Authentication in the Cellular Phone World: EAP-SIM
This last upper-layer authentication method reviewed in this chapter is interesting because it comes from a different industry from the others. The authentication methods that have built up around IETF and IEEE 802 have largely been associated with the data-processing industry. The model used in discussing and developing the solution revolves around the use of computers in education, industry, and the home. Over the years the ways in which computers are used have changed, and the models have been updated accordingly. However, it has always been against a backdrop of computer-based infrastructure.
New paradigms are now appearing. Over the next ten years, computer infrastructure will become important for home consumer electronics, and the computer industry, home entertainment industry, and the mobile phone industry will start to blur together. New types of cellular phones are being designed and deployed with digital communications capability. The cellular phone of the future will, in effect, be a small portable computer with capabilities exceeding laptops of today.
Up to now, the mobile phone networks and infrastructure have been quite separate from the Internet technologies used by the computer industry. But as phones turn into computers, all this has to change. If a phone looks like a mobile computer, it faces all the same issues of security found in a conventional computer. Furthermore, the new cellular phones will need to connect to the Internet and other computers and servers. Therefore, a way is needed to bridge the gap between the existing mobile phone infrastructure and the Internet infrastructure.
This change is relevant to wireless LANs and IEEE 802.11 because products are now being deployed that have both cellular phone data capability and an IEEE 802.11 wireless LAN capability built in. When you are within range of an access point, you can connect to the Internet using wireless LAN and, at other times, you can use the cellular data network, albeit at a lower data rate (for more information, see Chapter 14).
Each authentication method requires a way of storing secret information at the client end. In Kerberos, for example, it is assumed that users remember passwords. In TLS the client might need to have a certificate. For a large proportion of the world's cellular phones, the secret information is held in a smart card, often referred to as a SIM card. The SIM card is a small plastic chip with an embedded microprocessor. SIM cards are used in all GSM mobile phones around the world and in many PCS phones in the United States. The idea of the SIM card is that it contains all the information about your subscription for the phone service. It contains your phone number, your address book, and, importantly, your security codes. You can pick up any compatible cellular phone and insert your SIM card, and it will immediately have your information and start receiving your phone calls. The SIM card itself is a small plastic token, as shown in Figure 9.17.
Figure 9.17. SIM Card Next to a Quarter
The secret information in the SIM card is not known by the subscriber. It is known only by the cellular phone company. When you subscribe to the phone service, the phone company programs a unique SIM card for you and installs the secret onto it. It can then authenticate you as a subscriber and also encrypt the data going between your phone and the network. This scenario is similar to one in which a company installs client certificates on the computers of their employees so they can validate them for network access. When a mobile phone with Wi-Fi LAN capability wants to connect to an access point and authenticate to the network, it makes a lot of sense to leverage the secret stored in the SIM card. In fact, if you can link the authentication server back to the cellular phone billing system, you can provide subscriber access control as well as subscriber billing. Like it or not, this gives the phone company the ability to charge you for Wi-Fi LAN network access.
Overview of Authentication in a GSM Network
This section outlines how authentication is done in a conventional GSM network. This discussion also applies to many of the United States?based digital cellular networks that are based on GSM technology (although they may appear under a different name). The model was originally designed with voice communications in mind rather than data transfer, but it bears a striking similarity to the methods used for data security.
When a cellular phone comes within range of a base station and recognizes a compatible service, it may choose to try to register with the network?that is, to join the cell. Before the network allows the phone to connect, the phone must prove that it is a paid-up subscriber for the service. It needs to authenticate itself, and its identity needs to be verified with some subscriber database server in the network.
The basic approach to authentication is a challenge response method whereby the network sends a random value and the phone has to encrypt it[6] with its secret key and send it back for verification. In GSM three numbers are used during authentication and subsequent secure communications:
[6] Technically, the current algorithms are keyed hash functions rather than encryption functions. The SRES is only 4 bytes long so the algorithm cannot be a reversible encryption.
Random challenge: RAND
64-bit session key, which is used to encrypt the wireless communications: Kc
Response value called SRES that is computed by combining the secret key and the RAND value
Together, these three numbers are referred to as a triplet (RAND, SRES, Kc).
