Switched LAN Network Designs
A good switched networking solution combines the benefits of routers and switches in every part of the network, as well as offering a flexible path to grow from shared-media to switched networks.
In general, incorporating switches in campus network designs results in the following benefits:
High bandwidth? The more network bandwidth available to your users, the faster they can work, or surf the Internet. Think of a four-lane highway that enables more cars to travel than a two-lane road.
Quality of service (QoS)? This is a traffic-prioritization scheme used to ensure that delay-sensitive traffic such as voice and video is given a higher priority on the network than other types of traffic that are relatively immune to delay or changes in delay times (jitter). Often a percentage of the bandwidth is reserved for high-priority traffic, so when that type of traffic is present on the network it gets its own lane; when there is no high-priority traffic, however, all the bandwidth can be used by normal traffic. This is just like an airline ticket counter where one of the six lines is reserved for first-class passengers. The first-class passengers get a dedicated line; if there are no first-class passengers in line, however, the agent handling first class processes coach passengers.
Low cost? Here is one of the mantras in the network community, quoted from RFC 1925, "The Twelve Networking Truths" by Ross Callon at http://www.faqsorg/rfcs/rfc1925.html: "Good, fast, cheap: Pick any two (you can't have all three)." Many times this is correct, but one truth is always evident to a network designer, engineer, or manager: Don't spend more money than necessary.
Easy configuration? You know those "assembles in minutes" toys that don't? You do not want your network to suffer the same fate. Remember that if it is not easy to configure, it won't be easy to manage.
There are times when these solutions will not meet your requirements and some advanced network services will be required. Some of these advanced services are listed here; if you need any of these advanced networking services, then you are going to need routers in your network:
Firewalls? These devices provide a way to filter out unwanted network traffic, such as broadcasts, from the reaching beyond the local network segment into the rest of the network.
Communication between dissimilar LANs? If you have some users connected to an Ethernet network and some users connected to a Token Ring network, and you want these users to talk with each other, better get the router. This scenario is often seen when migrating from Token Ring to Ethernet.
Fast convergence? If a failure occurs in a switched network, it takes 50 seconds for the Spanning Tree Protocol to converge on the new change. Routers can run one or more of several routing protocols, which are used to build a network map, and depending upon the routing protocol used, the routers can converge on a change in the network in as little as 1 second. Bear in mind that 802.1d STP is 50 seconds without specialized features or enhancements. In other words, worst case, 50 seconds using 802.1d STP.
Security? Because routers look at the packets carried within the switched frames, you can specify that the router block traffic from certain source or destination network addresses. You can also configure the router to block all traffic from any networks to which you've not established permission to communicate, keeping potential network intruders out of your network. This is similar to requiring your network traffic to present a permission slip before it can continue on its field trip through your network.
Redundancy? If one link fails, the router can determine what, if any, other links are available that provide a path from source to destination, similar to a construction worker redirecting traffic around a pothole repair. Redundancy is accomplished with the implementation of the Spanning Tree Protocol defined by IEEE 802.1d or the newer Rapid Spanning Tree Protocol (RSTP) defined by IEEE 802.1w.
Load balancing/sharing? Remember that in kindergarten you were taught that it's good to share? Well, the rule applies here, too, in the form of load balancing. If you have multiple links between your source and destination, a router can be used to share the traffic across all those links, which can lead to more cost-effective use of your network. (Sharing is still a good thing.)
Switching and bridging sometimes result in the less-than-optimal path of network traffic because every frame and packet must go through the root bridge of the spanning tree if the source and destination nodes are on different branches of the spanning tree. When routers are used in your network, the routing of packets can be controlled and designed for the optimal path, providing "the quickest way out of town" for your data to get to where it needs to go (the destination network).
When designing switched LAN networks, consider the following, each discussed in more detail in the following sections:
Comparison of LAN switches and routers
Benefits of LAN switches in a network
Benefits of routers in a network
Benefits of VLANs and VLAN implementation in a network
General network design principles
Switched LAN network design principles
Routers and LAN Switches
The fundamental difference between a LAN switch and a router is that the LAN switch operates at Layer 2 of the OSI model and the router operates at Layer 3. It is this difference between routers and switches that affects the way that LAN switches and routers respond to network traffic. This section compares LAN switches and routers with regard to the following network design issues:
Loops
Convergence
Broadcasts
Subnetworking
Security
Media dependence
note
Switches implement Layer 2 functionality, and routers implement Layer 3 functionality. Because switches are beginning to implement Layer 3 functionality, in the form of multilayer switching, however, the functions of a LAN switch and a router are merging. |
Loops
Layer 2-switched LAN topologies are vulnerable to loops, because the network is a flat network, as shown in Figure 10-12.
