Lesson 2: Assigning NTFS Permissions and Special Permissions
Lesson 2:?Assigning NTFS Permissions and Special Permissions
You should follow certain guidelines for assigning NTFS permissions. Assign permissions according to group and user needs, which include allowing or preventing permissions to be inherited from parent folders to subfolders and files that are contained in the parent folder.
After this lesson, you will be able to
- Assign NTFS folder and file permissions to user accounts and groups
- Give users the ability to change permissions on files or folders
- Give users the ability to take ownership of files and folders
Estimated lesson time: 70 minutes
Planning NTFS Permissions
If you take the time to plan your NTFS permissions and follow a few guidelines, you will find that they are easy to manage. Use the following guidelines when you assign NTFS permissions:
- To simplify administration, group files into application, data, and home folders. Centralize home and public folders on a volume that is separate from applications and the operating system. Doing so provides the following benefits:
- You assign permissions only to folders, not to individual files.
- Backup is less complex because you don't need to back up application files, and all home and public folders are in one location.
- Allow users only the level of access that they require. If a user only needs to read a file, assign the Read permission to his or her user account for the file. This reduces the possibility of users accidentally modifying or deleting important documents and application files.
- Create groups according to the access that the group members require for resources, and then assign the appropriate permissions to the group. Assign permissions to individual user accounts only when necessary.
- When you assign permissions for working with data or application folders, assign the Read & Execute permission to the Users group and the Administrators group. This prevents application files from being accidentally deleted or damaged by users or viruses.
- When you assign permissions for public data folders, assign the Read & Execute permission and the Write permission to the Users group and the Full Control permission to the CREATOR OWNER. By default, the user who creates a file is also the owner of the file. The owner of a file can grant another user permission to take ownership of the file. The person who takes ownership would then become the owner of the file. If you assign the Read & Execute permission and the Write permission to the Users group and the Full Control permission to the CREATOR OWNER, users have the ability to read and modify documents that other users create and the ability to read, modify, and delete the files and folders that they create.
- Deny permissions only when it is essential to deny specific access to a specific user account or group.
- Encourage users to assign permissions to the files and folders that they create and educate them about how to do so.
Setting NTFS Permissions
By default, when you format a volume with NTFS, the Full Control permission is assigned to the Everyone group. This presented a problem in earlier versions of Windows, including Microsoft Windows 2000. In Windows XP Professional, the Anonymous Logon is no longer included in the Everyone group.
Assigning or Modifying Permissions
Administrators, users with the Full Control permission, and the owners of files and folders can assign permissions to user accounts and groups.
To assign or modify NTFS permissions for a file or a folder, in the Security tab of the Properties dialog box for the file or folder, configure the options that are shown in Figure 8.3 and described in Table 8.3.
Table 8.3??Security Tab Options
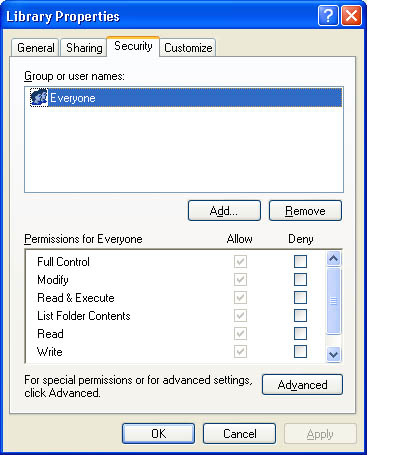
Adding Users or Groups
Click Add to display the Select Users Or Groups dialog box (see Figure 8.4). Use this dialog box to add users or groups so that you can assign them permissions for accessing a folder or file. The options available in the Select Users Or Groups dialog box are described in Table 8.4.
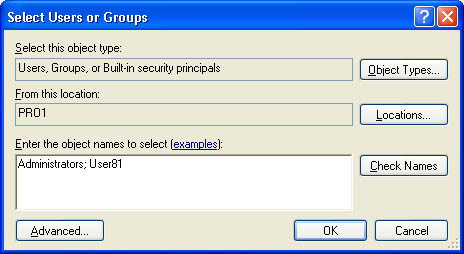
Table 8.4??Select Users Or Groups Dialog Box Options
| Option | Description |
|---|---|
Select The Object Type |
Allows you to select the types of objects you want to look for, such as built-in security principals (users, groups, and computer accounts), user accounts, or groups. |
From This Location |
Indicates where you are currently looking, for example in the domain or on the local computer. |
Locations |
Allows you to select where you want to look, for example in the domain or on the local computer. |
Enter The Object Names To Select |
Allows you to type in a list of built-in security principals, users, or groups to be added. |
Check Names |
Verifies the selected list of built-in security principals, users, or groups to be added. |
Advanced |
Allows you access to advanced search features, including the ability to search for deleted accounts, accounts with passwords that do not expire, and accounts that have not logged on for a certain number of days. |
Granting or Denying Special Permissions
Click Advanced to display the Advanced Security Settings dialog box (Figure 8.5), which lists the users and groups and the permissions they have on this object. The Permissions Entries box also shows where the permissions were inherited from and where they are applied.
