Other Tools of Interest
This section describes some other tools that can be used against your wireless network. The first tool is Airsnort, one of the original tools to implement the FMS attack against WEP. The second tool is Airjack, which implements wireless DoS attacks as well as establishes man-in-the-middle attacks.
Airsnort
Airsnort (http://airsnort.shmoo.com), compared to the bsdairtools described earlier in this chapter, is easy to use. It has an X-windows?based interface and an MS-Windows version in alpha testing, shown in Figure 16.14.
Figure 16.14. Airsnort Capture Window
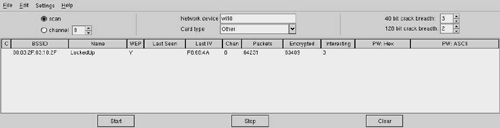
Figure 16.14 shows Airsnort running against our LockedUp network. Airsnort offers several features over the bsdairtools family that make the tool much easier to use. One of these features is the parallel cracking. The program is constantly working in the background to break the WEP key. When it does, it displays it in both hexidecimal and ASCII in the right columns (PW Hex and PW ASCII). Airsnort also allows you to capture on multiple networks or access points by scanning across the channels. This design causes you to miss packets sometimes, yet it remains a powerful feature.
Airsnort doesn't have the performance that bsdairtools has. In head-to-head tests we've run, bsdairtools seriously outperforms Airsnort. In one case, bsdairtools cracked the key in approximately 20 minutes, whereas Airsnort ran for six hours without recovering the key. The user forum for Airsnort located at http://airsnort.sourceforge.net indicates that others have had approximately the same performance from Airsnort.
Airjack
Airjack is a series of tools written by Abaddon. The tools were first described at the Black Hat Conference in 2002, and were available on the Internet for a short while at http://802.11ninja.net and run under the GNU/Linux operating system only. The tools provide an attacker with the ability to perform a DoS attack against an access point, actively determine the ESSID for a closed network, establish a man in the middle, and set the MAC address of the wireless card.
DoS Attack
The program wlan_jack continuously sends a Deauthentication message to the LAN broadcast address masquerading as an AP by using the same MAC address as the AP. This causes all of the stations/clients associated to that AP to drop their connections to the AP (disassociate); and because the attacker is continuously sending the Deauthentication message, the stations/clients can never associate to the AP for long, thereby creating a DoS attack (see Chapter 15).
ESSID Determination
The program essid_jack actively determines the ESSID for a closed network. Recall that some equipment uses the ESSID as a shared secret for access control (see Chapter 15). The ESSID can be determined passively by being patient and waiting until a station sends a Probe-Request message. If you're in a hurry, however, you can use essid_jack, which works similarly to wlan_jack in that it sends a forged Deauthentication message. It differs in that it only sends it to a single client, and then listens for the client to reassociate with the AP, during which step the ESSID is broadcast in the clear for essid_jack to sniff it and display it for you!
Man-in-the-Middle Attack
The program monkey_jack performs a man-in-the-middle attack against a station and a specific access point, as shown in Figure 15.6. However, we were unable to get the code to work by simply compiling it. In discussions with the author, he explained that the code is a proof of concept and that it does have several problems, such as a race condition, because the same card that knocks the target station off the AP (using a DoS) is also the card that is acting as the fake AP. Additionally, monkey_jack requires some changes to a wireless card driver that the author has not released.
While monkey_jack doesn't work as originally packaged, the author hobbled the code on purpose. The point of releasing the code, and of giving a talk at Black Hat 2002 (Abaddon, 2002), is to show that man-in-the-middle attacks can be accomplished, not to provide another tool to potential attackers.







