ARP-Related Tools
ARP is an important protocol both from a networking and a security point of view. From a practical point of view, it often becomes an issue when changing network adapters, dealing with HSRP/VRRP (Virtual Router Redundancy Protocol), and dealing with static NAT entries of firewalls. Modern ARP sniffers and spoofing utilities can cause havoc even in switched environments. Note that due to the lack of security within the ARP protocol, ARP replies are generally accepted without hesitation.
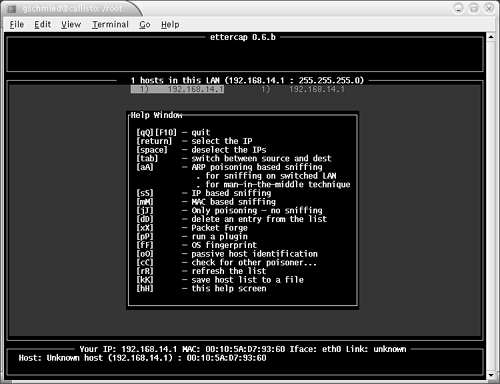
Among the most interesting tools are iptraf (see Figure 7-1) and ettercap (Figure 7-2). iptraf includes a LAN station (MAC) monitor, traffic statistics, and helpful statistics about protocol families (TCP/UDP/IP/ICMP) and packet sizes. ettercap is a versatile tool in switched and nonswitched environments. You can use it for ARP poisoning, man-in-the-middle attacks, OS fingerprinting, sniffing, and other tasks.
Figure 7-1. IPTraf MAC Accounting
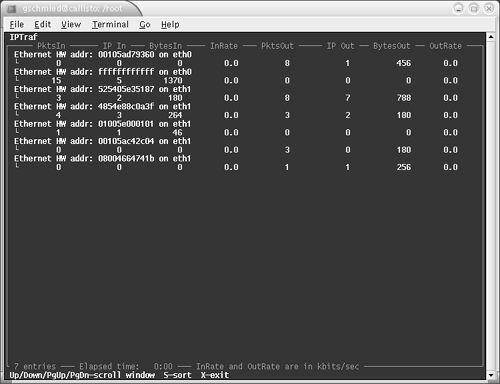
Figure 7-2. ettercap Toolbox
Other interesting standard command-line utilities are discussed in the following list and demonstrated in Example 7-19.
arpwatch/arpmonitor
arpoison
arpspoof (part of the dsniff package)
arping
arp-sk
For details, consult the man pages. Example 7-19 presents the arping tool, which combines the well-known ping behavior with ARP information. arp-sk is a flexible and versatile tool to dig deep into ARP statistics and ARP simulation. Finally, arpwatch and arpmonitor turn your workstation into a monitoring station for ARP traffic.
Example 7-19. Some Examples of ARP Monitoring
[root@callisto:~#] arping Usage: arping [-fqbDUAV] [-c count] [-w timeout] [-I device] [-s source] destination -f : quit on first reply -q : be quiet -b : keep broadcasting, don't go unicast -D : duplicate address detection mode -U : Unsolicited ARP mode, update your neighbours -A : ARP answer mode, update your neighbours -V : print version and exit -c count : how many packets to send -w timeout : how long to wait for a reply -I device : which ethernet device to use (eth0) -s source : source ip address destination : ask for what ip address [root@callisto:~#] arping -I eth1 192.168.1.254 ARPING 192.168.1.254 from 192.168.1.1 eth1 Unicast reply from 192.168.1.254 [48:54:E8:8C:0A:3F] 0.941ms Unicast reply from 192.168.1.254 [48:54:E8:8C:0A:3F] 0.871ms Unicast reply from 192.168.1.254 [48:54:E8:8C:0A:3F] 0.882ms Unicast reply from 192.168.1.254 [48:54:E8:8C:0A:3F] 0.889ms Unicast reply from 192.168.1.254 [48:54:E8:8C:0A:3F] 0.877ms Sent 5 probes (1 broadcast(s)) Received 5 response(s) [root@callisto:~#] arp-sk arp-sk version 0.0.15 (Sun Dec 1 18:35:24 CET 2002) Author: Frederic Raynal <pappy@security-labs.org> Usage: arp-sk -w --who-has send a ARP Who-has -r --reply send a ARP Reply -p --arping (bad) RARP emulation (NOT YET IMPLEMANTED) -m --arpmim Man in the Middle (NOT YET IMPLEMANTED) -d --dst dst in link layer (<hotname | hostip | MAC>) -s --src dst in link layer (<hotname | hostip | MAC>) --rand-hwa set random