The Rationale for Tunnels in Routing Environments
Some tunnels are authenticated, some are compressed, and some are even encrypted; some lack all these capabilities and primarily support signaling, transport, and connectivity. The primary goal of the IPSec framework or suite of protocols is the provisioning and setup of authenticated and encrypted tunnels. It is a complex suite because it has to deal with complex tasks.
IPSec is an extension of IPv4 and intrinsically included in IPv6. Tunnels are virtual point-to-point overlay links that consist of only two endpoints; there is nothing in between, just plain nondeterministic best-effort IP delivery. Two endpoints need to be configured. With the exception of Multiprotocol Label Switching (MPLS), tunnels form the foundation of most VPNs.
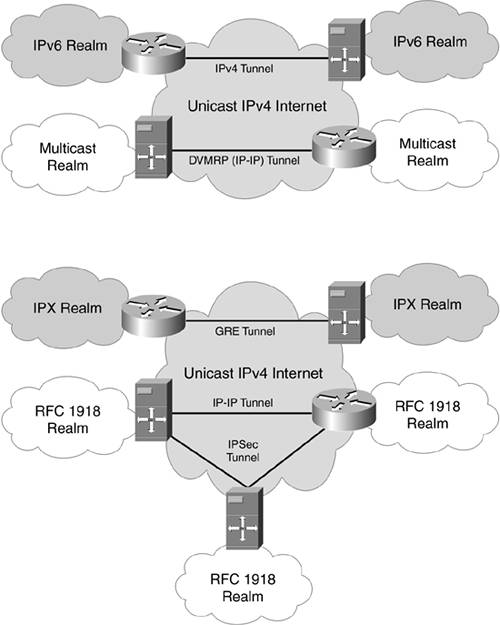
Virtual private dial-up networks (VPDNs) have different requirements to transport PPP connections securely over Digital Subscriber Line (DSL), Integrated Services Digital Network (ISDN), or Public Switched Telephone Network (PSTN) architectures. Figure 11-1 offers an overview of common tunnel scenarios.
Figure 11-1. Tunnel Applications