Office Mode
An important enhancement to SecureClient is Office Mode, which allows you to assign your remote access client an IP address, DNS, and WINS information as if the client were on the local network. To understand why this is a big step forward, a bit of history is in order.
Before Office Mode
In FireWall-1 4.1, a VPN client initiates a connection to the encryption domain simply by attempting to access the encryption domain. It is "transparent" in the sense that no interaction with the SecuRemote application is required to bring up the VPN. Once the VPN is established, the client may communicate with the encryption domain. Packets appear to be sourced from the client's IP address. If the client is sitting behind a NAT device, this is the client's nonroutable IP address. This creates a number of problems.
IP address conflicts: What happens when two or more VPN clients use the same private address space? With a number of NAT router vendors choosing 192.168.0.x as their internal DHCP address range and most of them assigning 192.168.0.2 first, you end up with a lot of clients using the same address. The firewall doesn't deal with this very well and drops clients. What about when the 192.168.0.x network is used in your encryption domain? SecuRemote doesn't work in this configuration.
Asymmetric routing: In particularly large networks that span multiple sites, there may be more than one way out of the internal network depending on where you are. As a result, you might come in one gateway and go out the other. Most firewalls don't cope very well with asymmetric routing, even when VPN access is not involved. In a VPN situation, it is vital to enter and exit the same set of firewalls. IP Pool NAT attempts to resolve this problem but breaks applications that aren't NAT friendly.
Routing of Internet addresses in the internal network: For a variety of reasons, it is not always desirable to allow Internet IP addresses on the internal network. It becomes especially difficult when trying to perform access control on items within the network. IP Pool NAT partially helps, but again, it is subject to the limitations of NAT.
Lack of integration with dial-up networking: In some instances, it is useful to allow a VPN connection only when dialed up to the Internet. In FireWall-1 4.1, there was no way to cleanly bring up dial-up networking and the VPN connection simultaneously.
Disconnection from the encryption domain: In a Transparent mode configuration, the only way to "log out" of a site (i.e., to prevent the client from sending encrypted packets to the encryption domain) is to disable or remove the site from the configuration.
Use of SecuRemote from within the encryption domain: You might want to use SecuRemote to always talk to a firewall, regardless of whether or not you are in the internal network. Furthermore, your client might be using IP address space your encryption domain contains. SecureClient 4.1 and earlier did not work in this configuration.
At the end of the day, VPN access was more problematic for many people than dialing in.
What Office Mode Does
Office Mode provides solutions to all of these issues.
Connect Mode: The client now provides a new way to initiate a VPN connection. Connect Mode acts a bit like dial-up networking?the interface is even similar. You must explicitly tell SecureClient to connect to the VPN domain. As part of that process, you can specify which dial-up networking connection to bring up as well. You can also disconnect from the VPN domain easily.
Client IP addresses assigned on authentication: In Office Mode, the firewall assigns the client an IP address. The administrator can choose which IP addresses the firewall will assign or choose to obtain the IP address via an internal DHCP server. The client uses one of these IP addresses for all communications to the encryption domain, which will be assigned to a virtual adapter that appears in your Windows configuration. This eliminates problems with external addresses on the internal network as well as with NAT.
No client IP address conflicts: Because the client is assigned a unique IP during the initial IKE negotiation, the client's local IP address can be almost anything it needs to be. The various types of IP address conflicts discussed earlier are essentially eliminated. There are a few cases where you will still have issues, for example, with clients located directly behind the gateway.
No asymmetric routing: Each gateway has a unique set of client IP addresses associated with it. Internal routing should be set up so that these IPs will route to the appropriate gateway.
These Office Mode features make a client-based VPN much easier to deploy on a wide scale.
Configuring Office Mode
In NG AI, Office Mode is configured in the gateway object in the Remote Access Office Mode frame, as shown in Figure 12.25. In NG FP3 and earlier, it is in the gateway object's Office Mode frame (under Remote Access).