Figure 10-12. Layer 2 Loop
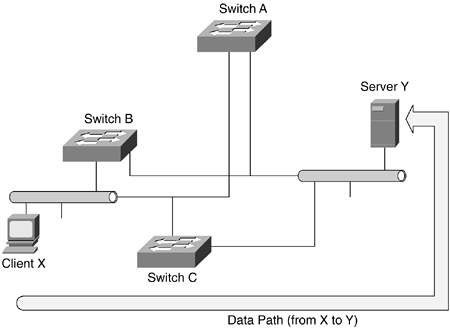
In Figure 10-12, it is possible for frames from Client X to be switched by Switch A and then for Switch B to put the same frame back on to the same LAN from where it originated. In this situation, frames loop and suffer multiple replications. To prevent this looping and replication, topologies that contain loops need to run the Spanning Tree Protocol. As discussed in Chapter 7, STP uses the spanning-tree algorithm to build topologies that do not contain loops.
note
A router can also support this design because the router would contain the broadcasts and bridge protocol data units (BPDUs) within each LAN segment. |
Convergence
In transparent switching, neighboring switches make topology decisions locally based on the exchange of BPDUs. This method of making topology decisions means that converging on an alternative path can take an order of magnitude, measured in seconds, longer than in a routed environment, measured in fractions of seconds.
In a routed environment, routing protocols such as Open Shortest Path First (OSPF) maintain topological databases, or route maps, of the network, enabling the network to converge quickly in response to a change in the network topology, such as a link failure or the addition of a new network device.
Broadcasts
LAN switches do not filter broadcasts, multicasts, or unknown address frames. This lack of filtering might be a severe problem in distributed networks, which many networks are today, in which broadcast messages are used to resolve data link layer and network layer addresses and dynamically discover network resources, such as file and print servers. Broadcasts originating from each network segment are received by every computer in the switched network. Even though most network devices discard broadcasts because they are irrelevant to that device, large amounts of network bandwidth are consumed by these broadcasts. Broadcasts limit the amount of bandwidth that can be used for user data.
In some cases, the circulation of broadcasts around the network can saturate the network to the point that no bandwidth remains for application data. Imagine a roomful of people shouting for attention and leaving no "air" for a conversation between two people.
This is a situation known as a broadcast storm. The problem is that new network connections cannot be established, and existing connections might be dropped. The probability of broadcast storms increases with each additional device added to the switched network. Broadcast storms are often caused by loops in the Layer 2 network and can shut down an entire network in seconds.
note
A broadcast storm is the excessive transmission of broadcast traffic within a network segment. Because routers do not forward broadcasts, routers are not subject to broadcast storms. |
Subnetting
Switched networks are composed of physically separate segments, but are logically considered to be one large network, such as one Internet Protocol (IP) subnet, similar to grouping blocks of phone numbers together that share the same area code or exchange.
Because LAN switches operate at the data link layer (OSI Layer 2), the switches provide connectivity to the network hosts and behave as if each host were on the same cable, regardless of the logical network to which the host belongs.
note
|
Because routers operate at OSI Layer 3, they can create hierarchical addressing structures. Routed networks associate a logical addressing structure to a physical infrastructure so that each network segment has, for example, a Transmission Control Protocol/Internet Protocol (TCP/IP) subnetwork (subnet). Traffic flow on routed networks differs from traffic flow on switched networks because routed networks have more flexible traffic flow. The traffic flow in a routed network is more flexible because routers use the hierarchy in determining the optimal path based on dynamic factors such as network congestion.
note
Routers route traffic to a destination network, not to the destination host. The router's job is to get the traffic to the destination network and let the receiving LAN determine who the host recipient is. |
Security
Routers and switches each have features available that can be used to create more-secure networks. LAN switches might use custom filters providing access control to the network based on the source or destination address, the protocol type, frame or packet length, or certain bits within the frame. Routers might filter on logical source or destination network addresses and provide access control to the network based on the options available within the Layer 3 protocol being used, such as IP. For example, routers can be used to permit or deny traffic based on specific TCP/IP information for a range of network addresses, such as preventing a group of users from accessing file-sharing websites.
note
All currently shipping Cisco switches and most enterprise switch vendors have Layer 3 filtering capabilities, even in their respective Layer 2 switch product lines. |
Media Dependence
Two factors need to be considered with regard to mixed-media networks, such as Ethernet and Token Ring: the maximum transmission unit (MTU) and the addressing scheme in the different networks.
