Lesson 3: Using Event Viewer
Lesson 3:?Using Event Viewer
You use Event Viewer to perform a variety of tasks, including viewing the audit logs that are generated as a result of setting the audit policy and auditing events. You can also use Event Viewer to view the contents of security log files and find specific events within log files.
After this lesson, you will be able to
- View a log
- Locate events in a log
- Filter events in a log
- Archive security logs
- Configure the size of audit logs
Estimated lesson time: 50 minutes
Understanding Windows XP Professional Logs
You use Event Viewer to view information contained in Windows XP Professional logs. By default, Event Viewer has three logs available to view, as described in Table 12.4.
Table 12.4??Logs Maintained by Windows XP Professional
Viewing Security Logs
The security log contains information about events that are monitored by an audit policy, such as failed and successful logon attempts. You can view the security log by performing the following steps:
- Click Start, click Control Panel, click Performance And Maintenance, click Administrative Tools, and then double-click Event Viewer.
- In the console tree, click Security.
In the details pane, Event Viewer displays a list of log entries and summary information for each item, as shown in Figure 12.5.
 Figure 12.5??Event Viewer displaying a sample security log
Figure 12.5??Event Viewer displaying a sample security logSuccessful events are marked with a key icon and unsuccessful events are marked with a lock icon. Other important information includes the date and time that the event occurred, the category of the event, and the user who generated the event.
The category indicates the type of event, such as object access, account management, directory service access, or logon events.
- To view additional information for any event, select the event, and then on the Action menu, click Properties.
Windows XP Professional records events in the security log on the computer on which the event occurred. You can view these events from any computer as long as you have administrative privileges for the computer where the events occurred. To view the security log on a remote computer, open the MMC console and point Event Viewer to a remote computer.
Locating Events
When you first start Event Viewer, it automatically displays all events that are recorded in the selected log. To change what appears in the log, you can locate selected events using the Filter command. You can also search for specific events using the Find command.
To filter or find events, start Event Viewer, and then on the View menu click Filter or click Find. The options provided by Filter and Find are almost identical. Figure 12.6 shows the options available in the Filter tab.
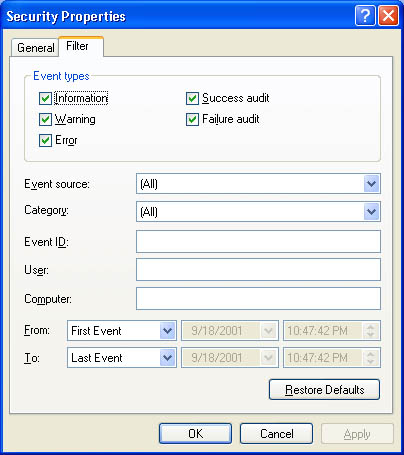
Table 12.5 describes the options for using the Filter tab to filter events and the Find command to find events.
Table 12.5??Options for Filtering and Finding Events
| Option | Description |
|---|---|
Event Types |
The types of events to view. |
Event Source |
The software or component driver that logged the event. |
Category |
The type of event, such as a logon or logoff attempt or a system event. |
Event ID |
An event number to identify the event. This number helps product support representatives track events. |
User |
A user logon name. |
Computer |
A computer name. |
From and To |
The date ranges for which to view events (Filter tab only). |
Restore Defaults |
Clears any changes in this tab and restores all defaults. |
Description |
The text that is in the description of the event (Find dialog box only). |
Search Direction |
The direction (up or down) in which to search the log (Find dialog box only). |
Find Next |
Finds and displays the next occurrence defined by the Find Settings. |
Managing Audit Logs
You can track trends in Windows XP Professional by archiving event logs and comparing logs from different periods. Viewing trends helps you determine resource use and plan for growth. You can also use logs to determine if a pattern of unauthorized resource use is a concern. Windows XP Professional allows you to control the size of the logs and to specify the action that it takes when a log becomes full.
You can configure the properties of each individual audit log. To configure the settings for logs, select the log in Event Viewer, and then on the Action menu, click Properties to display the Properties dialog box for the log.
Use the Properties dialog box for each type of audit log to control the following:
- The maximum size of each log, which can be from 64 KB to 4,194,240 KB (4 GB). The default size is 512 KB.
- The action that Windows XP Professional takes when the log fills up. To control this action, click one of the options described in Table 12.6.
Table 12.6??Options for Handling Full Audit Log Files
| Option | Description |
|---|---|
Overwrite Events As Needed |
You might lose information if the log becomes full before you archive it. However, this setting requires no maintenance. |
Overwrite Events Older Than X Days |
You might lose information if the log becomes full before you archive it, but Windows XP Professional will only lose information that is at least x days old. Enter the number of days for this option. The default is 7 days. |
Do Not Overwrite Events |
This option requires you to clear the log manually. When the log becomes full, Windows XP Professional will stop, but no security log entries will be overwritten. |
Archiving Logs
Archiving security logs allows you to maintain a history of security-related events. Many companies have policies on keeping archive logs for a specified period to track security-related information over time.
