Encryption
Encryption alters the bits of each data packet to guard eavesdroppers from decoding data, such as credit card numbers. Before encryption the data is called plaintext, which is easy to decode by using sniffing tools. The encryption converts the plaintext into ciphertext, which someone can decode only through the use of a proper secret key.
Many encryption methods, such as the 802.11 Wired Equivalent Privacy (WEP), are symmetric?that is, the same key that does the encryption is also the one that performs the decryption. Figure 8-4 illustrates this process.
Figure 8-4. Symmetric Encryption Uses a Common Key
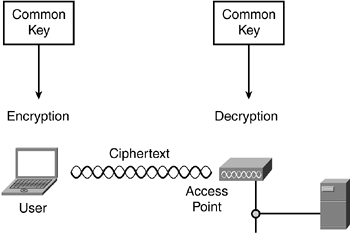
For example, the radio NIC uses key xyz to encrypt a data packet, and an access point uses key xyz to perform the decryption. This requires both the sending and receiving stations to trust each other, as is the case with a private wireless network application such as an enterprise wireless LAN. It's not practical to use symmetric keys in a public application, however, because anyone, including hackers, could obtain the key.
For symmetric encryption to be effective, the function must minimize the reuse of encryption keys by changing them often, possibly every frame transmission. This decreases the time available for a hacker to break into the network and makes it difficult?if not impossible?to compromise the security of the network. As a result, symmetric encryption mechanisms must have effective key distribution methods.
Public key cryptography uses asymmetric keys, with one that is private and another one that is public. As the name applies, the private key is secret; however, anyone can know the public key. This enables more effective encryption and authentication mechanisms because it simplifies key distribution.
An important requirement of public key encryption is that a set of public and private keys must match from a cryptographic standpoint. For example, the sending station can encrypt data using the public key, and the receiver uses the private key for decryption. The opposite is also true. The sending station can encrypt data using the private key, and the receiving station decrypts the data using the public key.
If the goal is to encrypt data, the sending station will use a public key to encrypt the data before transmission; this is shown in Figure 8-5. The receiving station uses the matching private key to decrypt the data upon reception. Each station keeps its private key hidden in order to avoid compromising encrypted information. As a result, the process allows any station to use a publicly known key to send encrypted data to any other station.
Figure 8-5. Public Key Encryption Enables All Senders of Encrypted Data to Use a Publicly Available Key

Public key cryptography works effectively for encrypting data because the public key can be made freely available to anyone wanting to send encrypted data to a particular station. A station that generates a new private key can distribute the corresponding public key over the network to everyone without worry of compromise. The public key can be posted on a website or sent unencrypted across the network.
WEP
WEP is 802.11's optional encryption and authentication standard implemented in the MAC Layer that most radio NIC and access point vendors support. When deploying a wireless network, you need to fully understand the ability of WEP to improve security.
WEP Operation
If a user activates WEP, the NIC encrypts the payload (frame body and cyclic redundancy check [CRC]) of each 802.11 frame before transmission using an RC4 stream cipher provided by RSA security. The receiving station, such as an access point or another radio NIC, performs decryption upon arrival of the frame. As a result, 802.11 WEP only encrypts data between 802.11 stations. Once the frame enters the wired side of the network, such as between access points, WEP no longer applies.
As part of the encryption process, WEP prepares a key schedule (seed) by linking the shared secret key supplied by the user of the sending station with a randomly generated 24-bit initialization vector (IV). The IV lengthens the life of the secret key because the station can change the IV for each frame transmission. WEP inputs the resulting seed into a pseudo-random number generator that produces a key stream equal to the length of the frame's payload plus a 32-bit integrity check value (ICV).
The ICV is a checksum that the receiving station recalculates and compares to the one sent by the sending station. It determines whether the transmitted data underwent any form of tampering while in transit. If the receiving station calculates an ICV that doesn't match the one found in the frame, the receiving station can reject the frame or flag the user.
WEP specifies a shared secret key to encrypt and decrypt the data. With WEP, the receiving station must use the same key for decryption. Each radio NIC and access point, therefore, must be manually configured with the same key.
Before transmission takes place, WEP combines the key stream with the payload/ICV through a bitwise XOR process, which produces ciphertext (encrypted data). WEP includes the IV in the clear (unencrypted) within the first few bytes of the frame body. The receiving station uses this IV along with the shared secret key supplied by the receiving station user to decrypt the payload portion of the frame body.
