Traditional Security Architecture
The traditional approach for network security is to divide the network into two zones: trusted and untrusted. The trusted zone is the area under your physical control, where access is limited by the security guard at the front door (or by your family when at home). There is no need for network security protection within the trusted zone because there are no enemies present. You might have an account on your computer to prevent people from accessing your private files, but you assume that no one will mess with data going across the wires between computers.
By contrast, you regard the untrusted zone as full of enemies. Internet access or even dedicated wired links through the public network are untrusted. Where the untrusted network meets the trusted network, there is typically a firewall to prevent all the enemies getting in (see Figure 3.1). The firewall is the electronic equivalent of the security guard (Cheswick et al., 2003).
Figure 3.1. Conventional Security Architecture

Difficulties arise when trusted people find themselves in the untrusted zone and want to access their home network. When you are traveling and staying in a hotel, you need a safe way to get back to the trusted zone in your company. One solution is virtual private network (VPN) technology. VPN extends the trusted zone out into the untrusted area through a secure tunnel, as shown in Figure 3.2. Imagine one of the old diving machines in which a diver went down into the water wearing a metal suit and with an umbilical cord bringing down air. The secure tunnel is a bit like that umbilical cord.
Figure 3.2. Remote User in "Trusted Bubble"
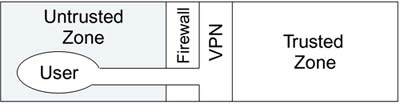
VPN uses a security protocol to form a connection, typically between a remote person and the home office. Helped by encryption, this connection is (theoretically) impenetrable to the enemies in the untrusted zone even though it passes right under their noses.
VPN can suffer from deployment issues. VPN software must be installed on the computer of the remote user, and it must be compatible with that of the VPN server. Because interoperability between vendors' products is not assured, you should consider buying the server and the client software from the same company. This type of VPN solution works at the Internet Protocol (IP) level and is not usually built in to network adapter cards such as Ethernet or Wi-Fi LAN PC cards. Also, because the implementation on the remote computer is usually in software, VPN may limit the speeds with which the computers can communicate (although for remote access the speed of the Internet is usually the limitation rather than the speed of the software). VPN is widely used in corporations for remote access and, in these applications, it is very effective (Norris and Pretty, 2000).
The important question is, "How does Wi-Fi LAN fit into this conventional security architecture?" Should it be deployed like the devices in the trusted zone?connected straight to the network? Or should it be placed behind the firewall? Life would be much easier if the answers to these questions were clear. In fact, a Wi-Fi LAN can be deployed either way. Placing wireless LANs outside the firewall means they must connect using VPN?a disadvantage. Connect directly to the network inside the firewall means you have to ensure that the wireless LAN is inherently secure. Although we briefly discuss the first option (via VPN), this book focuses on the second option. A direct connect is more common and it places bigger security demands on the technology. WPA and IEEE 802.11i address this option.
Option 1: Put Wireless LAN in the Untrusted Zone
In some situations the Wi-Fi LAN user is clearly in an untrusted zone. For example, some airports have installed Wi-Fi wireless LAN coverage in waiting areas or lounges (for more detail, see Chapter 14). If you subscribe to the service, you can connect to the Wi-Fi LAN and have direct high-speed Internet access while waiting for your flight. This is a clear example of working in an untrusted zone.
Now think about sitting at your desk in your office. Although you are in a trusted zone, your wireless signal may be going down the corridor and out the window. You have to assume that the signal can be picked up outside the building. Therefore, even though you are sitting at your desk, you are operating in an untrusted zone just like an airport. If you have no security on your Wi-Fi LAN and your access points are connected to your internal wired LAN, you have converted your entire building's network into an untrusted zone!
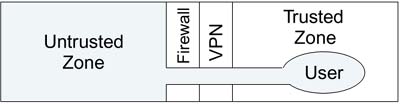
With the possible exception of national security headquarters, offices do not have perfect screening. You may decide, therefore, that Wi-Fi LANs are always operating in an untrusted zone regardless of where you are. In some sense you have created the situation shown in Figure 3.3, wherein the untrusted area extends inside your building.
