Relationship of the Standards
The next few chapters cover a bewildering number of standards, mostly those of IEEE 802 and IETF (RFCs). The following reference list of all the standards that we mention should help you keep track of these standards and serve as a roadmap to indicate if and where they fit into the RSN picture. You may find you want to refer back here as the picture starts to form in your mind.
List of Standards
Here is a list of all the standards mentioned in Chapters 8 through 12.
Name | Title or Description |
|---|---|
IEEE 802.1X | Port access control |
IEEE 802.3 | Wired LAN |
IEEE 802.11 | Wireless LAN |
IEEE 802.11e | Wireless LAN with Quality or Service Management (in development) |
IEEE 802.11i | Wireless LAN Security (in development) |
RFC 1321 | MD-5 Message Digest Algorithm |
RFC 1510 | Kerberos V5 |
RFC 1661 | Original PPP standard |
RFC 1964 | GSSAPI Kerberos Protocol Mechanism |
RFC 2058 | Earlier RADIUS spec. (superseded) |
RFC 2104 | Hash Message Authentication Code |
RFC 2138 | Earlier RADIUS spec. (superseded) |
RFC 2246 | Transport Layer Security (TLS) |
RFC 2284 | PPP Extensible Authentication Protocol (EAP) |
RFC 2548 | Microsoft Vendor Specific RADIUS Attributes |
RFC 2716 | PPP EAP TLS Authentication Protocol |
RFC 2743 | Generic Security Service Application Programming Interface |
RFC 2865 | RADIUS |
RFC 2866 | RADIUS Accounting |
RFC 2869 | EAP over RADIUS |
RFC 2945 | The SRP Authentication and Key Exchange System |
draft-ietf-pppext-rfc2284bis | Updates EAP |
draft-aboba-radius-rfc2869bis | Update to RFC2869 |
draft-josefsson-pppext-eap-tls-eap | PEAP |
draft-haverinen-pppext-eap-sim | GSM-SIM over EAP |
Cisco LEAP | Proprietary Vendor protocol for Wi-Fi Security |
RC4 | Encryption Cipher |
AES | Encryption Cipher |
Pictorial Map
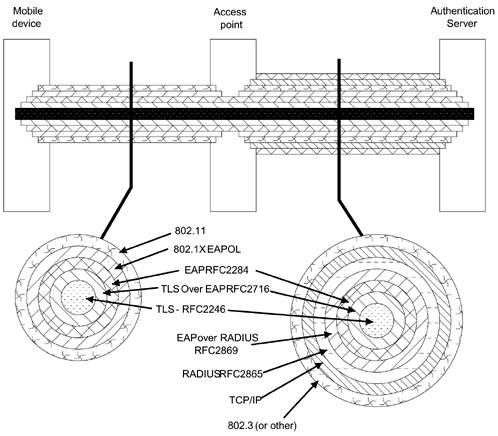
Figure 7.4 shows a pictorial map of the main standards used in an RSN solution based on TLS authentication. Inevitably the picture is a bit simplistic, but it shows how the TLS authentication process is buried inside a set of standards that provide the communications first between the mobile device and the access point and then between the access point and the authentication server. The links are shown as a set of concentric tubes; the outer tube is the communications medium and successive inner tubes are the encapsulations used to transport the information. As we said at the beginning of this section, we do not expect you to understand the whole picture from looking at Figure 7.4, but we hope it will form a reference point to which you can return.
Figure 7.4. Main Standards in an RSN Solution Based on TLS