In most cases, the sending station will use a different IV for each frame (this is not required by the 802.11 standard). When transmitting messages having a common beginning, such as the sender's address in an e-mail, the beginning of each encrypted payload will be equivalent when using the same key. After encrypting the data, the beginnings of these frames would be the same, offering a pattern that can aid hackers in cracking the encryption algorithm. Since the IV is different for most frames, WEP guards against this type of attack. The frequent changing of IVs also improves the ability of WEP to safeguard against someone compromising the data.
WEP Issues
WEP is vulnerable because of relatively short IVs and keys that remain static. The issues with WEP don't really have much to do with the RC4 encryption algorithm. With only 24 bits, WEP eventually uses the same IV for different data packets. For a large, busy network, this reoccurrence of IVs can happen within an hour or so.
This results in the transmission of frames having key streams that are too similar. If a hacker collects enough frames based on the same IV, the individual can determine the shared values among them?that is, the key stream or the shared secret key. This, of course, leads to the hacker decrypting any of the 802.11 frames.
The static nature of the shared secret keys emphasizes this problem. 802.11 doesn't provide any functions that support the exchange of keys among stations. As a result, system administrators and users generally use the same keys for weeks, months, and even years. This gives mischievous culprits plenty of time to monitor and hack into WEP-enabled networks.
When to Use WEP
Despite its flaws, you should enable WEP as a minimum level of security. Many people have discovered wireless networks that use protocol analyzers, such as AiroPeek and AirMagnet. Most of these people are capable of detecting wireless networks where WEP is not in use and then use a laptop to gain access to resources located on the associated network.
By activating WEP, however, you significantly minimize this from happening, especially if you have a home or small business network. WEP does a good job of keeping most people out. Beware: There are true hackers around who can exploit the weaknesses of WEP and access WEP-enabled networks, especially those with high utilization.
Temporal Key Integrity Protocol
The 802.11i standard includes improvements to wireless LAN security. One of the upgrades is the Temporal Key Integrity Protocol (TKIP), initially referred to as WEP2. TKIP is an interim solution that fixes WEP's key reuse problem. In fact, many wireless LAN products already have TKIP as an option.
The TKIP process begins with a 128-bit temporal key shared among clients and access points. TKIP combines the temporal key with the client's MAC address and then adds a relatively large 16-octet IV to produce the key that will encrypt the data. This procedure ensures that each station uses different key streams to encrypt the data.
TKIP uses RC4 to perform the encryption, which is the same as WEP. A major difference from WEP, however, is that TKIP changes temporal keys every 10,000 packets. This provides a dynamic distribution method that significantly enhances the security of the network.
An advantage of using TKIP is that companies having existing WEP-based access points and radio NICs can upgrade to TKIP through relatively simple firmware patches. In addition, WEP-only equipment will still interoperate with TKIP-enabled devices using WEP. TKIP is a temporary solution, and most experts believe that stronger encryption is still needed.
In addition to the TKIP solution, the 802.11i standard includes the Advanced Encryption Standard (AES) protocol. AES offers much stronger encryption. AES uses the Rine Dale encryption algorithm, which is a tremendously strong encryption that replaces RC4. Most cryptographers feel that AES is uncrackable. In addition, the 802.11i standard will include AES as an option over TKIP. In fact, the U.S. Commerce Department's National Institutes of Standards and Technology (NIST) organization chose AES to replace the aging Data Encryption Standard (DES). AES is now a Federal Information Processing Standard, which defines a cryptographic algorithm for use by U.S. government organizations to protect sensitive but unclassified information. The Secretary of Commerce approved the adoption of AES as an official government standard in May 2002.
The problem with AES is that it requires more processing power than what most access points on the market today can support. As a result, the implementation of AES will require companies to upgrade their existing wireless LAN hardware to support the performance demands of AES. An issue, however, is that AES requires a coprocessor (additional hardware) to operate. This means that companies need to replace existing access points and client NICs to implement AES.
Wi-Fi Protected Access
The Wi-Fi Protocol Access (WPA) standard provided by the Wi-Fi Alliance provides an upgrade to WEP that offers dynamic key encryption and mutual authentication. Most wireless vendors now support WPA. WPA clients utilize different encryption keys that change periodically. This makes it more difficult to crack the encryption.
WPA 1.0 is actually a snapshot of the current version of 802.11i, which includes TKIP and 802.1x mechanisms. The combination of these two mechanisms provides dynamic key encryption and mutual authentication, something needed in wireless LANs. WPA 2.0 offers full compliance with the 802.11i standard.
Virtual Private Networks
If wireless users will be roaming into public areas, such as airports and hotels, strongly consider virtual private network (VPN) solutions. Even though VPNs are not foolproof, they provide an effective means of end-to-end encryption. VPNs are also effective when clients roam across different types of wireless networks because they operate above the dissimilar network connection levels.






