Chapter 1: Introduction to MVPN
Chapter 1: Introduction to MVPN
Overview
Contracting margins and revenues per user, cost-based competition, and focus on customer retention rather than acquisitions are all signs that mobile telephony is not likely to show significant revenue growth— comparable to that enjoyed over the past decade—over the next several years. Service providers are therefore forced to look for innovative ways to invest in new technologies, which can potentially become the next growth enablers. For instance, in recent years much attention has been paid to "mobile Internet" services, which are believed to pose a significant revenue-generation potential for service providers.
This belief was in part responsible for the massive investment in spectrum for next-generation radio access technologies, with the potential to support higher data rates for mobile Internet services, commonly known as third generation (3G). More recently, service providers have recognized that Internet access per se may not justify the significant investments they made. As a result, the search is back on for innovative ways to generate revenues by using the new service capabilities offered by the deployment of packet-data-based systems such as General Packet Radio Service (GPRS), Universal Mobile Telecommunication System (UMTS), or CDMA2000 (CDMA stands for Code Division Multiple Access). So far, it is apparent that the most promising kind of services mix traditional mobile voice capabilities and new location-based and messaging services. Such systems must provide users personalized and predictable access to private networks where they can belong to communities of interest for both business and leisure, such as corporate networks or instant messaging groups.
The value of such networks to the customers appears to be strictly related to:
-
Ensuring secure network access with predictable performance
-
Making sure that access to such networks is exclusive to members with appropriate permissions.
These service requirements are compelling service providers to use Mobile Virtual Private Networking (MVPN), which we define as the emulation of private secure mobile data networks over generally insecure shared mobile and wireless facilities. This definition is based on a number of assumptions:
-
Data user mobility is defined as uninterrupted connectivity or the ability to stay connected and communicate to a possibly remote data network while changing the network access medium or points of attachment.
-
Despite MVPN service is usually provided over wireless media, and in fact, this book is written about VPN implementation over various wireless access systems. We make clear distinction between "mobile" and "wireless," since these terms have different meanings and we believe that for our purposes "mobile" is more accurate and inclusive (see Chapter 5 for more discussion on wireless versus mobile).
-
The term "wireless facilities" refers to current and future generations of cellular systems of interest such as Global System for Mobile Communications (GSM), CDMA2000, Time Division Multiple Access (TDMA), and UMTS, wireless networks such as Wireless LANs (WLANs), and overlay wireless packet data systems such as GPRS.
A simple visualization of MVPN can be found in Figure 1.1, which shows secure tunnels connecting a mobile device with a variety of private networks over multiple shared public networks, such as the Internet and an arbitrary cellular wireless system or WLAN network.
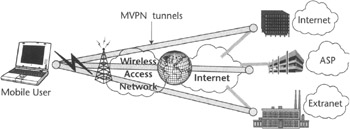 Figure 1.1: Example of Mobile Virtual Private Networking.
Figure 1.1: Example of Mobile Virtual Private Networking.
In this chapter we concentrate on business and standardization issues as an introduction to topics addressed in the rest of the book. The first half of this chapter discusses the MVPN business case and marketplace, explaining what benefits this technology can bring to service providers and their customers. We start with the discussion of pervasive mobility and its consequences, moving on to MVPN history and business case. The section ends with an overview of MVPN market segments and stakeholders. The second half of the chapter examines the current wireless data standardization status and trends and provides the reader with a reference to the standard documents usage and retrieval from various standard body repositories. The reader will become familiar with standards organizations such as 3GPP, 3GPP2, and the Internet Engineering Task Force (IETF), along with their standardization processes. An understanding of what a given standard body does within the landscape of mobile networking will be helpful to the reader for the remainder of the book.