When a phone wants to register to a new network, it sends its identification number. This is stored in the SIM card and is called the International Mobile Subscriber Identity (IMSI) value. It is unique for each subscriber, rather like MAC addresses in the LAN network. The network can identify the home operator for the cellular phone from the IMSI and it requests the authentication center to create and forward a triplet for the authentication. This referral method allows phones to roam to different networks and still be authenticated by their home network provider.
When the local network receives the security triplet, it sends the RAND value to the phone, which passes it to the SIM card. Being a smart card, the SIM has it own microprocessor and is able to compute the other two components of the triplet using an encryption method and secret key hidden inside. The resulting value of SRES is returned to the network for confirmation and then the session opens using the Kc value for link encryption (see Figure 9.18 for an illustration of this process).
Figure 9.18. Authentication Overview for GSM Phone Connection
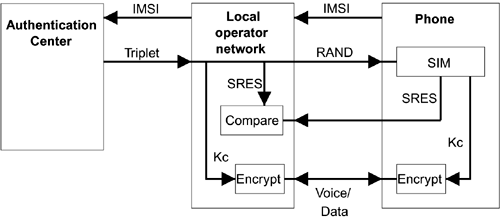
There are a couple of points worth noting. First, the network is not explicitly authenticated because it could accept any value of SRES without checking (although, if the network doesn't have a valid triplet, the encrypted communication would fail because Kc will not match between the network and the phone). Second, the algorithm used to generate SRES and Kc is not accessible outside the SIM card or to the network. When roaming, the network requests the authentication center associated with your home operator to provide a triplet; so the method used to generate SRES and Kc can be proprietary to the home network operator. The operator also issues the SIM card. Therefore, it is common for different network operators to use their own flavor of algorithm for security inside the SIM card?a sort of security by obscurity in addition to the usual protections.
Linking GSM Security to Wi-Fi LAN Security
Why would you want to link the existing GSM authentication system to Wi-Fi LAN operation? Well, as mentioned earlier, phones are becoming more like computers and users will want high-speed Internet access combined with mobility. One way to achieve this is to build IEEE 802.11 into a cellular phone and allow the phone to choose between available connections, using Wi-Fi LAN whenever available. In fact, at least one major cellular phone vendor has introduced a plug-in PC card for laptops that does precisely this. It has both IEEE 802.11 capability and GSM-GPRS cellular data capability. In an ideal scenario, the mobile phone operator deploys access points as well as cell phone base stations and the device can automatically switch to use the best infrastructure available. It follows that a single authentication and billing infrastructure is needed and, because a SIM card is available, it makes sense to use it also for the Wi-Fi LAN authentication.
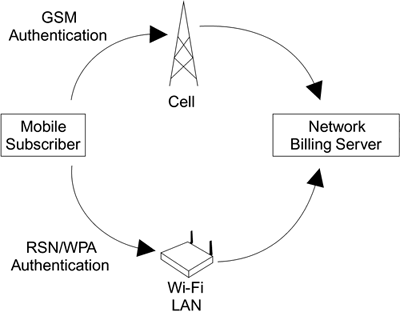
An example of handover is shown in Figure 9.19. When the subscriber is using the cell phone network, data goes to the local cellular base station and GSM authentication must be used. When the subscriber uses the Wi-Fi LAN, data goes to the access point and RSN authentication must be used. However, in both cases the authentication server must be the same.
Figure 9.19. Roaming Between Cellular and Wi-Fi LAN
EAP-SIM
At the time of writing, the proposal to use cellular phone SIM authentication is a draft in IETF: draft-haverinen-pppext-eap-sim-09.txt. Eventually, this draft may make the transition into an RFC. Essentially, the object of the method is to use the existing GSM style authentication unchanged so far as possible. Some things cannot be changed because they are built into the SIM card standard and method of operation.
One of the problems faced in converting cellular authentication to RSN is that the SIM card does not produce a very long master session key?only 64 bits. By today's standards, we need at least 128 bits for the master key. The SIM card produces the session key as part of its triplet containing the challenge and response information. To get a larger master key, multiple triplets are used. Instead of simply sending one challenge, the server can send two, or three, challenges during the EAP process. Each time a challenge arrives, the SIM card computes a corresponding triplet containing another 64-bit session key. By joining together the 64-bit triplet keys, a session key of arbitrary length can be created.
