Worker Process Identification
Security isn't only about authentication and authorization; it's also about the stability of your server because, in general, some form of instability tends to suggest a potential weak point in the server.
The new execution structure of IIS is whether Worker Process Isolation mode or IIS 5 Compatibility create a secure environment because the individual processes that actually service the Web applications can be so finely controlled, including enabling them to be recycled manually or automatically.
In both isolation modes, we can also secure individual application pools by assigning them a specific user account under which to execute. IIS 6 has updated and extended the available options, so it's worth covering the entire range now available:
ASPNET? A local user account specifically designed to be used with the ASP.NET worker process (aspnet_wp.exe) application only when the server is running in IIS 5 isolation mode.
Local System? Default user configured for all IIS and Indexing Service users. Worker processes configured with this user have access to the entire system (and should therefore be avoided).
Local Service? A limited privilege account granting access to the local system only. You should use this only when applications do not need access to other servers within a networked application.
Network Service? Provides a higher level service than that provided by the Local Service, including the ability to log on as a server and to communicate with other servers. This is the default account for worker processes in worker process isolation mode.
IUSR_ComputerName? The guest account used by anonymous users accessing an Internet Web site. If disabled, anonymous access to the site is disabled.
IWAM_ComputerName? The guest account used with Web applications. If disabled, this account blocks out of process applications when operating in IIS 5 Isolation mode.
The IIS_WPG group is granted the minimum rights required to start a worker process.
Table 3.2 summarizes the main rights for each user.
User Right | ASPNET | Local Service | Network System | IUSR | IWAM | IIS_WPG |
|---|---|---|---|---|---|---|
Access computer from the network | X | X | X | X | X | X |
Adjust memory quota for a process | X | X | X | |||
Allow log on locally | X | |||||
Bypass traverse checking | X | X | X | X | ||
Generate Security Audit | X | X | ||||
Impersonate a client after authentication | X | X | ||||
Log on as a batch job | X | X | X | X | X | |
Log on as a service | X | X | ||||
Deny Log on through terminal services | X | |||||
Replace a process-level token | X | X | X | |||
Deny log on locally | X |
CGI APPLICATIONS
If you create a new user to be used with application pools for the purposes of running CGI applications, the user must have been granted the Replace a Process Level Token and Adjust Memory Quotas for a Process rights. You can do this through the Local Security policy manager.
User Management
Users are configured either through the local account mechanism or, if you are within Active Directory, through the AD Users and Groups manager. However, if you want to restrict access, it can be more secure to create local users (which therefore don't automatically have access to AD resources and the rest of the domain) on a local basis.
When you have a new user, you can grant him access to the various facilities within IIS by using the Local Security Policy Manager to set specific rights. Just go to Local Policies, User Rights Assignment.
If you are using domain accounts, use the Group Policy editor and create a new policy within Computer Configuration, Security Settings, Local Policies. You can then apply the group policy to your IIS servers OU accordingly.
Setting Identity in Worker Process Isolation Mode
When working in worker process application mode, you can change the identity of an application pool using the following steps:
Right click on the application pool.
Select Properties from the popup menu.
Select the Identity tab (see Figure 3.8).
Figure 3.8. Setting worker process identity.
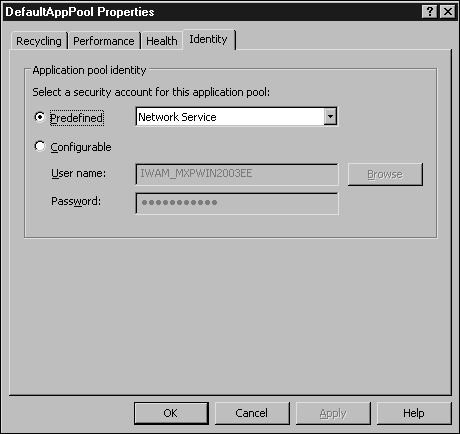
Choose a predefined identity or click the Configurable radio button and enter the username and password for the user you want to use.
Click OK
Setting Identity in IIS 5 Isolation Mode
IIS 5 Isolation mode can also set a user to be used for pooled applications using the following steps:
Open the Component Services tool from the Administrative Tools folder in the Start menu.
Expand the Component Services node, the My Computer node, and the COM+ Applications node.
Right-click the IIS Out-of-Process Pooled Applications entry and select Properties.
You will be presented with a window similar to the one shown in Figure 3.9. Here you can choose one of the System accounts or a specific user by entering the user's ID and password.
Figure 3.9. Setting application identity in IIS 5 Isolation mode.
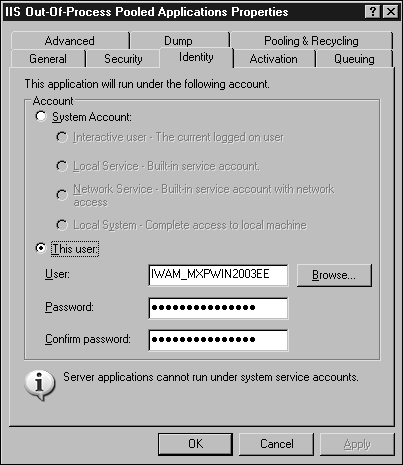
Click OK.







