.0.0/24 through 172.16.3.0/24. Following the procedure:
Step 1. | Write each network in binary. 172.16.0.0 = 1010 1010.0001 0000.0000 0000.0000 0000 172.16.1.0 = 1010 1010.0001 0000.0000 0001.0000 0000 172.16.2.0 = 1010 1010.0001 0000.0000 0010.0000 0000 172.16.3.0 = 1010 1010.0001 0000.0000 0011.0000 0000 |
Step 2. | Determine the number of bits that match. 172.16.0.0 = 1010 1010.0001 0000.0000 0000.0000 0000 172.16.1.0 = 1010 1010.0001 0000.0000 0001.0000 0000 172.16.2.0 = 1010 1010.0001 0000.0000 0010.0000 0000 172.16.3.0 = 1010 1010.0001 0000.0000 0011.0000 0000 In this example, the first 22 bits match. A summary of 172.16.0.0/22 is a candidate, although we know that this may over-summarize. To determine if it over-summarizes, use the technique described in the "Calculating Network Ranges Using Subnet Masks" section to determine the range of addresses covered. In this case, you will find that 172.16.0.0/22 covers the exact same set of addresses as the combination of 172.16.0.0/24, 172.16.1.0/24, 172.16.2.0/ 24, and 172.16.3.0/24 |
Step 3. | Step 2 did not result in an over-summarization, so the process is complete. On the BSCI exam, you may see cases where a range of addresses can be summarized in a neat and tidy fashion, just like the previous example. In the real world, there will be times when you will need to go a step further. One more example will help you in those cases. Consider a case where the following networks need to be summarized:
|
Following the procedure:
Step 1. | Write each network in binary. |
Step 2. | Determine the number of bits that match. 192.168.0.0 = 1100 0000.1010 1000.0000 0000.0000 0000 192.168.1.0 = 1100 0000.1010 1000.0000 0001.0000 0000 192.168.2.0 = 1100 0000.1010 1000.0000 0010.0000 0000 192.168.3.0 = 1100 0000.1010 1000.0000 0011.0000 0000 192.168.4.0 = 1100 0000.1010 1000.0000 0100.0000 0000 192.168.5.0 = 1100 0000.1010 1000.0000 0101.0000 0000 192.168.6.0 = 1100 0000.1010 1000.0000 0110.0000 0000 192.168.7.0 = 1100 0000.1010 1000.0000 0111.0000 0000 192.168.8.0 = 1100 0000.1010 1000.0000 1000.0000 0000 192.168.9.0 = 1100 0000.1010 1000.0000 1001.0000 0000 The first 20 bits match. However, upon reflection, a summary of 192.168.0.0/20 covers the range from 192.168.0.0 to 192.168.15.255 and over-summarizes. |
Step 3. | Because step 2 over-summarized, add a bit to the prefix and consider 192.168.0.0/21. This summarizes 192.168.0.0 through 192.168.7.0. So that will be one advertisement. We take the remaining portion of addresses and start again. |
Step 4. | Write each network in binary. |
Step 5. | Determine the number of bits that match. 192.168.8.0 = 1100 0000.1010 1000.0000 1000.0000 0000 192.168.9.0 = 1100 0000.1010 1000.0000 1001.0000 0000 The first 23 bits match. A summary of 192.168.8.0/23 describes addresses from 192.168.8.0 to 192.168.9.255, which matches exactly the required address space. |
Step 6. | Because step 2 did not over-summarize, the process is complete. Two advertisements (192.168.0.0/21 and 192.168.8.0/23) will be required. |
This process results in advertising 192.168.0.0/21 and 192.168.8.0/23, which is better than the ten advertisements that would have been required.
Address Planning
Summarization is not possible as an after-thought. If network numbers are randomly assigned within an organization, it will be difficult or impossible to find ways to adequately summarize. When designing a network, it is extremely important that careful attention is paid to the requirements for summarization.
Figure 2-5 shows that an example corporation might have multiple levels of summarization—within plants, within manufacturing groups, at the divisional level, and to the Internet. In particular, notice that the Internet is being summarized back to the company as a default route.
Figure 2-5. An Example of Summarization