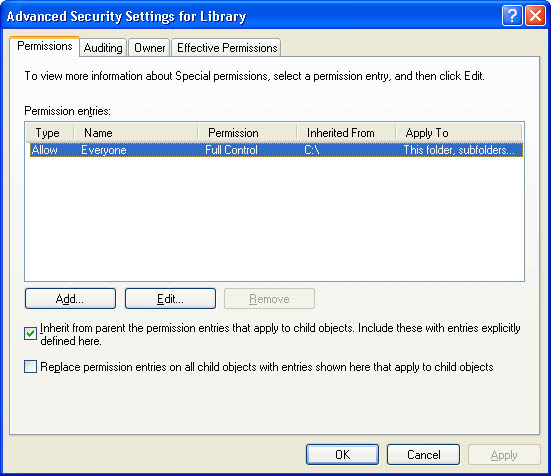
You can use the Advanced Security Settings dialog box to change the permissions set for a user or group. To change the permissions set for a user or group, select a user and click Edit to display the Permission Entry For dialog box (see Figure 8.6). You can then select or clear the specific permissions, explained in Table 8.5, that you want to change.

Table 8.5??Special Permissions
| Permission | Description |
|---|---|
Full Control |
Full Control applies all permissions to the user or group. |
Traverse Folder/ Execute File |
Traverse Folder allows or denies moving through folders to access other files or folders, even when the user has no permissions for the traversed folder (the folder that the user is moving through). Traverse Folder is not applied if the user or group has the Bypass Traverse Checking user right granted in Group Policy. By default the Everyone group has Bypass Traverse Checking granted, so you must modify the Group Policy if you want to use Traverse Folder permission. Traverse Folder applies only to folders. Execute File allows or denies running executable files (application files). Execute File applies only to files. |
List Folder/ Read Data |
List Folder allows or denies viewing file names and subfolder names within the folder. List Folder applies only to folders. |
|
Read Data allows or denies viewing the contents of a file. Read Data applies only to files. |
Read Attributes |
Read Attributes allows or denies the viewing of the attributes of a file or folder. These attributes are defined by NTFS. |
Read Extended Attributes |
Read Extended Attributes allows or denies the viewing of extended attributes of a file or a folder. These attributes are defined by programs. |
Create Files/ Write Data |
Create Files allows or denies the creation of files within a folder. Create Files applies to folders only. |
|
Write Data allows or denies the making of changes to a file and the overwriting of existing content. Write Data applies to files only. |
Create Folders/ Append Data |
Create Folders allows or denies the creation of folders within the folder. Create Folders applies only to folders. |
|
Append Data allows or denies making changes to the end of the file, but not changing, deleting, or overwriting existing data. Append Data applies to files only. |
Write Attributes |
Write Attributes allows or denies the changing of the attributes of a file or folder. These attributes are defined by NTFS. |
Write Extended |
Write Extended Attributes allows or denies the changing of the Attributes extended attributes of a file or a folder. These attributes are defined by programs. |
Delete Subfolders and Files |
Delete Subfolders and Files allows or denies the deletion of subfolders or files within a folder, even if the Delete permission has not been granted on the particular subfolder or file. |
Delete |
Delete allows or denies the deletion of a file or folder. A user can delete a file or folder even without having the Delete permission granted on that file or folder, if the Delete Subfolder and Files permission has been granted to the user on the parent folder. |
Read Permissions |
Read Permissions allows or denies the reading of the permissions assigned to the file or folder. |
Change Permissions |
Change Permissions allows or denies the changing of the permissions assigned to the file or folder. You can give other administrators and users the ability to change permissions for a file or folder without giving them the Full Control permission over the file or folder. In this way, the administrator or user can't delete or write to the file or folder but can assign permissions to the file or folder. |
Take Ownership |
Take Ownership allows or denies taking ownership of the file or folder. The owner of a file can always change permissions on a file or folder, regardless of the permissions set to protect the file or folder. |
Synchronize |
Synchronize allows or denies different threads to wait on the handle for the file or folder and synchronize with another thread that may signal it. This permission applies only to multithreaded, multiprocess programs. |
Taking Ownership
You can transfer ownership of files and folders from one user account or group to another. You can give someone the ability to take ownership and, as an administrator, you can take ownership of a file or folder.