If you want to archive, clear, or view an archived log, select the log you want to configure in Event Viewer, click the Action menu, and then click one of the options described in Table 12.7.
Table 12.7?? Options to Archive, Clear, or View a Log File
| To | Do this |
|---|---|
Archive the log |
Click Save Log File As and then type a filename. |
Clear the log |
Click Clear All Events to clear the log. Windows XP Professional creates a security log entry stating that the log was cleared. |
View an archived log |
Click New Log View; add another view of the selected log. |

Practice:?Auditing Resources and Events
In this practice, you'll plan an audit policy for your computer. Then you'll set up an audit policy by enabling auditing on certain events. You'll also set up auditing of a file and a printer. Then you'll view the security log file and configure Event Viewer to overwrite events when the log file is filled.
Exercise 1: Planning an Audit Policy
In this exercise, you plan an audit policy for your computer. You need to determine the following:
- Which types of events to audit
- Whether to audit the success or failure of an event, or both
Use the following criteria to make your decisions:
- Record unsuccessful attempts to gain access to the computer.
- Record unauthorized access to the files that make up the customer database.
- For billing purposes, track color printer use.
- Track whenever someone tries to tamper with the computer's hardware.
- Keep a record of actions that an administrator performs to track unauthorized changes.
- Track backup procedures to prevent data theft.
- Track unauthorized access to sensitive Active Directory objects.
Record your decisions to audit successful events, failed events, or both for the actions listed in the following table:
| Action to audit | Successful | Failed |
|---|---|---|
Account Logon Events |
|
|
Account Management |
|
|
Directory Service Access |
|
|
Logon Events |
|
|
Object Access |
|
|
Policy Change |
|
|
Privilege Use |
|
|
Process Tracking |
|
|
System Events |
|
|
Exercise 2: Setting Up an Audit Policy
In this exercise, you open the MMC console, add the Group Policy snap-in pointing to the local machine, and then enable auditing for selected events.
To set up an audit policy
- Log on as Fred or with an account that is a member of the Administrators group.
- Click Start, click Run, and in the Open text box, type mmc and then click OK.
- In the Console 1 window, on the File menu, click Add/Remove Snap-In.
- In the Add/Remove Snap-In dialog box, click Add.
- In the Add Standalone Snap-In dialog box, select Group Policy and then click Add.
- In the Select Group Policy Object dialog box, ensure that the Group Policy Object text box says Local Computer, and then click Finish.
- In the Add Standalone Snap-In dialog box, click Close.
In the Add/Remove Snap-In dialog box, notice that it says Local Computer Policy, even though you added Group Policy. Group Policy for the local computer is referred to as Local Computer Policy.
- In the Add/Remove Snap-In dialog box, click OK.
- In the console tree of the Local Computer Policy snap-in, double-click Local Computer Policy.
- Double-click Computer Configuration, and then double-click Windows Settings.
- Double-click Security Settings, and then double-click Local Policies.
- Click Audit Policy.
The console displays the current audit policy settings in the details pane of the Local Computer Policy window.
- To set the audit policy, in the details pane, double-click each type of event, and then select either the Audit Successful Attempts check box or the Audit Failed Attempts check box, as listed in the following table:
- Close the MMC console and save the Local Group Policy.
- Restart your computer to make the changes take effect immediately.
Exercise 3: Setting Up Auditing of Files
In this exercise, you set up auditing for a file.
To set up auditing of files
- Log on as Fred or with an account that is a member of the Administrators group.
- In Windows Explorer, create a folder named Audit in the root folder of your system disk (for example, C:\Audit).
- Create a text file named AUDIT in the Audit folder (for example, C:\Audit\Audit).
- Right-click the AUDIT file and then click Properties.
- In the Properties dialog box, click the Security tab, and then click Advanced.
- In the Access Control Settings dialog box, click the Auditing tab.
- Click Add.
- In the Select User Or Group dialog box, in the Name text box, type Everyone and click OK.
- In the Audit Entry For Audit.txt dialog box, select the Successful check box and the Failed check box for each of the following events:
- Create Files/Write Data
- Delete
- Change Permissions
- Take Ownership
- Click OK.
Windows XP Professional displays the Everyone group in the Advanced Security Settings For dialog box.
- Click OK to apply your changes.
Leave the Audit Properties dialog box open for the next procedure.