Figure 12.25. Gateway Properties, Office Mode frame
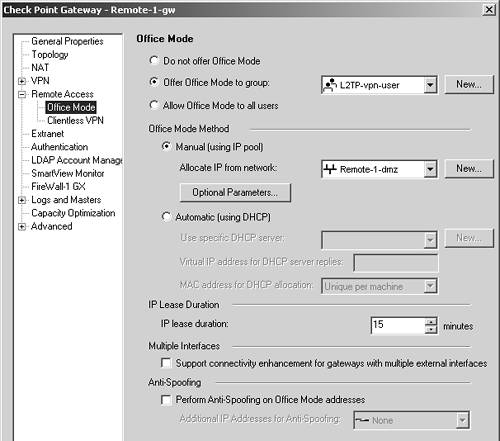
The settings here are described below.
Do not offer Office Mode: Do not use Office Mode. All properties on this page will be disabled if you select this option because Office Mode will not be used.
Offer Office Mode to group/Allow Office Mode to all users: You can allow Office Mode as a choice either for a specific group of users or for all users. Note that this doesn't require users to use Office Mode. However, your particular network configuration might make Office Mode the only thing that actually works.
Office Mode Method, Manual: This option tells FireWall-1 to automatically assign an IP address for a pool of IP addresses. In the optional parameters, you can define up to three DNS servers, three WINS servers, and the DNS domain of your client. In NG FP3 and before, ensure that the IP address space chosen is outside of your encryption domain.
Office Mode Method, Automatic: This option tells FireWall-1 to send a request to an internal DHCP server to obtain configuration information. You need to tell FireWall-1 which DHCP server to forward the request to and an IP address to originate the requests from. The DHCP server uses this IP address as a "hint" to determine which subnet to allocate IP addresses from. As with the previous method, ensure that the IP addresses assigned by the DHCP server are outside of your encryption domain. In NG AI, you can also specify how the MAC address will be generated to be used as part of the DHCP request. The routing on your internal network should ensure packets destined for this IP address get routed to the firewall.
IP Lease Duration: When FireWall-1 allocates a client to an IP, this is how long that IP should be given to a particular client unless the client requests that it be renewed. Provided there's a connection between the client and server, this should always be the case.
Support connectivity enhancement for gateways with multiple external interfaces: In NG AI, this checkbox might be better described as "Make Office Mode work with more than one external interface." This option affects performance, so check this box only if you have more than one external interface.
Perform Anti-Spoofing on Office Mode addresses: In NG AI, this option tells FireWall-1 to ensure that a packet that appears to be coming from an Office Mode address is really coming from a client operating in Office Mode. If address space is being allocated by a DHCP server, the address range(s) need to be specified in the Additional IP Addresses for Anti-Spoofing field.
Once you have made the appropriate configurations here, install the security policy. Now ensure that an explicit route for the chosen Office Mode network is specified on the gateway(s). This route will point to your "next hop" toward the Internet (i.e., the default route). Check Point suggests this route be added even if your routing table would normally route the packets that direction anyway. Other hosts and/or routers on the internal network need a similar route.
The Office Mode networks themselves won't really exist within your network, though for all intents and purposes, the networks exist within the firewall. Within your internal network, ensure that packets destined for these networks are routed to the firewall.
On the client side, you need to ensure that the client is installed in SecureClient mode and that Connect Mode is enabled. Right-click on the SecuRemote envelope icon and select Configure. From here, select Connect Mode from the Tools menu. If necessary, change the mode to Connect Mode, and restart the client. Select Stop VPN-1 SecureClient from the File menu. Then navigate to the Start menu, select Programs, then Check Point VPN-1 SecureClient, then SecureClient. This starts the client again.
Known Limitations of Office Mode
Office Mode has a few minor limitations.
There is no Windows 9x/ME support: Office Mode does not work on Windows 9x/ME platforms. Considering that Microsoft is ending support for these platforms in January 2004, it is unlikely Check Point will ever support this feature on these platforms.
One Office Mode client cannot connect to another prior to NG AI: Two client machines connected into the same firewall cannot communicate with one another through the VPN in NG FP3 and earlier. NG AI supports this functionality.
Office Mode also allocates an IP Pool NAT address: If you have IP Pool NAT configured, your Office Mode clients will also be allocated an IP Pool NAT address.






