MVPN Gateways
MVPN Gateways
MVPN gateways are the cornerstones of MVPNs. As opposed to MVPN clients, whose function is to satisfy the VPN connectivity needs of a single mobile host, MVPN gateways are the devices on which the MVPN infrastructure (often tightly integrated with the wireless data network) is built. Architecturally, in both wireline and wireless systems, VPN gateways, together with other networking elements such as firewalls, are located on the border between a public network (that is, the MVPN service provider network, or an ISP network supporting connectivity to the MVPN service provider network, such as in the case of CPE VPN gateway or CPE HA) and the MVPN customer networks. The MVPN gateway must also support some mobility scheme when it is collocated with a wireless data platform, thus creating complex multitiered networking environments.
MVPN Gateway Implementation
The main task of an MVPN gateway is to ensure safe and secure transmission of the user data between mobile VPN clients and the destinations within stationary (virtual) private networks. This is usually achieved by selecting a robust hardware platform and implementing tunneling, access control, authentication, security, and other functions such as routing and various policy decision and enforcement mechanisms. Unlike MVPN clients, which usually support a limited set of these technologies, the MVPN gateway must be designed for versatility and hence support a variety of networking technologies and possibly different VPN client types (Figure 8.2).
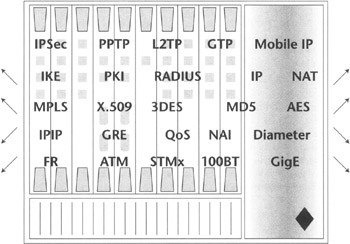 Figure 8.2: MVPN gateway functions.
Figure 8.2: MVPN gateway functions.
MVPN gateways must be able to authenticate mobile users via multiple authentication mechanisms and interface to AAA servers via AAA protocol client such as a RADIUS client, terminate tunnels originated by MVPN clients (in voluntary VPN case), or by the wireless infrastructure nodes (such as Mobile IP capable PDSN), and establish secure communications channels by providing constant user data integrity and confidentiality protection. MVPN gateways must also support a variety of static and dynamic IP address assignment techniques, actually assuming the role of the network access server, and must perform additional tasks associated with tunnel termination and origination.
Like MVPN clients, MVPN gateways can be implemented in both hardware and software on a dedicated platform, or they can be combined with existing devices performing other tasks within a network, such as servers, routers, wireless data network element platforms, or combinations of these. As a result, often the nontrivial duties assigned to a typical MVPN gateway must be accompanied by the capability to handle routing and forwarding, buffer management, packet scheduling support, packet marking and metering, accounting and performance monitoring, lawful interception, various data mobility schemes, and other typical wireless data networking functionalities. Such a variety of functionality has positioned network devices known as IP services switches (more on this in the next section) as the platform of choice in the carrier environment to support MVPNs, in part because of the service richness they can provide. Typically they not only support VPN termination, but also subscriber management, user services customization, firewalls, NAT, customer network access link termination, customer self-provisioning, and monitoring capabilities.
| Note |
The downside of this feature richness is the potentially high cost of such devices, some of which have already been implemented by a number of vendors. However, the cost of the device may be often balanced by its flexibility and revenue generation potential. |
Both dedicated and collocated MVPN gateway implementations can be native, where VPN gateway functionality is integrated with the platform operating system and often the hardware, or bump-in-wire, analogous to bump-in-stack implementation of MVPN clients, where a VPN gateway implemented on a dedicated platform is collocated with a router and attached to it via a physical interface. The specific case of devices combining MVPN gateway and wireless data platform functionalities deserves a bit more detailed evaluation, since we expect that this type of equipment has a good to chance to become a dominant way to implement MVPN gateways.
MVPN Gateways and Wireless Data Platforms
Before examining the MVPN gateway/wireless data platform combinations, we need to analyze the main types of wireless data platforms, their characteristics, and their suitability to VPN gateway functionality support. This analysis will be brief, however, mainly because the detailed discussion of modern router, IP switch, or an emerging class of wireless packet data platforms, for that matter, might easily evolve into not one but a series of books.
Wireless data platforms can be implemented in a variety of ways. The wireless data platform implementations can be roughly classified in two major types:
-
Router or IP switch-based
-
Server or general-purpose computer-based
Each has different properties as well as unique advantages and constraints. Servers are general-purpose computers optimized for serving the needs of a network or a group of users rather than a single user. Routers are in fact special-purpose computers optimized to forward data packets from one physical interface to another.