addresses in link header --rand-hwa-dst set random dst in link header --rand-hwa-src set random src in link header -D --arp-dst dst in ARP message ([hostname | hostip][:MAC]) -S --arp-src dst in ARP message ([hostname | hostip][:MAC]) --rand-arp set random addresses in ARP message --rand-arp-dst set random dst addresses in ARP message --rand-arp-src set random src addresses in ARP message --rand-arp-hwa-dst set random dst MAC address in ARP message --rand-arp-log-dst set random dst IP address in ARP message --rand-arp-hwa-src set random src MAC address in ARP message --rand-arp-log-src set random src IP address in ARP message -i --interface specify interface (eth0) -c --count # of packets to send (infinity) -t --time wait the specified number of seconds between sending \ each packet (or X micro seconds with -t uX) --rand-time randomize the sending period of the packets --beep beeps for each packet sent -a --addr-spaces addresses to use in the ARP packet (eth/ip) -n --network broadcast address to use for icmp-timestamp --use-ts an icmp-timestamp is sent to resolve MAC to IP -N --call-dns force address resolution in outputs (default is off) -V --version print version and exit -h --help this help :) [root@callisto:~#] arp-sk -i eth1 192.168.1.254 - Warning: no mode given, using default. + Running mode "reply" + Ifname: eth1 + Source MAC: 52:54:05:e3:51:87 + Source ARP MAC: 52:54:05:e3:51:87 + Source ARP IP : 192.168.1.1 + Target MAC: ff:ff:ff:ff:ff:ff + Target ARP MAC: ff:ff:ff:ff:ff:ff + Target ARP IP : 255.255.255.255 --- Start classical sending --- TS: 18:48:45.447550 To: ff:ff:ff:ff:ff:ff From: 52:54:05:e3:51:87 0x0806 ARP For 255.255.255.255 (ff:ff:ff:ff:ff:ff): 192.168.1.1 is at 52:54:05:e3:51:87 TS: 18:48:50.445497 To: ff:ff:ff:ff:ff:ff From: 52:54:05:e3:51:87 0x0806 ARP For 255.255.255.255 (ff:ff:ff:ff:ff:ff): 192.168.1.1 is at 52:54:05:e3:51:87 --- 255.255.255.255 (ff:ff:ff:ff:ff:ff) statistic --- To: ff:ff:ff:ff:ff:ff From: 52:54:05:e3:51:87 0x0806 ARP For 255.255.255.255 (ff:ff:ff:ff:ff:ff): 192.168.1.1 is at 52:54:05:e3:51:87 Total time: 10 sec [root@callisto:~#] arpwatch -? Version 2.1a11 usage: arpwatch [-dN] [-f datafile] [-i interface] [-n net[/width]] [-r file] ###### arpwatch running in debug mode without detaching from terminal ###### [root@callisto:~#] arpwatch -i eth1 -d From: arpwatch (Arpwatch) To: root Subject: new station (callisto) hostname: callisto ip address: 192.168.1.1 ethernet address: 52:54:5:e3:51:87 ethernet vendor: <unknown> timestamp: Saturday, January 31, 2004 19:02:40 +0100 [root@callisto:~#] arpmonitor -i ???? Usage mode: ./arpmonitor -i <interface> -s|e -p -i <interface> , interface to check -s or -e , output: <s>yslog or std<e>rr - default: syslog -p setup promisc mode (auto clean on ctrl-C) - default: no promisc mode [root@callisto:~#] arpmonitor -i eth1 -e eth1ArpMonitor: Initializing... ArpMonitor: HW address: 52:54:05:E3:51:87 ArpMonitor: IP address: 192.168.1.1 ArpMonitor: Netmask : 255.255.255.0 ArpMonitor: Broadcast : 192.168.1.255 ArpMonitor: received SIGINT, giving up