To verify file permissions
- In the Audit Properties dialog box, click Users (PRO1\Users) and verify that the Allow permissions for the file are Read & Execute and Read.
- Click OK to close the Properties dialog box, and then close Windows Explorer.
Exercise 4: Setting Up Auditing of a Printer
In this exercise, you set up auditing of a printer.
To set up auditing of a printer
- Click Start, click Control Panel, click Printers And Other Hardware, and click Printers And Faxes.
- In the Printers window, right-click HP Color LaserJet 4500 PS and then click Properties. (Any installed printer will do. The procedure for installing a printer is covered in Chapter 6, "Setting Up, Configuring, and Troubleshooting Common Setup and Configuration Problems for Network Printers.")
- Click the Security tab, and then click Advanced.
- In the Advanced Security Settings For HP Color LaserJet 4500 PS dialog box, click the Auditing tab and then click Add.
- In the Select User Or Group dialog box, in the Name text box type Everyone and then click OK.
- In the Auditing Entry For HP Color LaserJet 4500 PS dialog box, select the Successful check box for all types of access.
- Click OK.
Windows XP Professional displays the Everyone group in the Access Control Settings For HP Color LaserJet 4500 PS dialog box.
- Click OK to apply your changes.
- Click OK to close the HP Color LaserJet 4500 PS Properties dialog box.
- Close the Printers And Faxes window.
Exercise 5: Testing the Auditing Policy Set Up on the AUDIT File
In this exercise, you attempt to access and modify the AUDIT file to create entries in the security log for your computer.
To test the auditing policy
- Click Start, click Control Panel, and then click User Accounts.
- Verify that User2 exists and is a Limited account.
- Create a password of User2 for the User2 user account.
- Close all open windows and log off the computer.
- Log on to the computer as User2 with a password of User2.
- Open Windows Explorer and then open the file C:\Audit\Audit.
Notepad opens and displays the blank file AUDIT.
- Type in the following text: User2 has modified this file.
- Save the file.
Were you able to save the file? Why or why not?
- Close the file without saving it and log off as User2.
Exercise 6: Viewing the Security Log
In this exercise, you view the security log for your computer, and then you use Event Viewer to filter events and to search for potential security breaches.
To view and filter the security log for your computer
- Log on to your computer as Fred or with a user account that is a member of the Administrators group.
- Click Start, click Control Panel, click Performance And Maintenance, click Administrative Tools, and then double-click the Event Viewer shortcut.
- In the console tree, click the application log and view the contents. As you scroll through the logs, double-click a couple of events to view a description.
- In the console tree, click the system log and view the contents. As you scroll through the logs, double-click a couple of events to view a description.
- In the console tree, click the security log and view the contents. As you scroll through the logs, double-click each of the Failure Audit events until you can locate the one for User2 trying to access C:\Audit\Audit.
- Click Filter on the View menu.
- In the Security Properties dialog box, in the User text box, type User2 and then click OK.
Filtering reduces the number of events that you have to search through.
- Double-click each of the events and notice that all of them have to do with User2.
Exercise 7: Managing the Security Log
In this exercise, you configure Event Viewer to overwrite events when the log file gets full. Then you clear the security log and view an archived security log.
To control the size and contents of a log file
- In the console tree, click System.
- On the Action menu, click Properties.
- In the System Properties dialog box, click Overwrite Events As Needed.
- In the Maximum Log Size box, change the maximum log size to 2048 (KB) and then click OK.
Windows XP Professional now allows the log to grow to 2048 KB and will then overwrite older events with new events as necessary.
- Close Event Viewer, and then close Administrative Tools.

Lesson Review
The following questions will help you determine whether you have learned enough to move on to the next lesson. If you have difficulty answering these questions, review the material in this lesson before beginning the next chapter. The answers are in Appendix A, "Questions and Answers."
- What are the three Windows XP Professional logs you can view with Event Viewer and what is the purpose of each log?
- How can you view the security log on a remote computer?
- The two ways that Event Viewer provides for locating specific events are the _____________ command and the _____________ command. What does each of the commands allow you to do?
- The size of each log can be from ____ KB to ____ GB, and the default size is ____ KB.
- If you select the Do Not Overwrite Events option, what happens when the log becomes full?
Lesson Summary
- Windows XP Professional has the following three logs by default: the application log, the security log, and the system log.
- You use Event Viewer to view the contents of the Windows XP Professional logs.
- You can use the Filter and Find commands in Event Viewer to easily locate specific events or types of events.
- You can view the security log on a remote computer by opening the MMC console and pointing Event Viewer to the remote computer.
- You can manage the Windows XP logs by archiving them to allow you to track trends over time and by controlling the size of the log files.