The first factor that needs to be considered regarding mixed-media networks is that the MTU differs for various network media. Table 10-1 lists the minimum and maximum frame sizes for Token Ring and Ethernet network media.
Medium | Minimum Valid Frame Size | Maximum Valid Frame Size (MTU) |
|---|---|---|
Ethernet | 64 bytes | 1518 bytes |
Fast Ethernet | 64 bytes | 1518 bytes |
Gigabit Ethernet (a.k.a. "Jumbo Ethernet") | 64 bytes | 9000 bytes |
Token Ring | 32 bytes | 16 KB |
When LANs of different media types are switched, such as between an Ethernet network and a Token Ring network, hosts must use the MTU that is the lowest common denominator of the switched LANs that make up the network. For example, look at the network in Figure 10-13.
Figure 10-13. Token Ring and Ethernet Switched Network
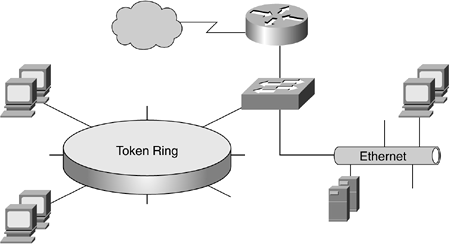
In this network, the switch recognizes that the maximum sized that can be accommodated is the 1518 bytes (1.518 kilobytes [KB]) of the Ethernet segment. If the switch allows a larger MTU, such as a 4-KB frame from the Token Ring segment, to traverse the Ethernet segment, the Ethernet segment will recognize the frame as a "giant" and discard the frame as invalid. The same holds true if a Token Ring network host sends a frame that is smaller than the minimum frame size of 64 bytes for Ethernet; however, in this case, the Ethernet segment will discard the frame as a "runt" because it is too small to be recognized as a valid frame.
This lowest common denominator requirement limits throughput and can compromise performance over a relatively fast link, such as the 100 Mbps of Fast Ethernet. Most network (OSI Layer 3) protocols can fragment, or break apart, and reassemble packets that are too large for a particular network, so networks connected with routers can accommodate the different MTU sizes, which maximizes throughput. An important consideration to remember here is high-speed routers use special hardware to route frames, which often limits the fragmenting and reassembling of packets.
The second factor that needs to be considered regarding mixed-media networks is that because switches operate at Layer 2, these switches must use a translation function to switch between different media. The translation function can result in serious problems such as converting the MAC (hardware) address from Token Ring to Ethernet. One issue with moving data from a Token Ring to an Ethernet network is the Layer 2 addressing; Token Ring network devices read the Layer 2 MAC address from left to right, whereas Ethernet network devices read the Layer 2 MAC address from right to left.
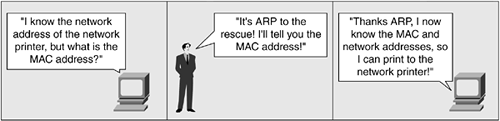
Because routers work at Layer 3, routers are independent of the properties of any physical media. Furthermore, because routers work at Layer 3, they can use a simple address-resolution protocol resolving differences between Layer 2 and Layer 3 addresses. An example of an address-resolution protocol is IP's Address Resolution Protocol (ARP), which can determine the Layer 2 address if you have the Layer 3 address, as illustrated in Figure 10-14.
Figure 10-14. The Adventures of ARP
note
Whereas ARP is used in IP to determine the Layer 2 (data link) address if you know the Layer 3 (network) address, Reverse ARP (RARP) does the opposite; if you know the Layer 2 address, Inverse ARP (InARP) or RARP can give you the Layer 3 address. RARP is the more common term used when discussing reverse address resolution. |