Another concern relates to the fact that the identity of the subscriber is visible in each authentication. The identity can be determined by observing the IMSI value, which is unique to the cellular phone. To avoid the access points gathering data about the subscriber from the IMSI value, the EAP-SIM draft introduces the idea of IMSI privacy. Remember the IMSI is the unique identity of the mobile device. If we can hide the identity, a degree of anonymity is possible. In addition, it is more difficult to mount an attack based on observing a large number of authentications; the attacker simply wouldn't know which authentication belongs to which device. Therefore the EAP-SIM draft has a scheme whereby, during authentication, the server and mobile device agree on a new subscriber identity to use for the next authentication. This is called a pseudonym. The new value is set using encryption so the identity changes every time the device connects and only the device and server know which identity will be used each time.
The third problem with GSM authentication is that the method does not explicitly authenticate the network. If a rogue server were to accept the challenge response without really checking, the mobile device would incorrectly think it has connected to a legitimate network. This problem is resolved by having the mobile device send a nonce value at the start of the negotiation. The server has to incorporate the nonce value into an encrypted response. To do this correctly, it has to have access to legitimate triplets.
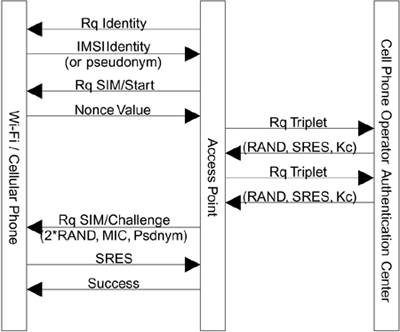
The actual message exchanges used for EAP-SIM authentication are shown in Figure 9.20 and described here:
It all starts with the usual EAP request-identity message. On the first operation the cellular phone sends its actual IMSI information. However, for all subsequent connects, it sends a pseudonym as agreed on with the server during the previous authentication. After this, the EAP-SIM specific messages start.
The server sends an EAP-Request/SIM/Start message telling the mobile that it is ready to proceed with authentication.
The mobile responds by sending its nonce value (this is a 16-byte unique value).
The server has several jobs to do at this stage:
Get Triplets: After the server receives the identity or pseudonym for the cellular phone, it asks the authentication center of the home operator to send several triplets; let's suppose two triplets are obtained. We write this as 2*(RAND, SRES, Kc) to indicate that each of the two triples has three pieces of information.
Compute Session Key: The server computes a 128-bit session key using the two (64-bit) Kc values. Rather than just concatenating the values as described earlier, it combines the two values with the mobile's nonce value using a hashing algorithm.
Protect the RAND values: The values of RAND form the challenge texts. The mobile device uses these to generate its own copies of the triplets using the SIM card. Therefore the RAND values must be sent to the mobile unencrypted and are vulnerable to tampering. To prevent this, an integrity check is computed across both values using the session key that has just been just derived
Compose new pseudonym: The server creates the pseudonym that the mobile should use next time it authenticates. This is then encrypted using the new session key.
Now the server is ready to respond to the mobile. It sends an EAP-Request/SIM/Challenge containing the two RAND values, the integrity check, and the encrypted new pseudonym.
Having received the two values of RAND, the mobile now submits each in turn to the SIM card and gets back the corresponding values of SRES and Kc. Assuming everything is legitimate, these will match those held at the network server. The mobile then computes the session key using its copy of the nonce and verifies the integrity check word sent by the server. It is also able to decrypt and store the new pseudonym.
Now the mobile sends back the values of SRES that the SIM card computed. This is the way in which the network can confirm that the mobile really has a valid SIM card. In the same way as the server did for RAND, the mobile computes an integrity check over the two values of SRES and sends this back with the response.
Assuming that the server is able to confirm a match with its copy of SRES and verify the integrity checkword, the authentication is now complete and an EAP-Success message is sent. The mobile and network have mutually authenticated and also generated a strong session key from which link layer keys can be derived.
Figure 9.20. Message Flow for GSM-SIM
Status of GSM-SIM Authentication
As previously mentioned, the EAP-SIM method was a draft at the time of writing. However, the bigger issue is whether the idea of authenticating Wi-Fi LAN by cellular phone methods will catch on. There are few such systems available. However, if terminals that combine cellular phone connectivity and Wi-Fi LAN capability become widespread, cellular phone operators may install access points all over the place and a combined authentication process with the strength of RSN would then be a real requirement. The issue of public Wi-Fi LAN access and its security implications are reviewed in Chapter 14.