The following rules apply for taking ownership of a file or folder:
- The current owner or any user with Full Control permission can assign the Full Control standard permission or the Take Ownership special access permission to another user account or group, allowing the user account or any member of the group to take ownership.
- An administrator can take ownership of a folder or file, regardless of assigned permissions. If an administrator takes ownership, the Administrators group becomes the owner and any member of the Administrators group can change the permissions for the file or folder and assign the Take Ownership permission to another user account or group.
For example, if an employee leaves the company, an administrator can take ownership of the employee's files and assign the Take Ownership permission to another employee, and then that employee can take ownership of the former employee's files.
To take ownership of a file or folder, the user or a group member with Take Ownership permission must explicitly take ownership of the file or folder, as follows:
- In the Security tab of the Properties dialog box for the file or folder, click Advanced.
- In the Advanced Security Settings dialog box, in the Owner tab, in the Change Owner To list, select your name.
- Select the Replace Owner On Subcontainers And Objects check box to take ownership of all subfolders and files that are contained within the folder, and then click OK.
Preventing Permissions Inheritance
By default, subfolders and files inherit permissions that you assign to their parent folder. This is indicated in the Advanced Security Settings dialog box (Figure 8.5) when the Inherit From Parent The Permission Entries That Apply To Child Objects check box is selected. To prevent a subfolder or file from inheriting permissions from a parent folder, clear the check box. You are then prompted to select one of the options described in Table 8.6.
Table 8.6??Preventing Permissions Inheritance Options
| Option | Description |
|---|---|
Copy |
Copy the permission entries that were previously applied from the parent to the child and then deny subsequent permissions inheritance from the parent folder. |
Remove |
Remove the permission entries that were previously applied from the parent to the child and retain only the permissions that you explicitly assign here. |
Cancel |
Cancel the dialog box. |

Practice:?Planning and Assigning NTFS Permissions
In this practice, you will plan NTFS permissions for folders and files based on a business scenario. Then you will apply NTFS permissions for folders and files on your computer running Windows XP Professional in a workgroup environment, based on a second scenario. Finally, you will test the NTFS permissions that you set up to make sure that they are working properly.
Before beginning the exercises that follow, log on with an account that is a member of the Administrators group and create the users listed in the following table:
Create the following folders:
- C:\Public
- C:\Public\Library

Run the PlanningNTFSPermissions file in the Demos folder on the CD-ROM accompanying this book for a demonstration of determining the default NTFS permissions applied to a folder. The demonstration also includes stopping a group from inheriting permissions from its parent object, deleting a group that has been assigned NTFS permissions, and adding a user and applying NTFS permissions to the user object for a folder.
Exercise 1: Determining the Default NTFS Permissions for a Folder
In this exercise, you determine the default NTFS permissions for the newly created Public folder located on a computer running Windows XP Professional in a workgroup environment.
To determine the default permissions on a folder
- Log on as Fred or with a user account that is a member of the Administrators group.
- Right-click My Computer, and then click Explore.
- Expand Local Disk (C:), right-click the Public folder, and then click Properties.
Windows XP Professional displays the Public Properties dialog box with the General tab active.
- Click the Security tab to display the permissions for the Public folder.If you do not have a Security tab, there are two things to check: Is your partition formatted as NTFS or FAT? Only NTFS partitions use NTFS permissions, so only NTFS partitions have a Security tab. Are you using Simple File Sharing? Click Cancel to close the Public Properties dialog box. On the Tools menu, click Folder Options. In the Folder Options dialog box, click View. Under Advanced Settings, clear the Use Simple File Sharing (Recommended) check box and click OK. Repeat steps 3 and 4 and continue with this practice.
If any of the users or groups have special permissions, click the user or group and then click Advanced to see which special permissions are set.
Windows XP Professional displays the Public Properties dialog box with the Security tab active.
What are the existing folder permissions?
- Click OK to close the Public Properties dialog box.
- Close Windows Explorer and log off.
To test the folder permissions for the Public folder
- Log on as User81, and then start Windows Explorer.
- Expand the Public folder.
- In the Public folder, create a text document named USER81 and type in the following text: The first four letters in the alphabet are a, b, c, and d.With the Public folder selected in the folder tree (the left pane), on the File menu, click New and then click Text Document to create the text document.
Were you successful? Why or why not?
- Attempt to perform the following tasks for the file that you just created:
- Open the file
- Modify the file
- Delete the file
Which tasks were you able to complete and why?
- In the Public folder, recreate the text file named User81.
- Log off Windows XP Professional.
- Log on as User82.
- Attempt to perform the following tasks on the USER81 text document.
- Open the file
- Modify the file
- Delete the file
Which tasks were you able to perform and why?
Exercise 2: Assigning NTFS Permissions
In this exercise, you assign NTFS permissions for the Public folder.