We must admit however, that the distinction between these two approaches is very fuzzy and has become even more blurred in the last few years. One way to clarify the distinction is to look at the platform operating system rather than its hardware. Traditionally, routers and IP switches were implemented based on specially designed real-time operating systems (RTOSs), such as VxWorks produced by Wind River systems, while servers relied on general-purpose non-RTOSs, such as UNIX, Linux, Windows NT, and Solaris OS. This approach, however, recently also became less applicable because of newly introduced dedicated routing platforms for wireless data and other types of networking relying on non-RTOSs, which have been simplified and made to conform to RTOS requirements (such as Starent ST16 wireless data platform, based on the generic Linux operating systems) and general-purpose computing systems based on PSOS and other RTOSs. [1] Other examples include vendors introducing complex routing and tunneling devices based on clusters of generic, often off-the-shelf computing systems (such as the now-defunct Cambia Networks, which developed PDSN, GGSN, and HA based on off-the-shelf Linux server produced by IBM), as well as dedicated router designs equipped to support functions such as firewalling and application layer processing, traditionally performed by servers.
Despite these difficulties in classifying wireless data platforms, most of them can still be defined—if increasingly loosely—and segmented into two classes, allowing us to analyze the pros and cons of each:
-
Server-based wireless data platforms are based on generic computing hardware and operating systems originally designed to support a variety of general computing tasks and applications, software-enhanced to support networking tasks such as packet forwarding or routing, tunneling, and AAA functions.
-
Router/IP switch-based wireless data platforms are based on hardware and software dedicated to performing a variety of networking functions (residing on the lower four OSI layers: physical through transport). Architecture of such platforms is usually optimized for packet data handling and forwarding or switching and tunneling and is not normally intended to support any applications outside of data networking.
Both of these platform types have certain advantages and constraints when used in wireless core networks to support a variety of tasks including MVPN. Let's consider these two types, along with several subtypes, in more detail.
General-Purpose Computing Platforms
Computer systems designed to perform a variety of tasks rarely excel in a particular one, forwarding or encapsulation of data packets being no exception. Most computer systems are designed to meet general market requirements and maximize their computing performance, while staying under budget both financially and technically in terms of system resource allocation.
For example, computing platforms optimized to run OSs like UNIX and Linux have been designed for data processing and general computing tasks, with resource allocation strategy not optimized for such tasks as routing, PPP termination, and especially encryption, compression, packet fragmentation and reassembly, and tunneling and tunnel switching. The memory hierarchy of a typical computer designed to run UNIX OS or its siblings, such as SUN SPARCstations, relies heavily on caches or virtual memory residing in nonvolatile memory, such as hard drives and other types of relatively slow-access mechanical devices. While cost-effective and suitable for general computing tasks, this approach often is not the most reliable, since mechanical devices are more prone to failure, nor is it optimal for running mission-critical applications such as routing that require frequent fast local memory pages.
Then there is Input/Output (I/O). In general computer systems, the I/O is a necessary evil often looked down upon by designers. In contrast to routers and other networking devices designed to deliver packets from one interface to another, I/O interfaces are what all the hard work is being done for.
| Note |
These and many other problems with UNIX-like operating systems in part stem from the fact that their network layers were originally designed for low-speed protocols such as SLIP, which used to be mainstream decades ago, and not for today's high-speed technologies and large-scale packet encapsulation and forwarding. |
When introduced to the task of handling complex wireless packet data functions entailing routing, switching, and encapsulation, such devices' packet forwarding and throughput constraints would not allow for efficient functioning in high-performance networks often spanning continents and hundreds of thousands of subscribers. Moreover, rather limited interface support options as well as inflexibility of hardware design, which often disallows hardware-based packet processing and other functions such as compression and encapsulation typically required by wireless packet data systems such as GPRS and CDMA2000, make these solutions only suitable for proof of concept, trials, and initial rollout stages of commercial deployments. In such small-scale deployments, however, these platforms often make sense, offering cost-effective alternatives to bringing purpose-built and therefore expensive routing devices in unproven and therefore high-risk markets.
Routers and IP Switches
The first breed of computers optimized for packet forwarding, named routers, was introduced by Cisco Systems in the late 1970s. The router was conceived to address the problems associated with generic computers when applied to networking tasks by creating specialized hardware often combined with real-time OSs optimized for data packet forwarding and other networking functions. Introduction of routers was a significant step forward for telecommunications and marked the beginning of a multibillion-dollar industry now known as data networking. Today routers come in many shapes and sizes, with different specializations and even under different names, such as an "IP switch" or a "network appliance." Not surprisingly, the majority of the successful wireless data platforms, while often based on specialized architectures, are still built around the familiar routing engines.