Figure 3.3. Wireless User Is in Untrusted Zone
One response to this situation is to handle Wi-Fi LAN users in the same way that you handle remote users. Make them use VPN as if they were outside the building. Even though a person is sitting at her desk, all the communications from Wi-Fi LAN computers must be encrypted by VPN software before passing over the network. These communications then go to the wireless access point and on to an Ethernet connection that is outside the firewall. From there they go through the firewall and are decoded by the VPN server. Finally, the messages are placed on the trusted wired network and arrive at their destination, which might be the printer on the desk of a Wi-Fi LAN user. Figure 3.4 shows this design. There are several disadvantages with this approach:
VPN software on the laptop can sometimes be intrusive, slowing down communication and limiting the types of operations that can be performed.
The VPN server may have limited capacity. Often companies install servers that can handle 20 to 50 users. This is enough for remote users in the field connecting from time to time. However, if you have many internal Wi-Fi LAN users, you need a high-capacity VPN server.
The access points must be connected to the untrusted side of the firewall. They must have dedicated wiring and cannot share with the internal Ethernet system. If there are multiple access points, you probably need a dedicated patch panel to avoid the possibility that the access point wiring and the internal wiring are connected up by mistake.
Figure 3.4. Treating a Wi-Fi LAN User Like a Remote User
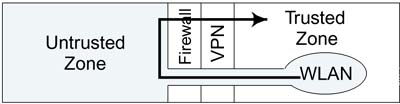
These disadvantages make this approach unattractive for many companies as well as impractical for small office and home users. Some companies have proceeded along these lines because they realized that the first generation of Wi-Fi was not sufficiently secure. Most would prefer the second approach, in which the Wi-Fi LAN becomes part of the trusted network, because it is simpler to administer.
Option 2: Make Wi-Fi LAN Trusted
The alternative to treating Wi-Fi LAN as a pariah that can never be trusted is to make the Wi-Fi LAN itself fundamentally impenetrable by enemies. Your goal is to make the LAN so secure that it can be regarded in the same way as physical wiring and treated as part of the trusted zone. Thinking along these lines led to the original security system of IEEE 802.11 being called "WEP," which stands for Wired Equivalent Privacy.
The idea runs something like this: It is very difficult, but not impossible, for an enemy to tap into a wired network in a building. There are various options, such as breaking into the building, bribing a security guard or employee, or using highly sensitive and directional radio receivers to pick up the slight emissions from the Ethernet cable connectors. The point is that it is not impossible to breach wired LAN security. So, the theory goes, you can make Wi-Fi LANs as trusted as wired LANs by making it very difficult to decode the wireless signals. You don't need to make it impossible to break the wireless security, just more difficult than breaking into the wired network because the enemy will always take the simplest route.
This principle that the enemy takes the path of least resistance is reasonable, but you cannot realistically compare the difficulty of bribing a security guard with the difficulty of breaking the Wi-Fi LAN security protocol. More modern thinking concludes that Wi-Fi LAN security must be evaluated on its own merits rather than by comparison to attacks on the wiring plant. The standard of security that has been set for the new generation of Wi-Fi and IEEE 802.11 is very high. It makes the signals look so random that any amount of monitoring by enemies does not provide useful information. It also prevents forgery, tampering, and other attack techniques. As a result, you can considering moving the Wi-Fi LAN back inside the trusted domain.
Once you believe that information being sent by wireless is completely inaccessible to attackers (perhaps more so than information on the wires), you can treat Wi-Fi LAN devices in the same way as regular LAN devices. The access points go right on to the regular internal LAN, and Wi-Fi LAN users who connect to them have the same rights as everybody else. Wi-Fi LAN can still be used in the untrusted zone, when people are passing through a hotel or airport, by employing VPN. WPA allows the old security model to be put back in place, making it much easier to integrate Wi-Fi into everyday networks. The same principle applies at home: you can treat Wi-Fi in the same way as you treat the Ethernet cables running across your floor. No one can get access to them but you.







