VLAN-Based Network Attacks
The majority of Layer 2 (data link layer) attacks exploit the inability of a switch to track an attacker, because the switch has no inherent mechanism to detect that an attack is occurring. This inability to detect an attacker means that this same attacker can perform malicious acts against the network path, altering the path and exploiting the change without detection.
note
Some of the newer switches introduced to the market can track network attackers with the implementation of firewall and IDS modules or Cisco Network-Based Application Recognition (NBAR). Firewalls are used to prevent unauthorized access to your network, and IDS sensors are used to track network attack and intrusion attempts. Cisco NBAR adds intelligent network classification to network infrastructures by using a classification engine that recognizes a wide variety of applications, including web-based applications. |
Some of the most common Layer 2 attacks are as follows:
MAC flooding attack
Address Resolution Protocol (ARP) attacks
Private VLAN attack
Multicast brute-force attack
Spanning-tree attack
Random frame stress attack
Each of these attacks is discussed in detail in the following sections.
MACFlooding Attack
A MAC flooding attack is not a network attack but more a limitation of the way switches and bridges work. Switches and bridges possess a finite hardware-learning table to store the source addresses of all received packets. When this table becomes full, traffic directed to addresses that cannot be learned anymore is permanently flooded. Traffic flooding is constrained within the VLAN of origin, and therefore no VLAN hopping is permitted.
On nonintelligent switches, this flooding problem arises because a sender's Layer 2 identity is not verified, and therefore the sender can impersonate an unlimited number of network devices by counterfeiting frames.
Port security, 802.1x, and dynamic VLANs are three features that you can use to limit a device's connectivity based on its user's login ID and the device's own MAC layer identification. With port security, for example, preventing MAC flooding attacks is as simple as limiting the number of MAC addresses that can be used by a single port. By using port security in this way, you tie the identification of the device's traffic to its port of origin. Dynamic VLANS enable you to dynamically assign switch ports to VLANs based on the Media Access Control (MAC) address of the device connected to the port. When you move a host from one switch port to another switch port in the network, that switch dynamically assigns the new port to the assigned VLAN for that device.
ARP Attacks
Address Resolution Protocol (ARP) is an old protocol and was developed back in the time when everyone in a network was supposed to be friendly. Because ARP was designed for a friendly environment, no security was built in to the ARP function. As a consequence, anyone can claim to be the owner of any IP address he likes. In other words, an attacker can say that his MAC address is associated to any IP address in your network. These false claims result from the fact that ARP requests and replies carry information that associates the MAC address with the IP address of a device. Because there is no way to verify these identities, anyone trying to break into your network can pretend to be someone else, such as a legitimate user of your network, and gain access to resources on your network, such as a corporate database.
ARP attacks are targeted to fool a switch into forwarding packets to a device in a different VLAN by sending ARP packets containing forged identities. Within the same VLAN, ARP attacks, also known as ARP poisoning, can fool network end nodes, such as workstations or routers, into learning these false identities. These counterfeited identities enable a malicious user to pretend to the network that she is an intermediary between two endpoints and perform a man-in-the-middle (MiM) attack, as illustrated in Figure 9-5.
Figure 9-5. ARP Spoofing Attack
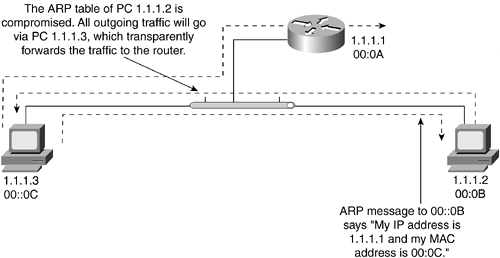
The man-in-the-middle attack occurs when one network device impersonates another network device, such as your default gateway. The attacker uses the ARP packets sent to the device targeted for attack because these ARP packets are not verified by the receiver. These ARP packets poison the receiver's ARP table with forged information, injecting the attacker into your network. This attack is similar to identity theft, in which someone obtains a piece of information related to your identity and uses that information to gather more information about you. Eventually, the pretender can convince everyone he is you.
Man-in-the-middle attacks can be prevented either by blocking direct Layer 2 communication between the attacker and the attacked device or by embedding intelligence into your network, such as a Layer 3 device that can check forwarded ARP packets for identity correctness.
Private VLAN Attack
Private VLANs allow traffic to be further segmented at Layer 2, limiting the size of your broadcast domain. A private VLAN attack uses the expected behavior of a private VLAN against the VLAN itself. Private VLANs are a Layer 2 feature that is supposed to restrict traffic to Layer 2. However, recall that a router is a Layer 3 device and as such, when the router is connected to the promiscuous port of a private VLAN, the switch forwards all Layer 3 traffic received on that port to whatever destination is identified. This forwarding occurs even if the destination is in the same local network as the source, as illustrated in Figure 9-6.
Figure 9-6. Private VLAN Attack
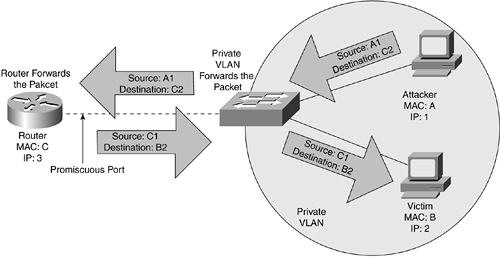
note
Configuring access control lists (ACLs) on the router is a way to prevent private VLAN attacks. |
It is normal for two hosts in an isolated VLAN to fail in communicating with each other through direct Layer 2 communication but instead succeed in talking to each other using the router as a packet relay. As it is with regular routed traffic, packets relayed through a Layer 2 proxy can be filtered, if desired, by an appropriately configured ACL on the forwarding device.
Multicast Brute-Force Attack
Multicast brute-force attacks exploit the potential vulnerability of a switch to a storm of multicast frames. When a switch receives a significant amount of Layer 2 multicast traffic (frames) in rapid succession, the switch should limit the traffic to its original VLAN; failing to do so would leak frames to other VLANs if there is a routing mechanism in place between the VLANs.
This type of attack often proves ineffective against switches because switches should contain all the frames within their appropriate broadcast domain.
Spanning-Tree Attack
Another attack that can leverage switch vulnerability is the spanning-tree attack. Recall from Chapter 7, "Spanning Tree Protocol (STP)," that by default STP is turned on and every port on the switch both talks and listens for STP messages on the network. The spanning-tree attack consists of sniffing the network STP frames on the wire and getting the ID of the port on which STP was transmitting.
When the attacker has this port ID information, she can begin sending out STP Configuration/Topology Change Acknowledgement BPDUs (bridge protocol data units) announcing that she (the attacker) is the new root bridge with a much lower priority. This enables the attacker to listen in on all the network traffic and possibly change traffic flow.
Random Frame-Stress Attack
Random frame-stress attacks can have many incarnations but in general this attack is a brute-force attack, randomly varying several fields of a packet and leaving only the source and destination addresses untouched.
Private VLANs can be used to better isolate hosts at Layer 2 and protect these hosts from unwanted or malicious traffic from untrustworthy devices. Communities of mutually trusting hosts can be created so that a Layer 2 network can be divided into smaller Layer 2 networks where only friendly devices are permitted to communicate with each other.