Originally, routers were designed to dynamically communicate with large numbers of networks via a limited number of links. As data networking technology progressed, to accommodate for the support for new functions such as subscriber access link termination, deep packet lookup, and, later, VPN functions and wireless data services, modifications to the original routing concept were needed. For instance, remote access servers (RASs) were introduced to handle subscriber termination, and IP switches were introduced to handle VPNs and other advanced data services such as labeling at the edge of MPLS networks, NAT, firewalling, and IPSec and tunnel switching. The latest wireless data platforms tend to be based on traditional routers, RAS devices, IP switches—all of which have their own advantages and limitations regarding mobility business and technologies like MVPN. Later in this section we will devote some attention to each of these.
To qualify for support of wireless packet data services in general, in addition to its traditional ability to efficiently forward packets, a routing platform must satisfy certain requirements:
-
The ability to terminate subscriber traffic
-
The ability to encapsulate subscriber traffic on a large scale with minimum delay
-
A full set of carrier class features suitable for the Central Office environment
-
Support for significant volatile local memory, such as dynamic random access memory (DRAM) resources and fast memory paging
-
Support for wireless system-specific signaling and logical interfaces
-
Support for QoS technologies such as DiffServ
-
Support for packet data mobility schemes such as GPRS and Mobile IP
In addition to these requirements, a wireless data platform aspiring to become an MVPN gateway must also support the following:
-
Dynamic tunnel switching (see Chapter 5)
-
Multiple tunneling protocols (see Chapter 2)
-
Dynamic policy provisioning (COPS, LDAP; see Chapter 5)
-
Encryption, compression, and AAA client
In the carrier environment, the wireless data platform must also support the following:
-
A variety of I/O modules to interconnect the device to the mobile network and to customer networks.
-
Ability to interface with a large number of customers' networks supporting overlapping private IP address space, as well as multiple virtual routing tables or full-blown virtual routers customers may manage.
-
High availability and other carrier-class features.
Traditional Routers
No doubt, traditional routers are more appropriate in this environment than generic computer systems, since efficient routing is, of course, their strong point. Carrier class features can be easily added by designing a robust chassis with various redundancy mechanisms. Tunneling and labeling capabilities can also be achieved in both hardware (for example, by designing new "encryption accelerator" cards) and software (by optimizing protocol stacks). Tunnel switching and scalable subscriber termination might, however, create certain problems and prompt significant architectural changes, which might potentially cause the router to evolve into something else, like an RAS or an IP switch. Mainly for these reasons, classic routers, when used as wireless data platforms and MVPN gateways, often suffer from low scalability and a lack of essential features. IP service switches or advanced edge routers utilizing virtual routers (see Chapter 5), network processors, and other advanced techniques are likely to be more suitable for the task of supporting MVPNs in carrier environments.
Remote Access Servers
Remote access servers were originally introduced by companies like Livingston, Ascend Communications (both acquired by Lucent), and 3Com (now CommWorks after the spin-off) to address the need to terminate large quantities of dial-up subscribers using such link layer protocols as PPP and Serial Line Internet Protocol (SLIP). RAS is a combination of a routing engine and modem banks (often implemented as a farm of Digital Signal Processor, or DSP, chips), software-optimized for subscriber termination, and additional memory necessary to store PPP state information. Architecturally, RAS is used to terminate subscribers accessing a private network or the Internet and aggregate high numbers of low-speed dial-up communications sessions or ISDN calls established over a PSTN into time slots on a small number of high-speed interfaces such as T1s or T3s. While quite appropriate for wireless circuit data systems based on dial-up connections (CommWorks' Total Control chassis is a popular example), RAS might be less well suited for wireless packet data systems and MVPN support mostly because of its already high complexity and cost and hard limit on the number of subscriber sessions (usually a few thousand) and session bandwidth.
IP Switches
IP switches, a new breed of routing device, are based on a routing engine or a cluster of routing engines and specifically designed for scalable packet subscriber termination, via DSL or cable modem, and encapsulation, as well as other tasks beyond the capabilities of traditional routers or RASs. The recent examples of successful IP switches include Shasta 5000 from Nortel Networks and Springtide 7000 wireless from Lucent Technologies. The physical interfaces of the IP switches can be shared by a high number of subscriber sessions, which can be scaled up and down with the interface bandwidth to the desired amount of memory and processing power for the routing engines and network processors. Tunneling and processing the intensive tunnel-switching capabilities of IP switches are usually supported in hardware for higher efficiency. The combination of these features, originally developed to address the requirements for scalable VPN support, is well applicable to the support of both wireless packet data and MVPN functions, making IP switches the best candidate MVPN platform.
[1]An interesting example of the latter is an infamous first-generation unmanned Mars Pathfinder rover launched by NASA in 1997 (for further information on this unique vehicle, see http://mars.jpl.nasa.gov/default.html and http://nssdc.gsfc.nasa.gov/planetary/mesur.html).