The permissions that you assign are to be based on the following criteria:
- All users should be able to read documents and files in the Public folder.
- All users should be able to create documents in the Public folder.
- All users should be able to modify the contents, properties, and permissions of the documents that they create in the Public folder.
- User82 is responsible for maintaining the Public folder and should be able to modify and delete all files in the Public folder.
Based on what you learned in Exercise 1, what changes in permission assignments do you need to make to meet each of these four criteria? Why?
You are currently logged on as User82. Can you change the permissions assigned to User82 while logged on as User82? Why or why not?
To assign NTFS permissions for a folder
- Log on as Fred or with a user account that is a member of the Administrators group, and then start Windows Explorer.
- Expand the Public folder.
- Right-click the Public folder and then click Properties.
Windows XP Professional displays the Properties dialog box for the folder with the General tab active.
- In the Properties dialog box for the folder, click the Security tab.
- In the Security tab, click Add.
The Select Users Or Groups dialog box is displayed.
- In the Enter The Object Names To Select text box, type User82 and then click Check Names.
PRO1\User82 should now appear in the Enter The Object Names To Select text box, indicating that Windows XP Professional located User82 on PRO1 and it is a valid user account.
- Click OK to close the Select Users Or Groups dialog box.
User82 now appears in the Group Or User Name box in the Public Properties dialog box.
What permissions are assigned to User82?
- Click Advanced.
Windows XP Professional displays the Advanced Security Settings For Public dialog box with User82 (PRO1\User82) listed in the Permissions Entries text box.
- Ensure User82 is selected and click Edit.
Windows XP Professional displays the Permission Entry For Public dialog box with User82 (PRO1\User82) displayed in the Name text box.
- In the Allow column, click Full Control.
All the check boxes under Allow are now selected.
- Click OK to close the Permission Entry For Public dialog box.
Windows XP Professional displays the Advanced Security Settings For Public dialog box.
- Click OK to close the Advanced Security Settings For Public dialog box.
- Click OK to close the Public Properties dialog box.
- Close Explorer and log off Windows XP Professional.
To test NTFS permissions for a folder
- Log on as User82 and type password when prompted for the password.
- Start Windows Explorer.
- Expand Local Disk (C:) and then expand the Public folder.
- Attempt to perform the following tasks on the USER81 text document:
- Modify the file
- Delete the file
Which tasks were you able to record and why?
- Close Windows Explorer and then log off Windows XP Professional.
Exercise 3: Testing NTFS Permissions
In this exercise, you create a file in a subfolder and test how NTFS permissions are inherited through a folder hierarchy.
To test permissions for the Library folder
- Log on as User81, and then start Windows Explorer.
- In Windows Explorer, expand the Public\Library folder.
- Create a text document USER81 in the Library folder.
- Log off Windows XP Professional.
To test permissions for the Library folder while logged on as User82
- Log on as User82, and then start Windows Explorer.
- Expand the Public\Library folder.
- Attempt to perform the following tasks on USER81:
- Open the file
- Modify the file
- Delete the file
Which tasks were you able to record and why?
- Log off Windows XP Professional.

Lesson Review
The following questions will help you determine whether you have learned enough to move on to the next lesson. If you have difficulty answering these questions, review the material in this lesson before beginning the next lesson. The answers are in Appendix A, "Questions and Answers."
- By default, when you format a volume with NTFS, the ______________________ permission is assigned to the Everyone group.
- When you assign permissions for public data folders, it is recommended that you assign the ______________________ permission and the ____________________ permission to the Users group and the ______________________ permission to the CREATOR OWNER user.
- Which of the following users can assign permissions to user accounts and groups? (Choose all answers that are correct.)
- Administrators
- Power users
- Users with the Full Control permission
- Owners of files and folders
- Which of the following tabs in the Properties dialog box for the file or folder do you use to assign or modify NTFS permissions for a file or a folder?
- Advanced
- Permissions
- Security
- General
- What is the purpose of the Traverse Folder/Execute File special permission?
- What is the difference between the Delete permission and Delete Subfolder and Files permission?
Lesson Summary
- By default, when you format a volume with NTFS, the Full Control permission is assigned to the Everyone group.
- To assign or modify NTFS permissions for a file or a folder, you use the Security tab of the Properties dialog box for the file or folder.
- By default, subfolders and files inherit permissions that you assign to their parent folder.
- To stop subfolders and files from inheriting permissions that you assign to their parent folder, clear the Inherit From Parent The Permission Entries That Apply To Child Objects check box in the Advanced Security Settings dialog box.
- The current owner or any user with Full Control permission can assign the Full Control standard permission or the Take Ownership special access permission to another user account or group, allowing the user account or a member of the group to take ownership.
- You cannot assign anyone ownership of a file or folder.







